SignatureCheckerLib.isValidSignatureNow will always return true if address(0) is an owner meaning malicious users can make arbitrary calls on an account, including in the current set up of the CoinbaseSmartWallet proxy implementation
#117
Labels
bug
Something isn't working
downgraded by judge
Judge downgraded the risk level of this issue
duplicate-90
grade-a
insufficient quality report
This report is not of sufficient quality
Q-10
QA (Quality Assurance)
Assets are not at risk. State handling, function incorrect as to spec, issues with clarity, syntax
🤖_90_group
AI based duplicate group recommendation
Lines of code
https://github.com/code-423n4/2024-03-coinbase/blob/main/src/SmartWallet/CoinbaseSmartWallet.sol#L104-L106
https://github.com/code-423n4/2024-03-coinbase/blob/main/src/SmartWallet/MultiOwnable.sol#L85
Vulnerability details
Impact
There are no checks in
MultiOwnable::addOwnerAddressto stop someone adding the zero address as an owner. While typically this would not be a significant issue, in the case of this codebase ifaddress(0)is an ownerCoinbaseSmartWallet::_validateSignaturewill always return true regardless of the signature ifSignatureWrapper.ownerIndexis the index of the zero address.This means that a malicious user would be able to use EntryPoint transactions to cause significant damage to a users account (steal funds, change owners, upgrade the proxy implementation).
This is currently the case in the
CoinbaseSmartWalletproxy implementation contract asaddress(0)is mistakenly added as an owner in an attempt to make the proxy implementation inoperable, but instead has the exact same effect. This would escalate the issue severity to critical if it were possible to do something such as upgrade the implementation contract's implementation, putting allCoinbaseSmartWalletinstances that use this implementation contract at risk.Proof of Concept
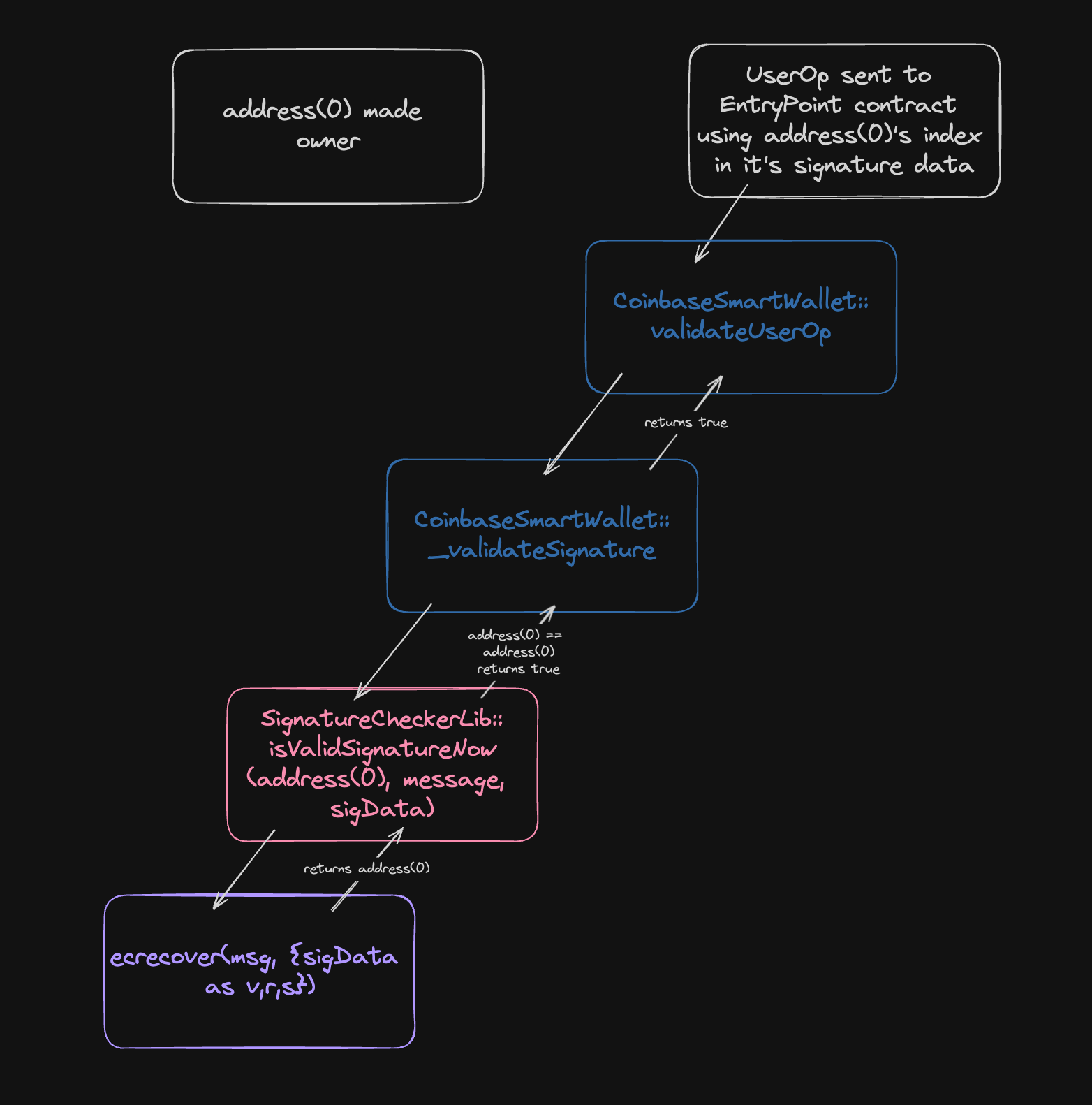
The following shows the control flow outlining how any instance where
address(0)is a viable owner will result in the signature being validated:Recommended Mitigation
Given the severity of the damage should the zero address be made an owner, and that the likelihood of the issue occurring is scaled up by the number of users using a
CoinbaseSmartWallet, the project should implement sufficientaddress(0)checks whenMultiOwnable::addOwnerAddressto protect their users from a potentially costly error.On top of this the
CoinbaseSmartWalletconstructor should not passaddress(0)as an owner when calling_initializeOwnersand should instead use another address such as "0x000000000000000000000000000000000000dEaD" top stop users being able to make arbitrary calls via the proxy implementation contract.Assessed type
Other
The text was updated successfully, but these errors were encountered: