New issue
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and privacy statement. We’ll occasionally send you account related emails.
Already on GitHub? Sign in to your account
AES with CipherMode.CFB and PaddingMode.PKCS7 incompatible between .NET Framework and .NET5.0 #46672
Comments
|
Tagging subscribers to this area: @bartonjs, @vcsjones, @krwq Issue DetailsDescriptionI have a .NET Framework 4.6.2 program that encrypt/decrypt files and I tried to use the same encrypt/decrypt methods for a .NET5.0 console application. The code (below) compiles and works on both systems, but if I try to decrypt a file that is encrypted by the other system it is not compatible. Encrypted with .NET Framework / Decrypted .NET Framework: Works fine. I expected that the code in .NET Framework and .NET5.0 results in the same behaviour, but their seems to be differences. Configuration.NET Framework 4.6.2 Windows 10, x86 Visual Studio 2019, V16.8.3 Regression?Don't know. CipherMode.CFB is supported from .NET5.0 and should not work in older versions. Other informationDecryption/Encryption Code Example:
|
|
Thanks for the repro. I'll take a look. |
|
Okay, there are a number of things that I am seeing. Starting with the first, it appears that using System;
using System.Security.Cryptography;
using var aes = new RijndaelManaged();
aes.Key = new byte[32];
aes.IV = new byte[16];
aes.Mode = CipherMode.CFB;
Console.WriteLine(aes.FeedbackSize); //Prints 128
byte[] input = System.Text.Encoding.UTF8.GetBytes("hello");
using var transform = aes.CreateEncryptor();
byte[] ciphertext = transform.TransformFinalBlock(input, 0, input.Length);
Console.WriteLine(ciphertext.Length); // Prints 6???Even though we are supposedly in CFB128 mode, the resulting ciphertext is 6. So 5 bytes of input and 1 byte of padding = 6. This may or may not be part of the issue at hand, but, it's something I've noticed that so far looks like incorrect behavior. This is because the Line 30 in 1cd5e42
But the Line 16 in 1cd5e42
|
|
In your .NET 5 code, if you replace: RijndaelManaged AES = new RijndaelManaged();with: Aes AES = Aes.Create();
AES.FeedbackSize = 128;I think things should be interoperable now. Can you please try that and let us know if that fixes it? |
|
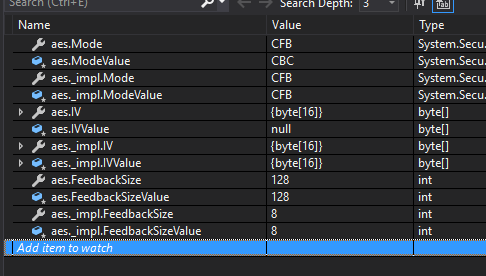
@bartonjs For .NET 5/6 the
|
|
@jakubbogacz Yeah, the protected fields in these classes are a little weird. However, since The fields there are just a byproduct of existing on |
|
This seems like Rijndael's version of #43234, where we decided "match Framework". |
Yeah. In addition to that, the |
I checked it and it works fine. Thank you @vcsjones @bartonjs and @jakubbogacz for the fast reply and your help. One last question: In which Version of .NET will the bugfix of RijndaelManaged published? .NET5.0.2 or .NET6.0? |
|
@korny86 the fix has been merged for 6.0. #46713 is to fix it for 5.0 - but it has not been approved by servicing yet. When / if it gets approved and merged for 5.0, we'll know what release it will be in. The solution I posted is the recommended way forward - the rijndael types exist for compatibility, but using the Aes factory method is the "correct" way in .NET Core and 5. |
|
@korny86 just to follow up on the 5.0 port, it looks like the fix landed in 5.0.3. |
Description
I have a .NET Framework 4.6.2 program that encrypt/decrypt files and I tried to use the same encrypt/decrypt methods for a .NET5.0 console application. The code (below) compiles and works on both systems, but if I try to decrypt a file that is encrypted by the other system it is not compatible.
Encrypted with .NET Framework / Decrypted .NET Framework: Works fine.
Encrypted with .NET5.0 / Decrypted .NET5.0: Works fine.
Encrypted with .NET Framework/ Decrypted .NET5.0: Exception “Padding is invalid and cannot be removed”
Encrypted with .NET5.0 / Decrypted .NET Framework: Exception “Length of the data to decrypt is invalid”
I expected that the code in .NET Framework and .NET5.0 results in the same behaviour, but their seems to be differences.
Are there any properties to make the .NET5.0 project compatible? (The .NET Framework program is already released 2 years ago and changing the algorithm on that side is a bigger issue.)
Configuration
.NET Framework 4.6.2
.NET5.0
Windows 10, x86
Visual Studio 2019, V16.8.3
Regression?
Don't know. CipherMode.CFB is supported from .NET5.0 and should not work in older versions.
Other information
Decryption/Encryption Code Example:
The text was updated successfully, but these errors were encountered: