New issue
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and privacy statement. We’ll occasionally send you account related emails.
Already on GitHub? Sign in to your account
[Fleet] Minor secrets UX improvements #171225
Comments
|
Pinging @elastic/fleet (Team:Fleet) |
|
Ping @zombieFox - this is the initial issue I was using to track these improvements. I'm going to make a few more tweaks over on the associated PR at #171405 and then provide some updated screenshots on the current state of things. If we want to spend some more time with this, I'll probably merge what we have so far in that PR and then create a follow-up issue to track incremental improvements to this UI. |
## Summary Closes #171225 - Highlights secrets during package policy creation with a distinct background and icon - Add tooltip + docs link for secrets where appropriate - Detect "new secrets" during policy upgrade and alert the user in a separate callout ## To do - [x] Fix any failing tests - [x] Add tests for "new secrets" detection logic ## Screenshots 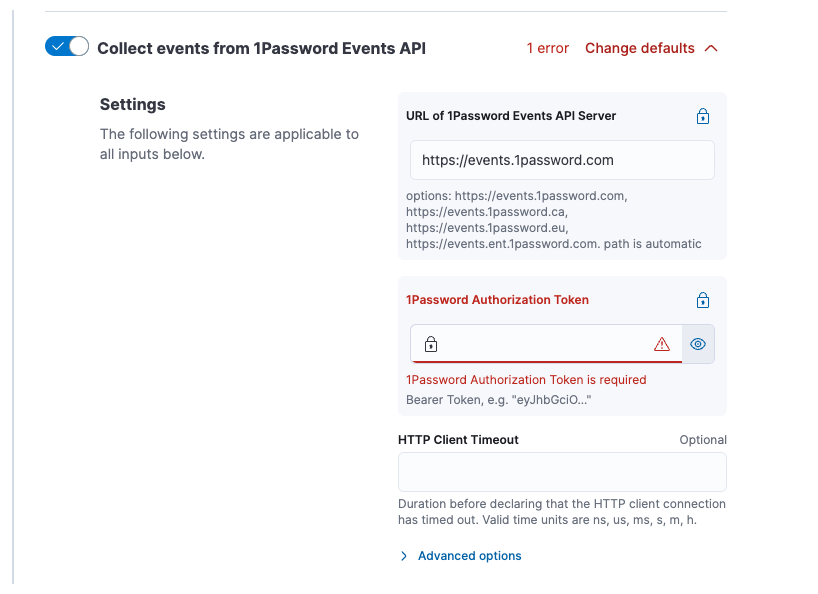   ## How to test There's probably an easier way to do this, but this is what I did 1. Clone https://github.com/elastic/package-registry and https://github.com/elastic/integrations 2. Add the following to `config.yml` in your package-registry repo ```yml package_paths: - path/to/your/integrations/build/packages ``` 3. Build a version of an integration with some `secrets: true` for various variables. I used `1password` ```shell cd integrations/packages/1password # Edit `manifest.yml` or a given `data_stream/*/manifest.yml` file to change some variables to `secret: true`. Also bump the version and update `changelog.yml` elastic-package build ``` 4. Run the local package registry e.g. ```shell cd package-registry go run . --feature-proxy-mode=true -proxy-to=https://epr.elastic.co # makes it so you can still see EPR packages in Kibana ``` 5. Update your `kibana.dev.yml` to point at your local package registry ```yml xpack.fleet.registryUrl: http://localhost:8080 ``` 6. Start Kibana and Elasticsearch and install, upgrade, etc your package in question to verify the changes --------- Co-authored-by: David Kilfoyle <41695641+kilfoyle@users.noreply.github.com>
## Summary Closes elastic#171225 - Highlights secrets during package policy creation with a distinct background and icon - Add tooltip + docs link for secrets where appropriate - Detect "new secrets" during policy upgrade and alert the user in a separate callout ## To do - [x] Fix any failing tests - [x] Add tests for "new secrets" detection logic ## Screenshots    ## How to test There's probably an easier way to do this, but this is what I did 1. Clone https://github.com/elastic/package-registry and https://github.com/elastic/integrations 2. Add the following to `config.yml` in your package-registry repo ```yml package_paths: - path/to/your/integrations/build/packages ``` 3. Build a version of an integration with some `secrets: true` for various variables. I used `1password` ```shell cd integrations/packages/1password # Edit `manifest.yml` or a given `data_stream/*/manifest.yml` file to change some variables to `secret: true`. Also bump the version and update `changelog.yml` elastic-package build ``` 4. Run the local package registry e.g. ```shell cd package-registry go run . --feature-proxy-mode=true -proxy-to=https://epr.elastic.co # makes it so you can still see EPR packages in Kibana ``` 5. Update your `kibana.dev.yml` to point at your local package registry ```yml xpack.fleet.registryUrl: http://localhost:8080 ``` 6. Start Kibana and Elasticsearch and install, upgrade, etc your package in question to verify the changes --------- Co-authored-by: David Kilfoyle <41695641+kilfoyle@users.noreply.github.com> (cherry picked from commit 9396ef3) # Conflicts: # packages/kbn-doc-links/src/get_doc_links.ts # packages/kbn-doc-links/src/types.ts # x-pack/plugins/translations/translations/fr-FR.json # x-pack/plugins/translations/translations/ja-JP.json # x-pack/plugins/translations/translations/zh-CN.json
# Backport This will backport the following commits from `main` to `8.11`: - [[Fleet] Improve UX for policy secrets (#171405)](#171405) <!--- Backport version: 8.9.8 --> ### Questions ? Please refer to the [Backport tool documentation](https://github.com/sqren/backport) <!--BACKPORT [{"author":{"name":"Kyle Pollich","email":"kyle.pollich@elastic.co"},"sourceCommit":{"committedDate":"2023-11-16T19:35:19Z","message":"[Fleet] Improve UX for policy secrets (#171405)\n\n## Summary\r\n\r\nCloses #171225 Highlights secrets during package policy creation with a distinct\r\nbackground and icon\r\n- Add tooltip + docs link for secrets where appropriate\r\n- Detect \"new secrets\" during policy upgrade and alert the user in a\r\nseparate callout\r\n\r\n## To do\r\n- [x] Fix any failing tests\r\n- [x] Add tests for \"new secrets\" detection logic\r\n\r\n## Screenshots\r\n\r\n\r\n\r\n\r\n\r\n\r\n\r\n\r\n\r\n\r\n## How to test\r\n\r\nThere's probably an easier way to do this, but this is what I did\r\n\r\n1. Clone https://github.com/elastic/package-registry and\r\nhttps://github.com/elastic/integrations\r\n2. Add the following to `config.yml` in your package-registry repo\r\n\r\n```yml\r\npackage_paths:\r\n - path/to/your/integrations/build/packages\r\n```\r\n\r\n3. Build a version of an integration with some `secrets: true` for\r\nvarious variables. I used `1password`\r\n\r\n```shell\r\ncd integrations/packages/1password\r\n# Edit `manifest.yml` or a given `data_stream/*/manifest.yml` file to change some variables to `secret: true`. Also bump the version and update `changelog.yml`\r\nelastic-package build\r\n```\r\n\r\n4. Run the local package registry e.g. \r\n\r\n```shell\r\ncd package-registry\r\ngo run . --feature-proxy-mode=true -proxy-to=https://epr.elastic.co # makes it so you can still see EPR packages in Kibana\r\n```\r\n\r\n5. Update your `kibana.dev.yml` to point at your local package registry\r\n\r\n```yml\r\nxpack.fleet.registryUrl: http://localhost:8080\r\n```\r\n\r\n6. Start Kibana and Elasticsearch and install, upgrade, etc your package\r\nin question to verify the changes\r\n\r\n---------\r\n\r\nCo-authored-by: David Kilfoyle <41695641+kilfoyle@users.noreply.github.com>","sha":"9396ef3d6bed213b681970a4914eeb558a30ed44","branchLabelMapping":{"^v8.12.0$":"main","^v(\\d+).(\\d+).\\d+$":"$1.$2"}},"sourcePullRequest":{"labels":["release_note:enhancement","Team:Fleet","backport:prev-minor","v8.12.0"],"number":171405,"url":"#171405 Improve UX for policy secrets (#171405)\n\n## Summary\r\n\r\nCloses #171225 Highlights secrets during package policy creation with a distinct\r\nbackground and icon\r\n- Add tooltip + docs link for secrets where appropriate\r\n- Detect \"new secrets\" during policy upgrade and alert the user in a\r\nseparate callout\r\n\r\n## To do\r\n- [x] Fix any failing tests\r\n- [x] Add tests for \"new secrets\" detection logic\r\n\r\n## Screenshots\r\n\r\n\r\n\r\n\r\n\r\n\r\n\r\n\r\n\r\n\r\n## How to test\r\n\r\nThere's probably an easier way to do this, but this is what I did\r\n\r\n1. Clone https://github.com/elastic/package-registry and\r\nhttps://github.com/elastic/integrations\r\n2. Add the following to `config.yml` in your package-registry repo\r\n\r\n```yml\r\npackage_paths:\r\n - path/to/your/integrations/build/packages\r\n```\r\n\r\n3. Build a version of an integration with some `secrets: true` for\r\nvarious variables. I used `1password`\r\n\r\n```shell\r\ncd integrations/packages/1password\r\n# Edit `manifest.yml` or a given `data_stream/*/manifest.yml` file to change some variables to `secret: true`. Also bump the version and update `changelog.yml`\r\nelastic-package build\r\n```\r\n\r\n4. Run the local package registry e.g. \r\n\r\n```shell\r\ncd package-registry\r\ngo run . --feature-proxy-mode=true -proxy-to=https://epr.elastic.co # makes it so you can still see EPR packages in Kibana\r\n```\r\n\r\n5. Update your `kibana.dev.yml` to point at your local package registry\r\n\r\n```yml\r\nxpack.fleet.registryUrl: http://localhost:8080\r\n```\r\n\r\n6. Start Kibana and Elasticsearch and install, upgrade, etc your package\r\nin question to verify the changes\r\n\r\n---------\r\n\r\nCo-authored-by: David Kilfoyle <41695641+kilfoyle@users.noreply.github.com>","sha":"9396ef3d6bed213b681970a4914eeb558a30ed44"}},"sourceBranch":"main","suggestedTargetBranches":[],"targetPullRequestStates":[{"branch":"main","label":"v8.12.0","labelRegex":"^v8.12.0$","isSourceBranch":true,"state":"MERGED","url":"#171405 Improve UX for policy secrets (#171405)\n\n## Summary\r\n\r\nCloses #171225 Highlights secrets during package policy creation with a distinct\r\nbackground and icon\r\n- Add tooltip + docs link for secrets where appropriate\r\n- Detect \"new secrets\" during policy upgrade and alert the user in a\r\nseparate callout\r\n\r\n## To do\r\n- [x] Fix any failing tests\r\n- [x] Add tests for \"new secrets\" detection logic\r\n\r\n## Screenshots\r\n\r\n\r\n\r\n\r\n\r\n\r\n\r\n\r\n\r\n\r\n## How to test\r\n\r\nThere's probably an easier way to do this, but this is what I did\r\n\r\n1. Clone https://github.com/elastic/package-registry and\r\nhttps://github.com/elastic/integrations\r\n2. Add the following to `config.yml` in your package-registry repo\r\n\r\n```yml\r\npackage_paths:\r\n - path/to/your/integrations/build/packages\r\n```\r\n\r\n3. Build a version of an integration with some `secrets: true` for\r\nvarious variables. I used `1password`\r\n\r\n```shell\r\ncd integrations/packages/1password\r\n# Edit `manifest.yml` or a given `data_stream/*/manifest.yml` file to change some variables to `secret: true`. Also bump the version and update `changelog.yml`\r\nelastic-package build\r\n```\r\n\r\n4. Run the local package registry e.g. \r\n\r\n```shell\r\ncd package-registry\r\ngo run . --feature-proxy-mode=true -proxy-to=https://epr.elastic.co # makes it so you can still see EPR packages in Kibana\r\n```\r\n\r\n5. Update your `kibana.dev.yml` to point at your local package registry\r\n\r\n```yml\r\nxpack.fleet.registryUrl: http://localhost:8080\r\n```\r\n\r\n6. Start Kibana and Elasticsearch and install, upgrade, etc your package\r\nin question to verify the changes\r\n\r\n---------\r\n\r\nCo-authored-by: David Kilfoyle <41695641+kilfoyle@users.noreply.github.com>","sha":"9396ef3d6bed213b681970a4914eeb558a30ed44"}}]}] BACKPORT--> --------- Co-authored-by: Kibana Machine <42973632+kibanamachine@users.noreply.github.com>
I've been preparing some docs to drive adoption of secrets for all integration maintainers, and I think there are a few quick wins we can get done to improve the UX around secrets:
secret: truee.g. this API key field for 1password is marked as a secret in my local package registry, but it's just presented as a plain password field:
We could add a lock badge with a tooltip linking to https://www.elastic.co/guide/en/fleet/current/agent-policy.html#agent-policy-secret-values and a brief explanation that the variable is considered a secret.
secret: falseorsecret: nullprior to an upgradeI recall this being a stretch goal that we never got to in the UI implementation here, but it's definitely something we should look to do in an upcoming release. As users upgrade their integration policies to versions of integrations that support secrets, we'll want to make sure the initial onboarding experience is good.
We need to make it clear that once you save a value where
secret: truehas been provided for a variable that existed in the prior version of the package, that value will no longer be readable at all. If a user only has a record of this value in their Fleet policy (bad idea, but people will do it regardless), we need to make it abundantly clear that they could lose access to that value by saving this policy.The text was updated successfully, but these errors were encountered: