New issue
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and privacy statement. We’ll occasionally send you account related emails.
Already on GitHub? Sign in to your account
[Bug]: CSP not working in development #31029
Comments
|
Thanks for reporting this and helping to make Electron better! Because of time constraints, triaging code with third-party dependencies is usually not feasible for a small team like Electron's. Would it be possible for you to make a standalone testcase with only the code necessary to reproduce the issue? For example, Electron Fiddle is a great tool for making small test cases and makes it easy to publish your test case to a gist that Electron maintainers can use. Stand-alone test cases make fixing issues go more smoothly: it ensure everyone's looking at the same issue, it removes all unnecessary variables from the equation, and it can also provide the basis for automated regression tests. I'm adding the |
|
I think I understand what you're saying. What you're trying to say is: We need to make it clear that You can simply understand it as: electron's
I checked and there is no good way to turn off CSP (at the code level) In your example, there is an easy way to do this, just remove the cc @codebytere @MarshallOfSound, do you have anything to add? |
|
Many thanks! @BlackHole1 I will try just remove it this time. |
|
No, thanks @BlackHole1! that about sums up what I would have said :) |
|
It is pretty weird that a page in development without any csp header, will lead to csp error: Would you mind reopen this?
I hope there can be a way to allow me send request to api.github in development ! |
|
Because: In production, website is loading using file:// protocol, and in development, it is using http:// protocol. Solution: protocol.registerSchemesAsPrivileged([
{ scheme: 'http', privileges: { standard: true, bypassCSP: true, allowServiceWorkers: true, supportFetchAPI: true, corsEnabled: true, stream: true } },
{ scheme: 'https', privileges: { standard: true, bypassCSP: true, allowServiceWorkers: true, supportFetchAPI: true, corsEnabled: true, stream: true } },
{ scheme: 'mailto', privileges: { standard: true } },
]); |


Preflight Checklist
Electron Version
14.0.1
What operating system are you using?
macOS
Operating System Version
11.5.2
What arch are you using?
x64
Last Known Working Electron version
No response
Expected Behavior
No warning or allow me to disable csp, otherwise I barely can't do any test in my dev environment.
Actual Behavior
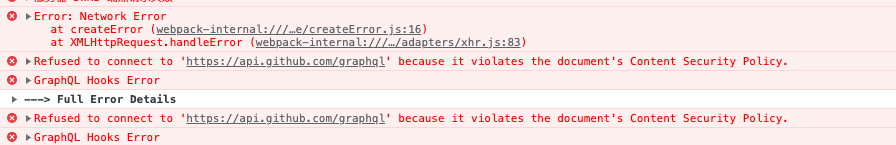
Refused to connect to 'https://tiddlygit-desktop.authing.cn/oidc/.well-known/jwks.json' because it violates the following Content Security Policy directive: "default-src 'self' 'unsafe-inline' data:". Note that 'connect-src' was not explicitly set, so 'default-src' is used as a fallback.
While I already have this meta
Testcase Gist URL
No response
Additional Information
I already have webSecurity: false, but error is still shown. And adding correct meta tag cant stop it complaining about
Note that 'connect-src' was not explicitly set,The text was updated successfully, but these errors were encountered: