-
Notifications
You must be signed in to change notification settings - Fork 316
New issue
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and privacy statement. We’ll occasionally send you account related emails.
Already on GitHub? Sign in to your account
Meta: window.ipfs v2 #589
Comments
|
Sounds like B is a good candidate for moving forwards.
Should we consider the case where an app would like basic permissions (low barrier to entry, less chance of hitting no)? 99% of the time the app only needs those permissions but very occasionally might want to do something more sensitive that requires additional permissions. With the proposal above there's no way to "get more", or could you call It would be nicer to just be able to use the API and get a prompt when you try to use restricted API calls you haven't already requested access to. It means you don't have to code around missing properties and calling Also, when I say "nicer" I think it might be necessary! The issue is if we have a provider library we don't know what type of I think we discussed a request permissions API once apon a time, what if we had |
|
Very good feedback! I think we could do all of that without adding additional APIs: Added notes:
Having that, a dapp first asks for basic dag get/put APIs (that triggers a calm user prompt,) and in rare case when dapp wants access to
Yes, we don't want to load |
|
PR with I also updated #589 (comment) to include remaining work plan. |
|
tl;dr
|
|
I've been looking at ways we can optimize thin We could make things much more efficient if we.. did not inject any script payload at all. What if websites could explicitly ask for Are there any downsides to this approach? Quick idea dump: such hint needs to happend before entire HTML is loaded, so it could be:
|
IMO headers are too strict. There might be cases where a user/developer is not able to control headers returned by hosting provider. Another example might be userscripts (I know it is quite dev focused) but I think there are cases where someone might want to write a userscript using |
|
Another idea: Something along these lines:
const handshake = await fetch('/.well-known/ipfs/companion/window.ipfs')
if (handshake.url.endsWith('window.ipfs/ready') && window.ipfs) {
// companion with window.ipfs
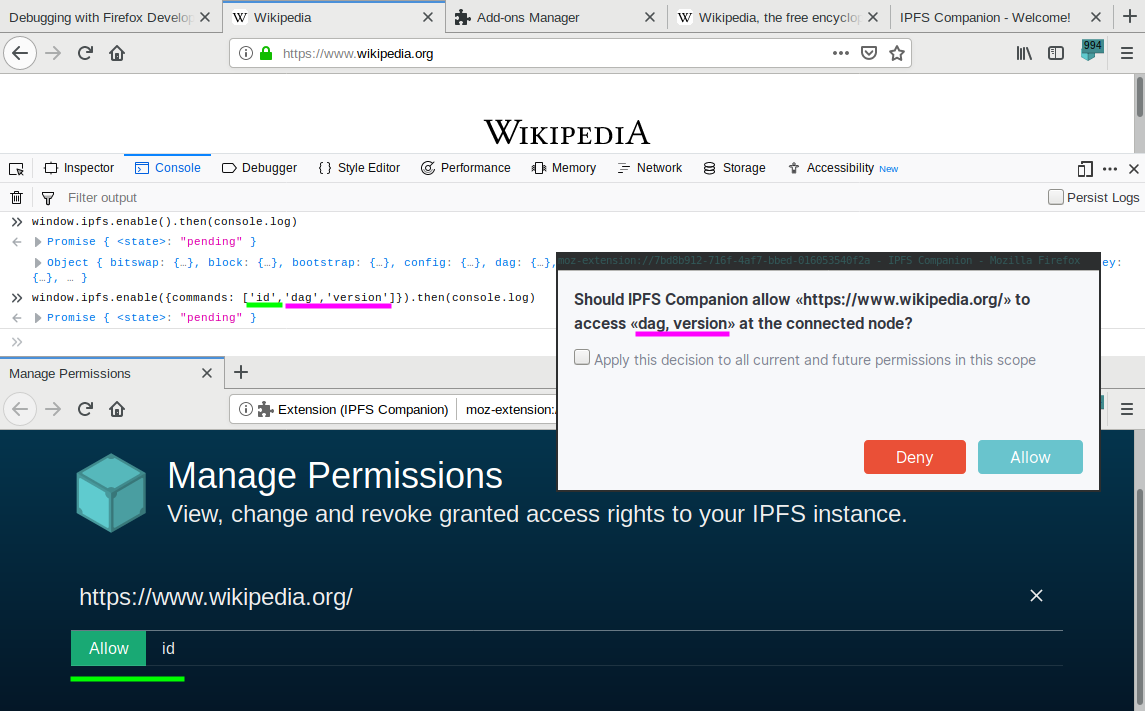
const ipfs = await window.ipfs.enable({commands: ['add','cat']})
} else {
// no companion / window.ipfs
}This comes with some interesting characteristics:
Downsides:
|
|
PSA: to remove overhead introduced by IPFS Companion the plan for the end of Q4 is to expose
This will not introduce any new overhead (reusing checks we already do for other things) and will decrease resource usage on non-IPFS websites. It will also act as a small incentive to enable DNSLink and/or self-host gateway. |
|
The It did help us understand challenges and risks, and identified the need for more robust API for the web. We are officially putting If we revisit this approach, it will be a more robust API tailored for use on the web, |
(This is a placeholder issue, will be updated in future)
The goal:
window.ipfsv2 ships and is production ready(tl;dr: injected on-demand, expose only requested APIs)
TL;DR
Future-proof way of using
window.ipfsis:Implementation Status
#619:
window.ipfs.enable.enable()(no params) and keep no-dialog for things likeipfs.cator display no initial dialog but prompt every api insteadwindow.ipfs.enable(Add window.ipfs.enable(opts) (Bulk Permission Prompt) #619)window.ipfs.enable({commands: ['id','version'] })experimentsawait window.ipfs.enable({ experiments: { ipfsx: true } })will returnipfsxversion of the APIwindow.ipfsOpen Questions
window.ipfsProxy.enable? (to avoid breaking websites that manually detectwindow.ipfsand executewindow.ipfs.<command>) or is it enough to deprecate old use for 3 months and then remove support for old ways?window.ipfs.enableshould we require permission from user for all commands? (remove acl-whitelist for things likedag.get?)window.ipfsinjection via manifest in Chromiumwindow.ipfs.enablewe should revisitRemaining TODOs (separate PRs)
window.ipfswindow.ipfswindow.ipfs.enable()Design Notes
windowobjectwindow.ethereumattributewindow.ethereum.enable()triggers permission dialogwindow.ethereumwindow.postMessageAPI injection scheme(thin content-script registers listener for
window.postMessage+window.addEventListener)windowobject (assumption: there are no other fingerprinting vectors)window.ipfsattribute. Given this reality, there is no value in over-complicating the detection.window.ipfsthat has only a.enable()methodwindowsolves the problem of signaling ipfs capability to dappwindow.ipfsbecomes a thin entry pointwindow.ipfs.enable()method, user accepts/denies, actual API object is returned with only those namespaces, permission is cached and user is not prompted next timeawait window.ipfs.enable(<capabilities>)should return a complete IPFS API instance<capabilities>should trigger ad-hoc permission prompt for that single capability (and update ACLs for the scope)window.ipfs.enable(<capabilities>)multiple times should be possible as well as an alternative, UX-friendly way to extend preexisting permissions with additional oneswindowbut there is only one additional bit of info malicious parties can use for fingerprinting.window.ipfswould be like fingerprinting based on if the user’s browser has notification or webcam possibilities. (related pro | con for Ethereum)window.ipfs.*later.enable(arg)and then target method on a cached API object + printing warning in logs.enable()callwindow.ipfsin Chromewindow.ipfsin synchronous fashion needs to be deprecated as it won't be fixed in Chrome.config) should trigger more prominent visual warning (within the same, single dialog)Additional References
Browser Vendors
windowbefore page loads)Turn on the behavior from bug 1329324 (disallowing defining non-configurable properties on a WindowProxy) on beta/release
Ethereum's
window.ethereumnavigator.permissions.*can't be usedwindow.postMessagecan't respond with a full API providerPlaces to Update (after the switch)
The text was updated successfully, but these errors were encountered: