Inspired by Paul-Reed/cloudflare-ufw and Leow Kah Man.
A simple bash script that downloads a list of IP address ranges (both v4 and v6) belonging to Cloudflare and adds them as rules to UFW (Ubuntu's Uncomplicated Firewall).
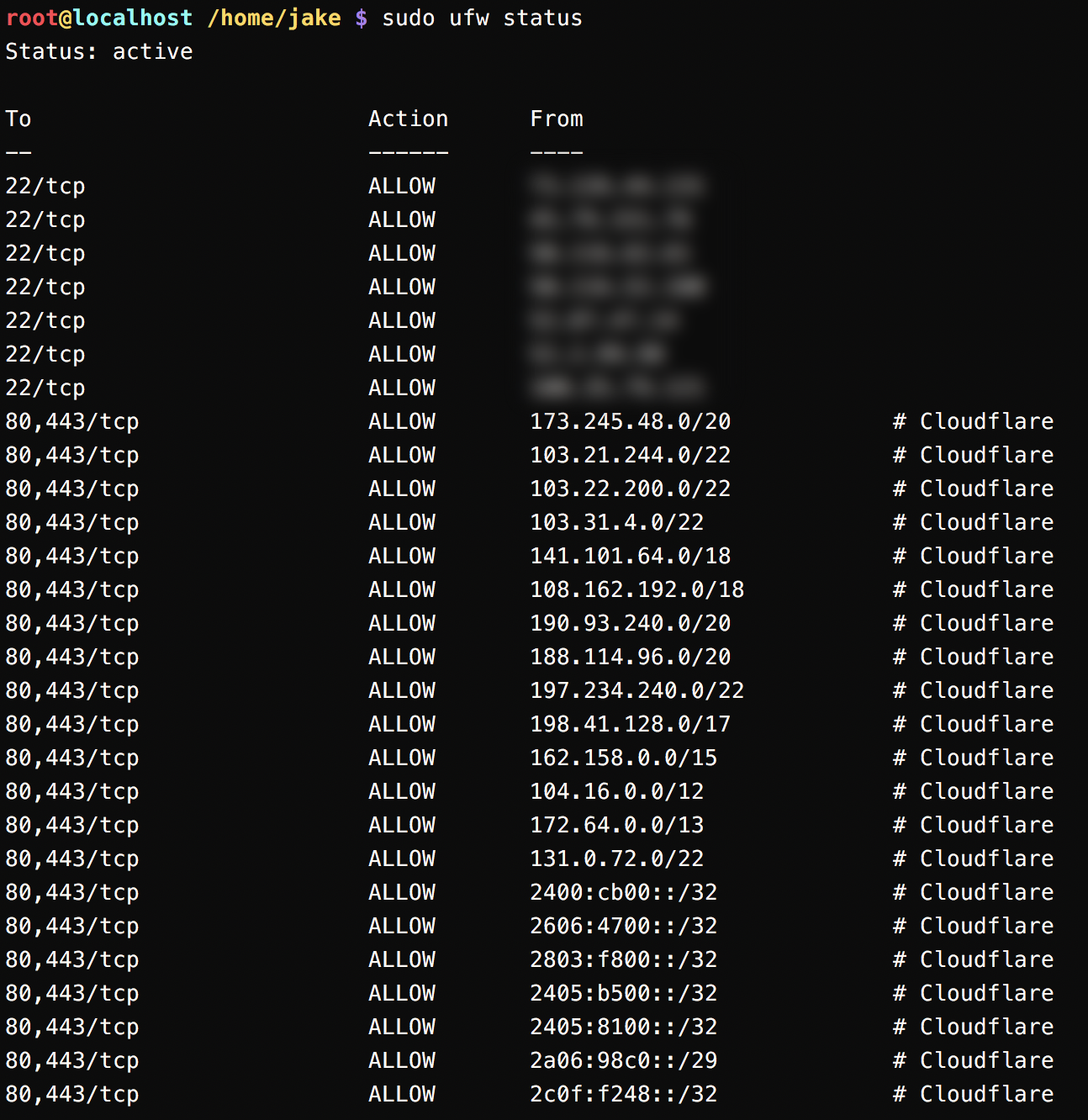
In other words, the easiest way to protect your origin server from direct attacks circumventing Cloudflare's protection.
Check your current rules first (sudo ufw status numbered); if you're already allowing traffic to ports 80 and 443 from anywhere, delete those rules with sudo ufw rule delete X (replace X with the matching rule number).
Make sure you're allowing SSH traffic for yourself before enabling UFW! Run sudo ufw allow ssh to be "safe" — you can restrict SSH to your own IPs later if you'd like to actually be safe. 😉
Download (and skim through it — don't trust strangers on the internet with sudo permissions!) and run this script once as root (sudo bash ./cf-ufw.sh).
Once you've checked that it worked (sudo ufw status numbered once again), you can run sudo ufw enable to lock everything down.
Cloudflare might add new IPs to their lists at any time. Therefore, it's important to keep your UFW rules up-to-date by running this script automatically at a set interval via a cron job.
sudo crontab -e- Add this line to the end and save:
@daily /location/of/cf-ufw.sh &> /dev/null
If you'd like an interval other than daily, crontab.guru is a nifty tool to generate the syntax to replace @daily.
cf-ufw.sh can easily be modified and adjusted to your liking. By default, it only restricts ports 80 and 443 via TCP — likely the reason you're using Cloudflare in the first place. Those can be changed to any other port number (or literally every port). You can also remove either one of the first two lines if your server isn't using IPv6 or IPv4.
In any case, I'd recommend skimming Ubuntu's full UFW documentation before enabling, as it's easy to lock yourself out of your own server if you're not careful!
This project is distributed under the MIT license.