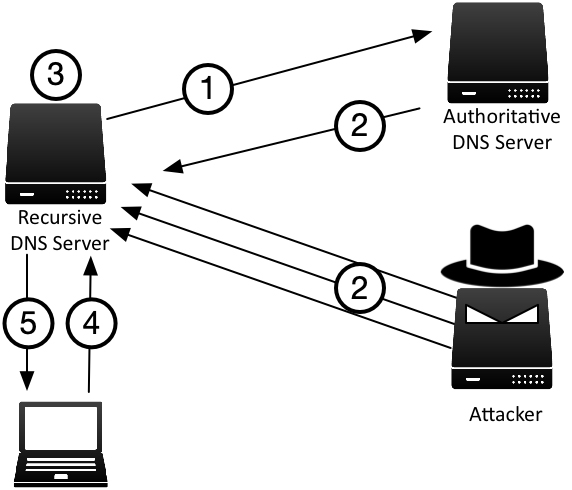
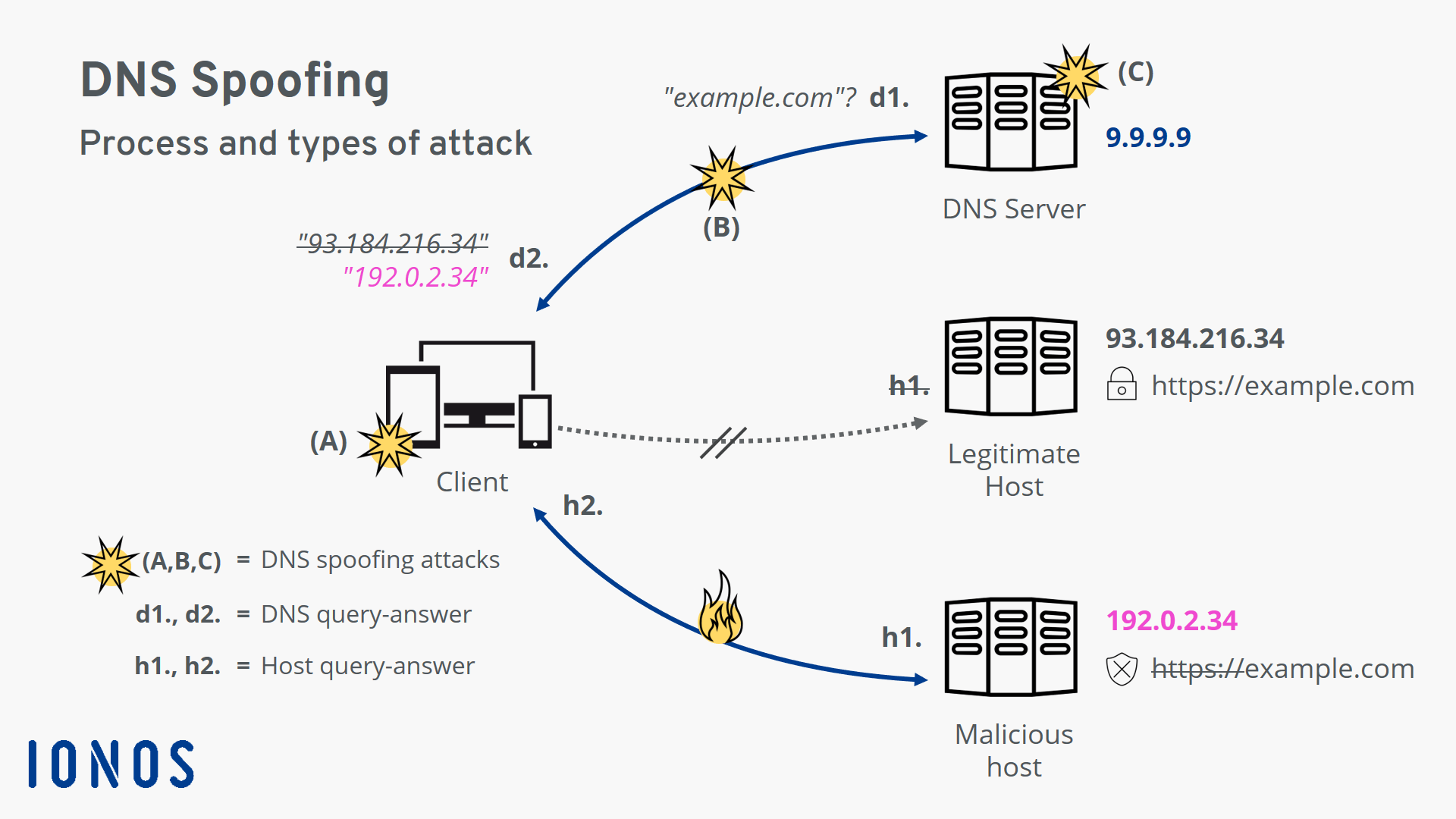
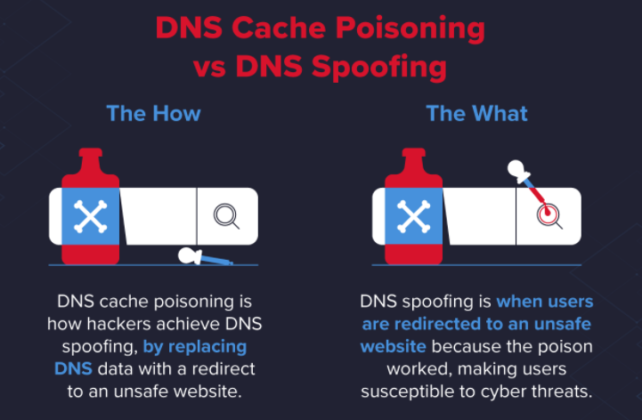
DNS Spoofing is a type of cyber attack where a hacker redirects a website's traffic to a malicious website by manipulating the Domain Name System (DNS) cache. This can be a serious security threat to individuals and businesses, as it can result in the theft of sensitive information, financial losses, and reputational damage.
DNS Spoofing works by manipulating the DNS cache, which is used to translate domain names (such as example.com) into IP addresses. By spoofing the DNS cache, an attacker can redirect traffic to a malicious website that appears to be legitimate.
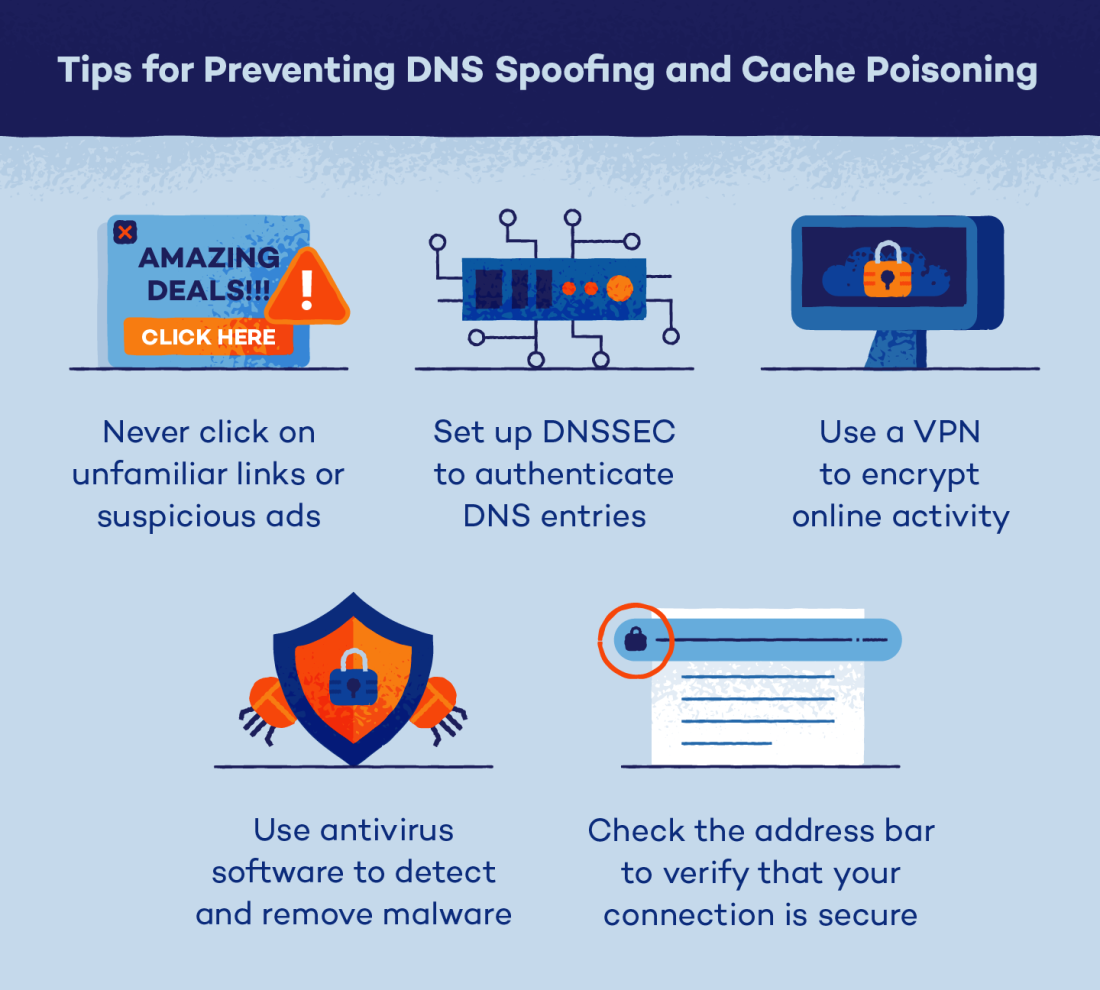
There are several techniques that can be used to prevent DNS Spoofing attacks, including:
-
Using DNSSEC (DNS Security Extensions): DNSSEC is a set of extensions to the DNS protocol that add security features, such as digital signatures, to the DNS infrastructure.
-
Implementing Strong Firewalls and Filters: Firewalls and filters can be used to block traffic from known malicious sources and to restrict access to sensitive information.
-
Regularly Monitoring DNS Activity: Regularly monitoring DNS activity can help to detect and prevent DNS Spoofing attacks before they can cause damage.
DNS Spoofing attacks have been used in a number of high-profile cyber attacks, including the 2008 DNS cache poisoning of a major U.S. ISP that resulted in the theft of over 570,000 social security numbers.
DNS Spoofing is a serious security threat that can have significant consequences for individuals and businesses. By understanding how DNS Spoofing works and implementing appropriate prevention techniques, it is possible to reduce the risk of falling victim to this type of attack.