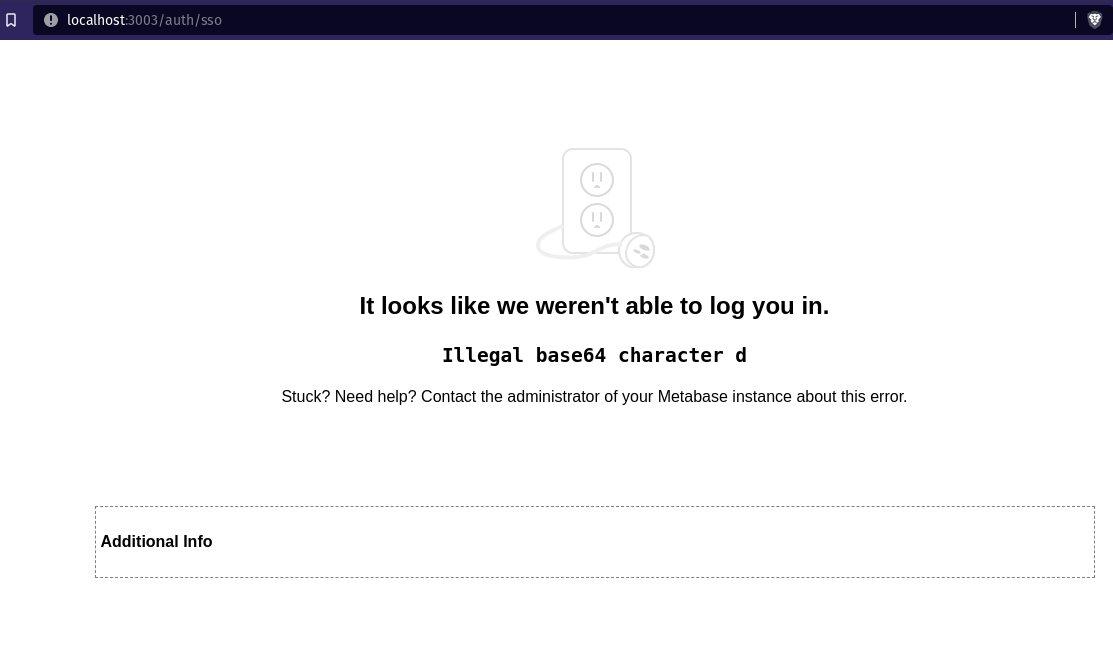
Illegal base64 character d when using OneLogin SAML SSO (43+) #23451
Labels
Administration/Auth/SSO
Enterprise SSO like SAML and JWT
Priority:P1
Security holes w/o exploit, crashing, setup/upgrade, login, broken common features, correctness
.Regression
Bugs that were previously fixed and/or bugs unintentionally shipped with new features.
Type:Bug
Product defects
Milestone
Describe the bug
When using Onelogin SSO with 43+, you can't log in. Can't reproduce on Keycloak, just on OneLogin. < 43 works fine
Logs
To Reproduce
Set up an account on OneLogin
“Issuer URL” should be the value that goes into Metabase “SAML Identity Provider URL”
“Issuer URL” should be the value that goes into Metabase “SAML Identity Provider Issuer”
Click on “View details” under the certificate, and copy the certificate to “SAML Identity Provider Certificate” in Metabase
Now try to authenticate Metabase with SSO, you'll get the error
Expected behavior
Work in the same way as 42, users are authenticated
Screenshots
Information about your Metabase Installation:
Severity
P1
Additional context
NA
The text was updated successfully, but these errors were encountered: