New issue
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and privacy statement. We’ll occasionally send you account related emails.
Already on GitHub? Sign in to your account
[discuss] client auth protocol for push/pull #38591
Comments
|
Just a thought on this topic... Perahaps Additionally, the client could send the remote and/or the list of remotes it wants to use with the creds for them along with the initial request.... however daemon configured mirrors gets a little weird here. It may be helpful to have an endpoint on the daemon that can assist the client in resolving a remote? |
|
@cpuguy83 Thank you for taking care in opening the discussion here. If I take your input and put it into a picture I could imagine a solution like this: So what are the main reasons in not doing this and what else is missing? |
|
Having an auth negotiation between client and server would also help with the issue that |
|
@caervs PTAL |
This is not true anymore with BuildKit. BuildKit uses session endpoint to call back to the client for specific credentials per host, basically like the diagram above shows but without sending requests again. This can be extended to pull/push endpoint, mirror credentials, and short-lived tokens instead. Extra security benefit would be that the password never leaves the client machine (master...simonferquel:auth-streaming actually attempted to add it long time ago). |
|
Has this work stalled (and thus stalled #34319)? |
|
This is really looking for contributors. |
|
@cpuguy83 fyi, latest development moby/buildkit#1660 |
|
I agree the right direction is getting tokens directly on the client. Once this is in place, it can allow token servers to generate longer lived, tightly scoped tokens which could also be used by orchestrators. |
|
For the push/pull case, I really like the solution outlined in #38591 (comment): the client optimistically requests a pull or push and is presented with the auth challenge to complete the operation, mirroring the authentication workflow between daemon and registry. The auth challenge could even be a direct copy of the registry's response, I think. It includes all the necessary information: the canonical name of the registry to authenticate for, the token server to authenticate against, and the auth challenge itself. The registry only needs to be reachable from the daemon and the token server from the client, which would enable the use-case of authenticating with the token server using client certificates, as discussed in #45409 (comment). sequenceDiagram
Client->>+Daemon: pull my.reg/image:tag
Daemon->>+my.reg: pull my.reg/image:tag
my.reg-->>-Daemon: 401 Unauthorized<br/>Www-authenticate: Bearer realm="my.auth/token",service="my.reg"
Daemon-->-Client: 401 Unauthorized<br/>Www-authenticate: Bearer realm="my.auth/token",service="my.reg"
Client->>+my.auth: POST /token
my.auth-->>-Client: {"token": "..."}
Client->>+Daemon: pull my.reg/image:tag<br/>Authorization: Bearer ...
Daemon->>+my.reg: pull my.reg/image:tag<br/>Authorization: Bearer ...
my.reg-->>-Daemon: 200 OK
Daemon-->>-Client: 200 OK
|
|
containerd also added support for a similar flow to this in containerd 1.7. Daemon side pulling with a client callback for auth. It also supports sending |
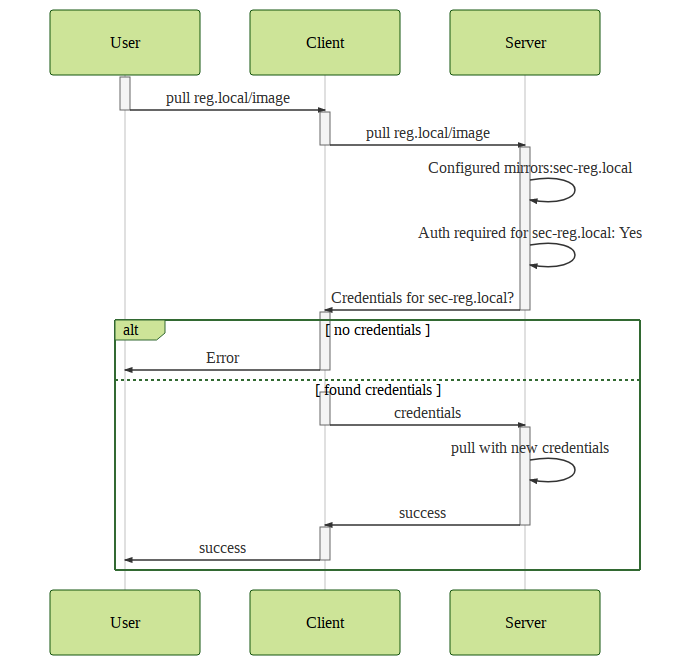
In #34319, we are looking to add support for mirrors for private registries, which has brought up the topic of how to deal with auth.
Personally speaking, I don't want to see:
The text was updated successfully, but these errors were encountered: