-
Notifications
You must be signed in to change notification settings - Fork 712
WebViewDataTest fails on API 26+ after Android Profiler file injection (part 1: whitelist) #1842
Comments
|
These may come from the new Android Studio 3.0 profiler. Three files I noticed are:
The contents of perfa.jar: $ unzip perfa.jar
Archive: perfa.jar
inflating: META-INF/MANIFEST.MF
inflating: classes.dex
creating: com/
creating: com/android/
creating: com/android/tools/
creating: com/android/tools/profiler/
creating: com/android/tools/profiler/support/
creating: com/android/tools/profiler/support/event/
creating: com/android/tools/profiler/support/memory/
creating: com/android/tools/profiler/support/network/
creating: com/android/tools/profiler/support/network/httpurl/
creating: com/android/tools/profiler/support/network/okhttp/
creating: com/android/tools/profiler/support/network/okhttp/reflection/
creating: com/android/tools/profiler/support/network/okhttp/reflection/okhttp2/
creating: com/android/tools/profiler/support/network/okhttp/reflection/okhttp3/
creating: com/android/tools/profiler/support/network/okhttp/reflection/okio/
creating: com/android/tools/profiler/support/profilers/
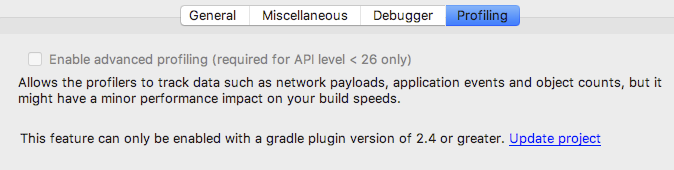
creating: com/android/tools/profiler/support/util/I confirmed that these files are not injected in AS 2.3.3 but are in 3.0.1. The new profiler description page mentions, "To show you advanced profiling data, Android Studio must inject monitoring logic into your compiled app." After following the directions to enable it, I see: Which leads me to the conclusion: Android Studio 3.0+ is automatically injecting profiler related files on API 26+ and this can also be enabled for APIs below 26: I assume this only affects debug builds. Note that I did not extensively test this so this conclusion may be wrong in some cases. |
I don't want to delete them because this may break our ability to correctly profile the app so I'm going to whitelist them. |
|
I'm having second thoughts – if our intent is to ensure there is no browsing data left on disk and the profiler caches browsing data on disk, shouldn't we delete the profiler's files? I'm going to investigate if these files are added in:
If so:
If not:
fwiw, |
|
It appears data these profiler files will only be injected if you build via Android Studio and you have opened the "Android profiler" tab at least once since this current Android Studio process has been launched. I think we should whitelist these so we don't break local builds and I think it's unlikely that these files will be added for release builds so it should be safe. |
Given the conditions under which I've noticed these files are added, it's only likely to occur in local builds. However, if we wanted to be extra safe that these files aren't kept on disk in release builds, we could explicitly delete them but then we'd presumably have to add a branch to allow developer builds to use these files without problems. For simplicity, I've opted for the whitelist.
Given the conditions under which I've noticed these files are added, it's only likely to occur in local builds. However, if we wanted to be extra safe that these files aren't kept on disk in release builds, we could explicitly delete them but then we'd presumably have to add a branch to allow developer builds to use these files without problems. For simplicity, I've opted for the whitelist.
Stack trace:
It seems there are a few files in the data/ directory that don't exist on my API 23 emulator, which is why I didn't catch this sooner.
We should also verify that these files, if we whitelist them, aren't leaking browsing state. Otherwise, we should delete them!
The text was updated successfully, but these errors were encountered: