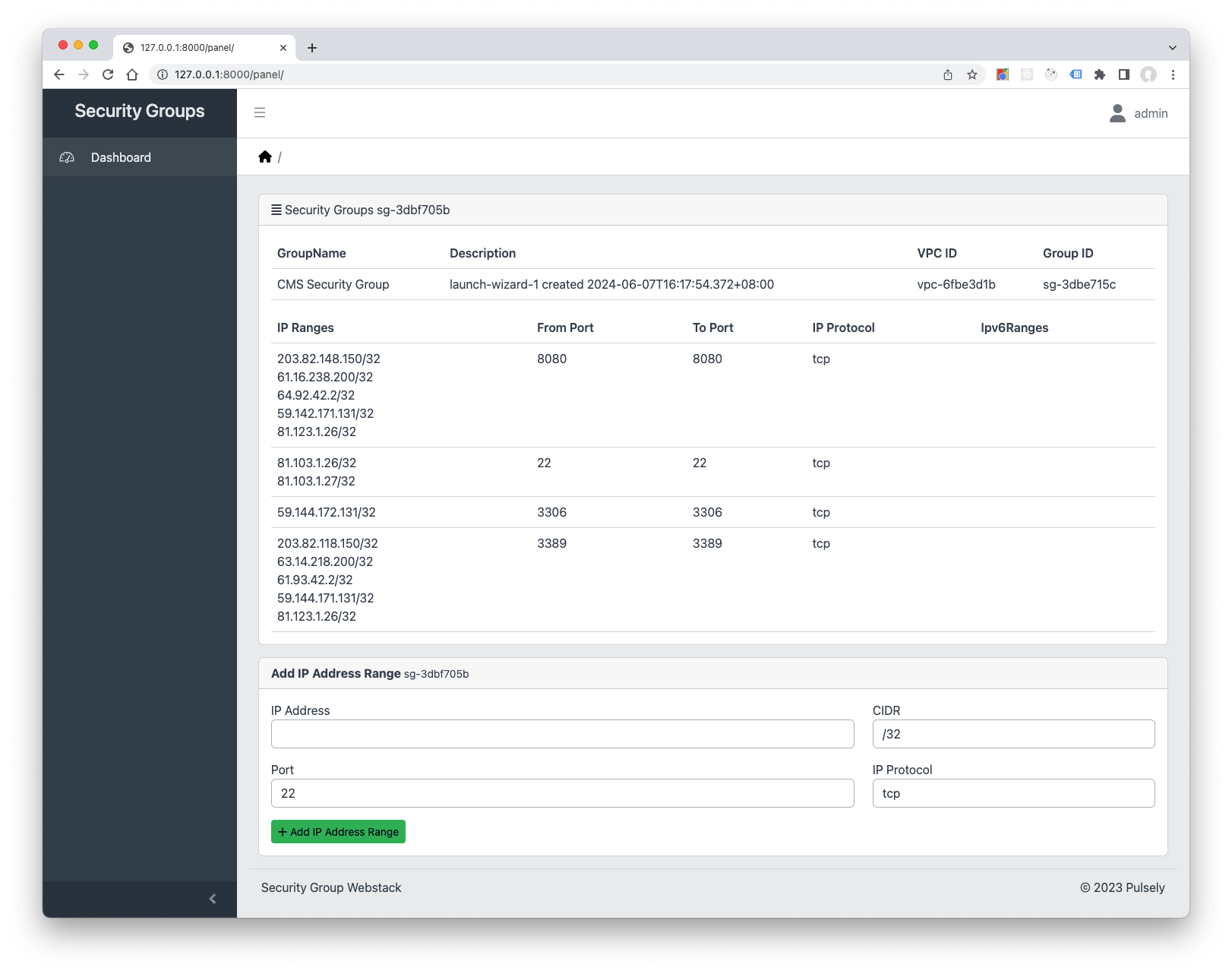
Security Groups Webstack is a Django powered webstack solution developed by Pulsely. Security Groups Webstack let you control the access of a specific Security Group in an Amazon Web Services Virtual Private Network.
You can run the Security Groups Webstack directly with a Python virtual environment, or with Docker.
The best way would be to create a new Python virtual environment. Any Python with version 3.9 should work. The only dependency would be an active Redis 4.0+ installation.
-
Pull the source code of Security Groups Webstack:
git clone https://github.com/pulsely/webstack-securitygroups
-
Changed to the directory of the Security Groups Webstack:
cd webstack-securitygroups -
Create a new python virtual environment and install the packages from requirements.txt:
python -m venv venv source ./venv/bin/activate pip install -r requirements.txt
(Your Python 3 runtime could be named differently, such as 'python3', so change to python3 -m venv venv if this is the case.)
- Then run the Security Groups Webstack:
The manage.py will check if a .env file is create and create one for you automatically if missing. The db.sqlite3 file will also be created for you 4 seconds after the installation is fired up the first time.
python manage.py runserver
- You can run your Security Groups Webstack in development mode with the Make command
make dev, or activate the venv virtual environment created previously with these commands:source ./venv/bin/activate python manage.py runserver
The Security Groups Webstack has a default DockerFile which will run with Docker or Podman in development mode.
-
The Docker setup will run the Security Groups Webstack with Django, and run the first run setup automatically.
docker-compose up
-
To run the Docker setup in daemon mode:
docker-compose up -d docker-compose run django python manage.py createsuperuser
These settings are stored at the .env file and can be overwriten at the default Django settings at securitygroups/settings_customized.py which should be created on first run.
| Varaiable | Description | Defaults |
|---|---|---|
SECRET_KEY |
The secret key for Django user authentication | Random key generated automatically |
DEBUG |
Django DEBUG mode for development. Set to false for deployment | true |
ALLOWED_HOSTS |
Host/domain names that this Django site can serve. | * |
AWS_REGION_SECURITY_GROUP |
AWS Region of the Security Group | ap-northeast-1 |
AWS_EC2_SECURITY_GROUP |
The Security Group ID | sg-xxxxxxxxxx |
EMAIL_BACKEND |
The default E-mail backend, set to django-ses for AWS deployment | django_ses.SESBackend |
AWS_SES_REGION_NAME |
Default AWS SES region Name | us-west-2 |
AWS_SES_REGION_ENDPOINT |
Default AWS SES region endpoint | email.us-west-2.amazonaws.com |
SERVER_EMAIL |
E-mail for sending the notification emails |
These settings can be overwriten at the default Django settings at securitygroups/settings_customized.py which should be created on first run.
| Varaiable | Description | Defaults |
|---|---|---|
AWS_SECURITY_GROUP_KEY_ID |
Access ID of IAM user which has access to the Security Group | - |
AWS_SECURITY_GROUP_ACCESS_KEY |
Access Key of IAM user which has access to the Security Group | - |
If you deploy to production such as Nginx with Supervisord, you will need to overwrite the default CSRF_TRUSTED_ORIGINS variable at the file securitygroups/settings_customized.py.
Configuration details of the CSRF_TRUSTED_ORIGINS is available at Django website
Type python manage.py to check for the default Django management commands available:
migrate
createsuperuser
changepassword
python manage.py migrate will create database schema on your database settings. It should automatically run by manage.py the first time though.
python manage.py createsuperuser allows you to create superuser at the command line.
python manage.py changepassword let you change password for any user in the system.
These Security Groups Webstack commands are available for testing and house cleaning.
mail_test
reset
python manage.py mail_test can be used for sending test e-mail(s) to check your notification configurations.
python manage.py reset will remove the .env, db.sqlite3, celerybeat-schedule and securitygroups/settings_customized.py configuration files to reset your installation.
(Only available for DEBUG mode on.)
You can use any databases supported by Django. Create the database settings at the securitygroups/settings.py file following the Django documentations, and you should be good to go.
This project utilizes the following components:
-
Django
Copyright (c) Django Software Foundation and individual contributors.
All rights reserved.
https://www.djangoproject.com/ -
Django SES Copyright (c) 2011 Harry Marr
MIT license
https://github.com/django-ses/django-ses -
Font Awesome
CC BY 4.0 License https://github.com/FortAwesome/Font-Awesome -
python-decouple
Copyright (c) 2013 Henrique Bastos MIT license
https://github.com/HBNetwork/python-decouple
- Admin panel template is provided by CoreUI
Copyright 2022 creativeLabs Łukasz Holeczek. Code released under the MIT License
https://github.com/coreui/coreui
The Security Groups Webstack is written by Pulsely https://www.pulsely.com/
Copyright 2023 Pulsely