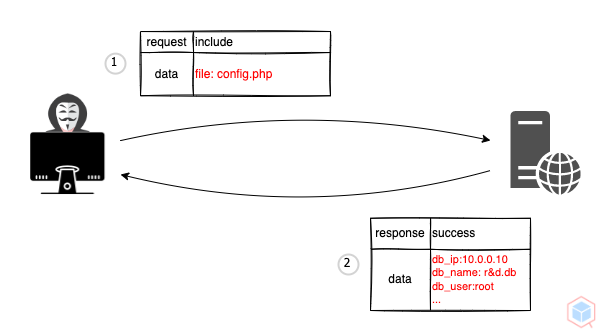
A threat actor may cause a vulnerable target to include/retrieve local file
- A threat actor sends a malicious request that includes the local file name to a vulnerable target
- The vulnerable target includes the malicious local file as PHP and outputs it
#allow_url_include = On
<?php
$file = fopen($_GET["file"], 'r');
echo fread($file, 1);
fclose($file);
?>http://vulnerable.test/index.php?file=config.php
db_ip:10.0.0.10
db_name:r&d.db
db_user:root
High
- Local file inclusion
- LFI
- Read data
- Input validation
- Whitelist
2690f163-038a-4bc5-9ff3-3a02ba5f84ee