-
Notifications
You must be signed in to change notification settings - Fork 13.8k
New issue
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and privacy statement. We’ll occasionally send you account related emails.
Already on GitHub? Sign in to your account
Add Total.js Directory Traversal module #11547
Conversation
|
Hmm this is a little interesting. I tested it on total.js version 3.2.2 and the module didn't work. 3.2.0 did though. |
This is very strange ... for convenience I am using docker to quickly have different environments so I have verified that I have not made mistakes of some kind in creating the image. I attach a screenshot of my latest test. Can you share your test? |
|
Code looks good to me. I'll land this. Thanks @fabiocogno and thanks @bcoles for reviewing. |
Release NotesThe scanner/http/totaljs_traversal auxiliary module has been added to the framework. This module exploits a directory traversal vulnerability against Total.js. |


This module check and exploits a Directory Traversal vulnerability in Total.js framework < 3.2.4 (CVE-2019-8903). Here is a list of accepted extensions: flac, jpg, jpeg, png, gif, ico, js, css, txt, xml, woff, woff2, otf, ttf, eot, svg, zip, rar, pdf, docx, xlsx, doc, xls, html, htm, appcache, manifest, map, ogv, ogg, mp4, mp3, webp, webm, swf, package, json, md, m4v, jsx, heif, heic.
References:
https://cvedetails.com/cve/CVE-2019-8903/
https://cwe.mitre.org/data/definitions/22.html
https://blog.totaljs.com/blogs/news/20190213-a-critical-security-fix/
https://snyk.io/vuln/SNYK-JS-TOTALJS-173710
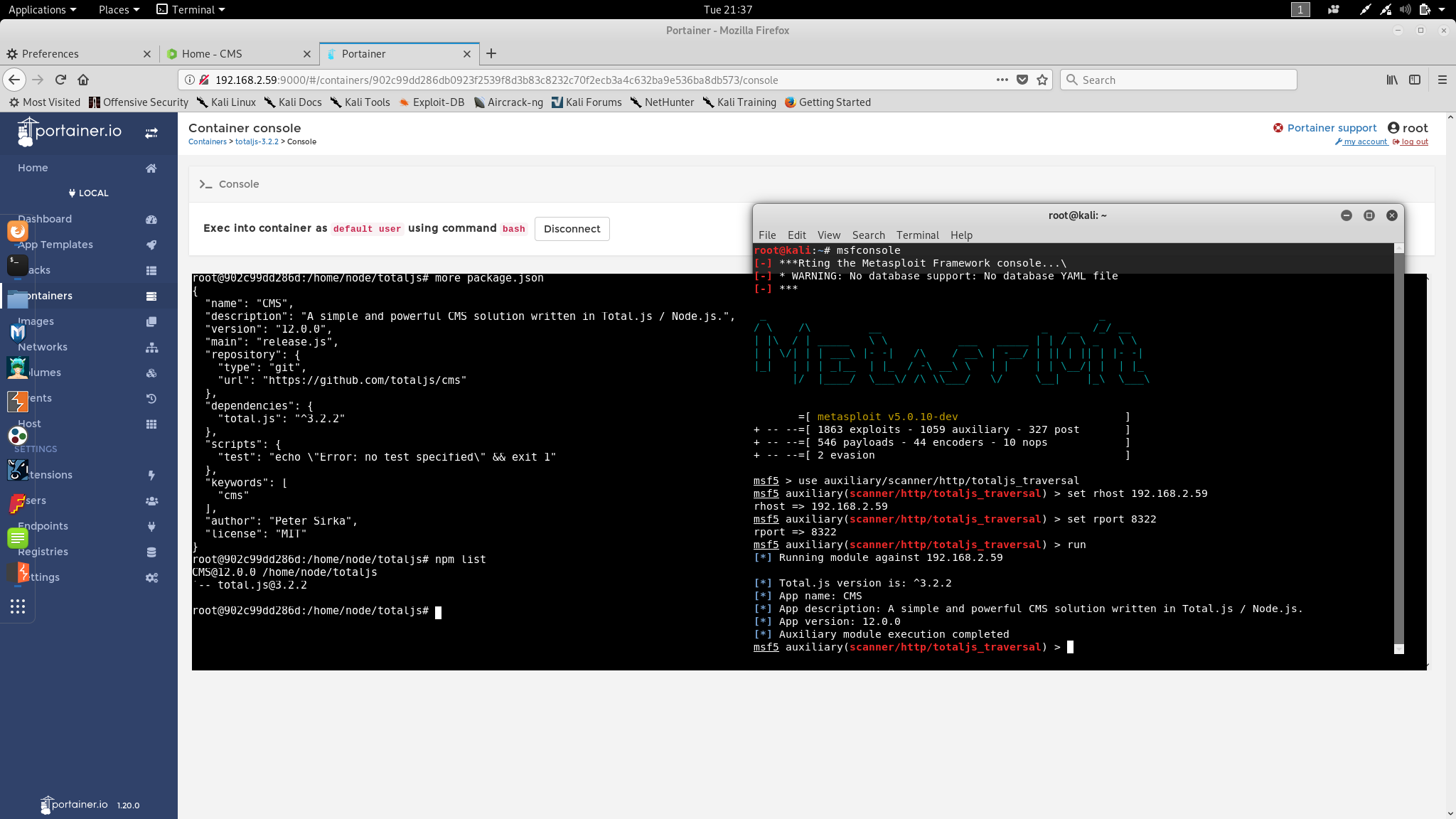
This module has been tested successfully on Total.js framework 3.1.0, 3.2.0 and 3.2.2
Verification
List the steps needed to make sure this thing works
msfconsoleuse auxiliary/scanner/http/totaljs_traversalset RHOST <IP>set RPORT <PORT>runScenarios
Testing
In order to set-up a vulnerable site, please refer to https://fabiocogno.github.io/metasploit-modules/totaljs-directory-traversal-try-this-at-home.html