-
Notifications
You must be signed in to change notification settings - Fork 758
New issue
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and privacy statement. We’ll occasionally send you account related emails.
Already on GitHub? Sign in to your account
How to address 1st-party tracker blocking? #6538
Comments
|
Maybe a scriptlet? Are there other sites on which this tracking is used? |
|
With DNS analysis, we found at least those customers. |
|
@aeris for uBo add:
However the domain names don't seem to change so they can probably be blocked in EasyPrivacy. |
|
This domain is owned by a https://uniregistry.com ... a registrar reseller. $ dig +short aeris.liberation.net You made a typo and you have a lot of imagination, conspiracy theory ? |
|
Oh my god, I miss the domain 😭 Sorry… 😨 |
|
Should help filterlist maintainers collecting/checking domains there before adding. |


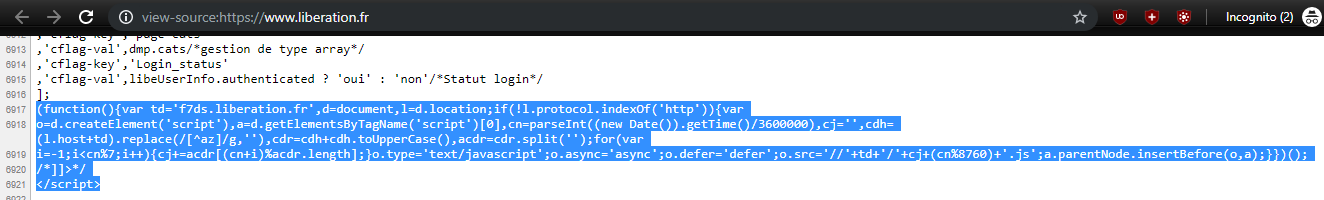
Helle here!
Since friday, we hit a case of 1st-party tracking that seems to be unblockable.
This occurs on https://www.liberation.fr/, embedding a 1st-party tracker
f7ds.liberation.fr, which point to a ugly tracking provider Eulerian via the CNAMEliberation.eulerian.net.This provider clearly states it provide unblockable tracker


Seems Criteo starts to ask the same to their customer, with 1st-party tracking pointing to
*.dnsdelegation.iosubdomain.In this case, it seems really difficult to block such tracker by tools like uBlock:
f7ds.example.org), even if we found someea.*pattern*.eulerian.netor*.dnsdelegation.io), but this is difficult to integrate to browser (those steps are internal to DNS client resolver)Do you have any way to detect then block such content from the browser?
The only (not so) efficient way I have at the moment is using DNS tools like PiHole to blacklist range of IP and CNAME pattern resolution (with regex, hostfile not usable here). And even this way, it doesn't cover all the possible case… Even tools like µMatrix seems totally inefficient on such tracker…
The text was updated successfully, but these errors were encountered: