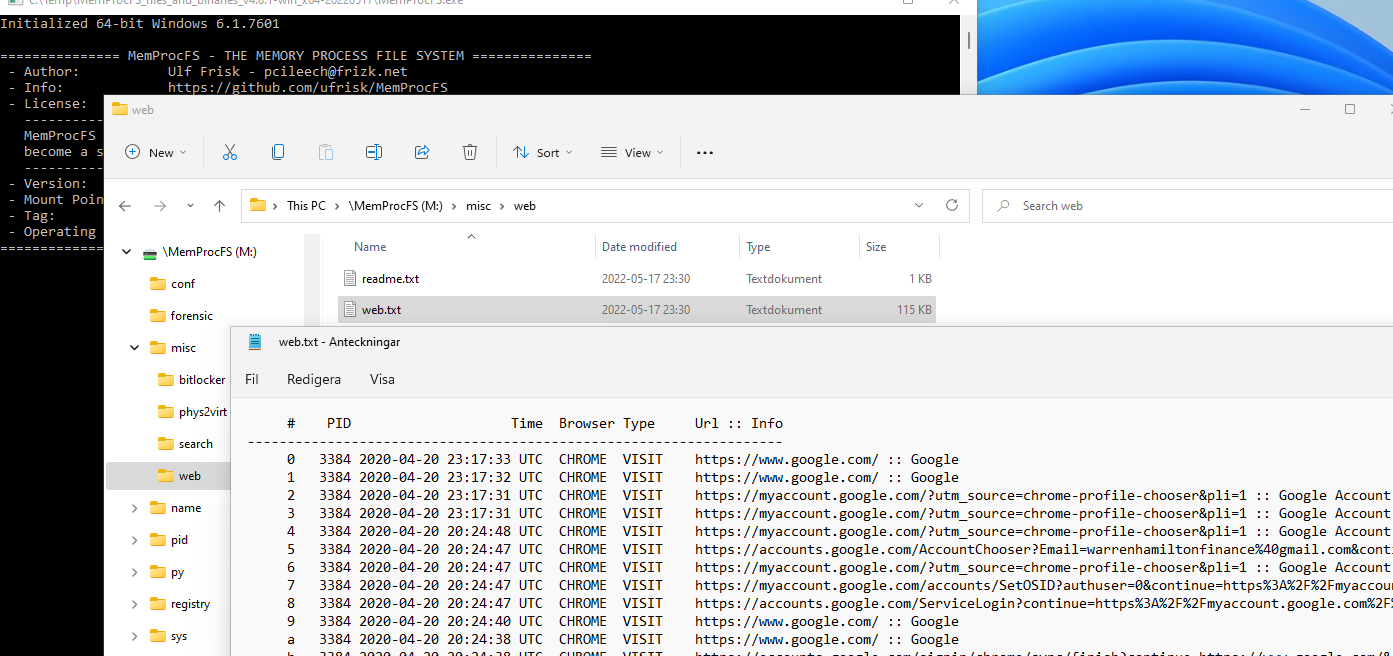
FS_Web
The directory forensic/web exists as a sub-directory to the file system root.
The directory is hidden by default. It will appear once forensic mode has been started and processing is completed.
The directory contain web browser related information such as browser history from supported web browsers.
The files in the misc/web directory are listed in the table below:
| File | Description |
|---|---|
| readme.txt | General information about the web module. |
| web.txt | Web browser history. |
Files in the forensic/web directory are read-only.
| Supported Browser |
|---|
| Brave |
| Google Chrome |
| Microsoft Edge (new) |
| Mozilla Firefox |
Internet Explorer, Microsoft Edge (old) and many other browsers are not supported. Chromium-based browsers not listed may sometimes be detected as Chrome.
The web module may recover, by using a best-effort algorithm, events related to:
| Type | Description |
|---|---|
VISIT |
Page visit. |
DOWNLOAD |
File download. |
LOGINPWD |
Saved login data. (The actual password is not recovered by MemProcFS but is often recoverable manually). |
The web browser contains many more events, such as cookies, which is not parsed by MemProcFS. Events may be recovered from active and recently closed web browsers.
The example shows the forensic/web directory with the files readme.txt and web.txt. The web.txt contains web browser information.
The forensic/web sub-directory is implemented as a built-in native C-code plugin. The plugin source is located in the file modules/m_fc_web.c in the vmm project.
Sponsor PCILeech and MemProcFS:
PCILeech and MemProcFS is free and open source!
I put a lot of time and energy into PCILeech and MemProcFS and related research to make this happen. Some aspects of the projects relate to hardware and I put quite some money into my projects and related research. If you think PCILeech and/or MemProcFS are awesome tools and/or if you had a use for them it's now possible to contribute by becoming a sponsor!
If you like what I've created with PCIleech and MemProcFS with regards to DMA, Memory Analysis and Memory Forensics and would like to give something back to support future development please consider becoming a sponsor at: https://github.com/sponsors/ufrisk
Thank You 💖