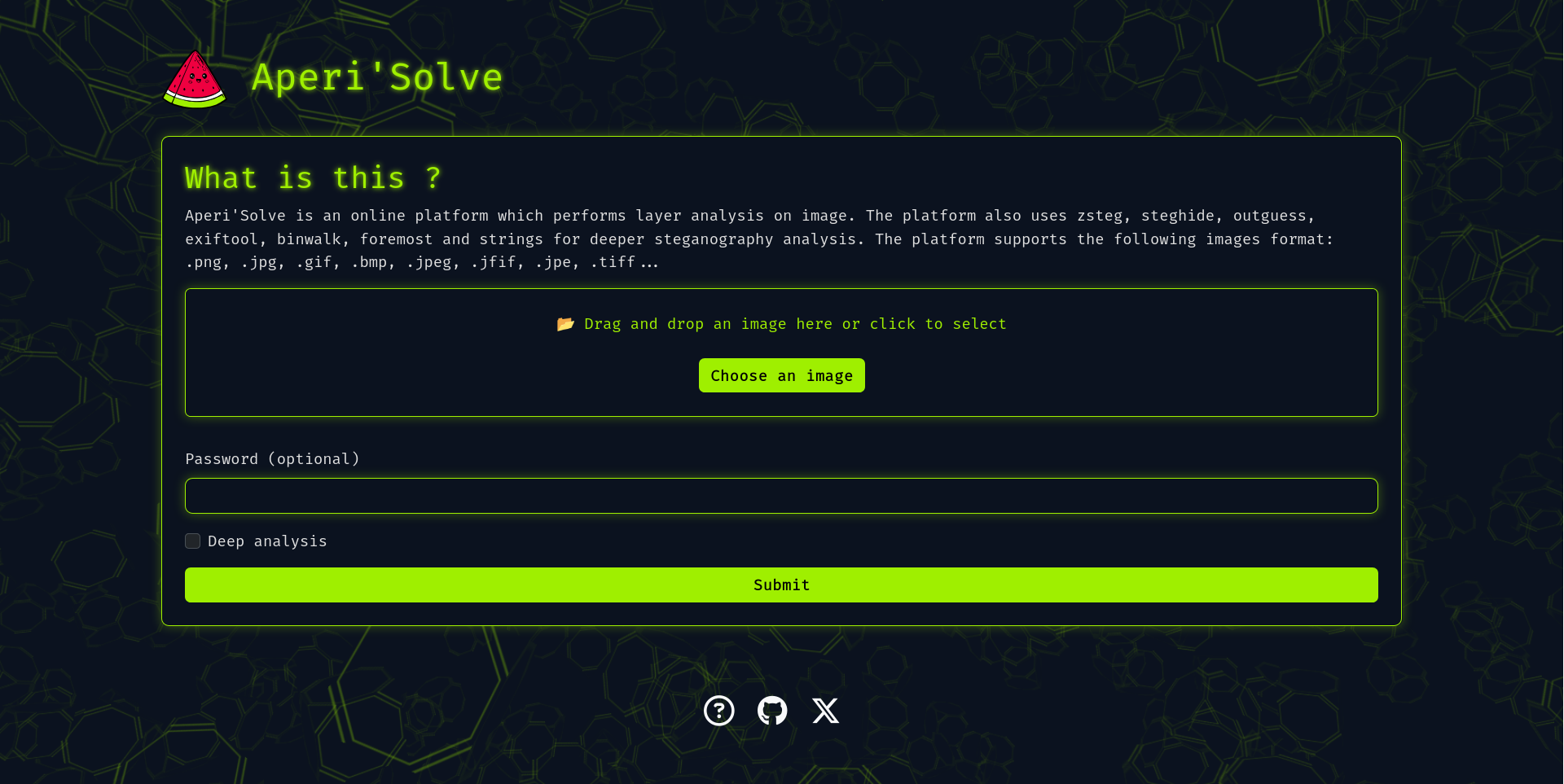
Try it now: https://www.aperisolve.com
Aperi'Solve is a platform which performs layer analysis on image.
The platform also uses "zsteg", "steghide", "outguess", "exiftool", "binwalk", "foremost" and "strings" for deeper steganography analysis.
Even if Aperi'Solve is available at the URL https://www.aperisolve.com, you can install a cli alias with the following command:
sudo sh -c"$(curl -fs https://www.aperisolve.com/install.sh)"
aperisolve image.pngAperi'Solve has been created in order to have an "easy to use" platform which performs common steganalysis tests such as LSB or steghide. The platform is also a quick alternative for people who didn't manage to install zsteg (ruby gem) properly.
Aperi'Solve is based on Python3 with Flask and PIL module, the platform currently supports the following images format: .png, .jpg, .gif, .bmp, .jpeg, .jfif, .jpe, .tiff.
The platform allow you to:
- Visualise each bit layer of each channel for a given image (ie. LSB of Red channel).
- Browse and Download each bit layer image.
- Visualise
zsteginformations such as text encoded on LSB - Download
zstegfiles such as mp3 encoded on LSB - Download
steghidefiles using a defined password - Download
outguessfiles using a defined password - Visualise
exiftoolinformations such as geolocation or author - Visualise
binwalkinformations - Download
binwalkfiles such as zip in png headers - Download
foremostfiles such as zip in png headers - Visualise
stringsoutput
The Aperi'Solve platform is a Flask web service (/web) (python 3.7) with backend daemons (/backend) which perform analysis.
Both of the two part has its own docker container.
Simply run the following command:
docker-compose build
docker-compose upThen check your browser at http://localhost:5000/.
- Statistics on homepage
- "Probable flag" with regex
- Implement "out of the box" png check (increase size of png) ?
- ...