Writeup oriented CTF skill improvement
The corresponding ctf problem and wargame will be curated based on each required skill. :exclamation: You may need the login account for browsing each wargame properly.
| Difficulty | Wargames |
|---|---|
| Easy | (Exploit-exercise) Protostar |
| Medium | (Root-me) App System, (PwnerRank) Binary Exploitation |
| High | Pwnable.kr |
- Overwrite local variable
- [Easy | x86] : (Protostar) Stack0, (Protostar) Stack1, (root-me) x86 BoF basic1
- Environment variable usage
- [Easy | x86] : (Protostar) Stack2, (root-me) x86 basic4
- Overwrite EIP (to be other function like flag printing)
- [Easy | x86] : picoctf-2013/rop1, (Protostar) Stack3, (Protostar) Stack4, (root-me) x86 BoF basic2
- [Easy | x64] : (root-me) x64 BoF basic
| Technique | Knowledge | Best Training 👍 |
|---|---|---|
| shellcode injection | shellcode | pico-ctf-2013/overflow-4 |
- [Easy | x86] : (Protostar) Stack5
- [Easy | x86] : pico-ctf-2013/rop2
| Technique | Knowledge | Best Training 👍 |
|---|---|---|
| ASLR Bypass | ROP, Mem leak | pico ctf 2013/rop3 |
| Technique | Knowledge | Best Training 👍 |
|---|---|---|
| Address Calac | ROP, Mem Leak, Address offset | defcon 2015 / r0pbaby |
- [Easy | x86] : Protostar: Format1 |
shellphish/how2heap: A repository for learning various heap exploitation techniques. 🌟
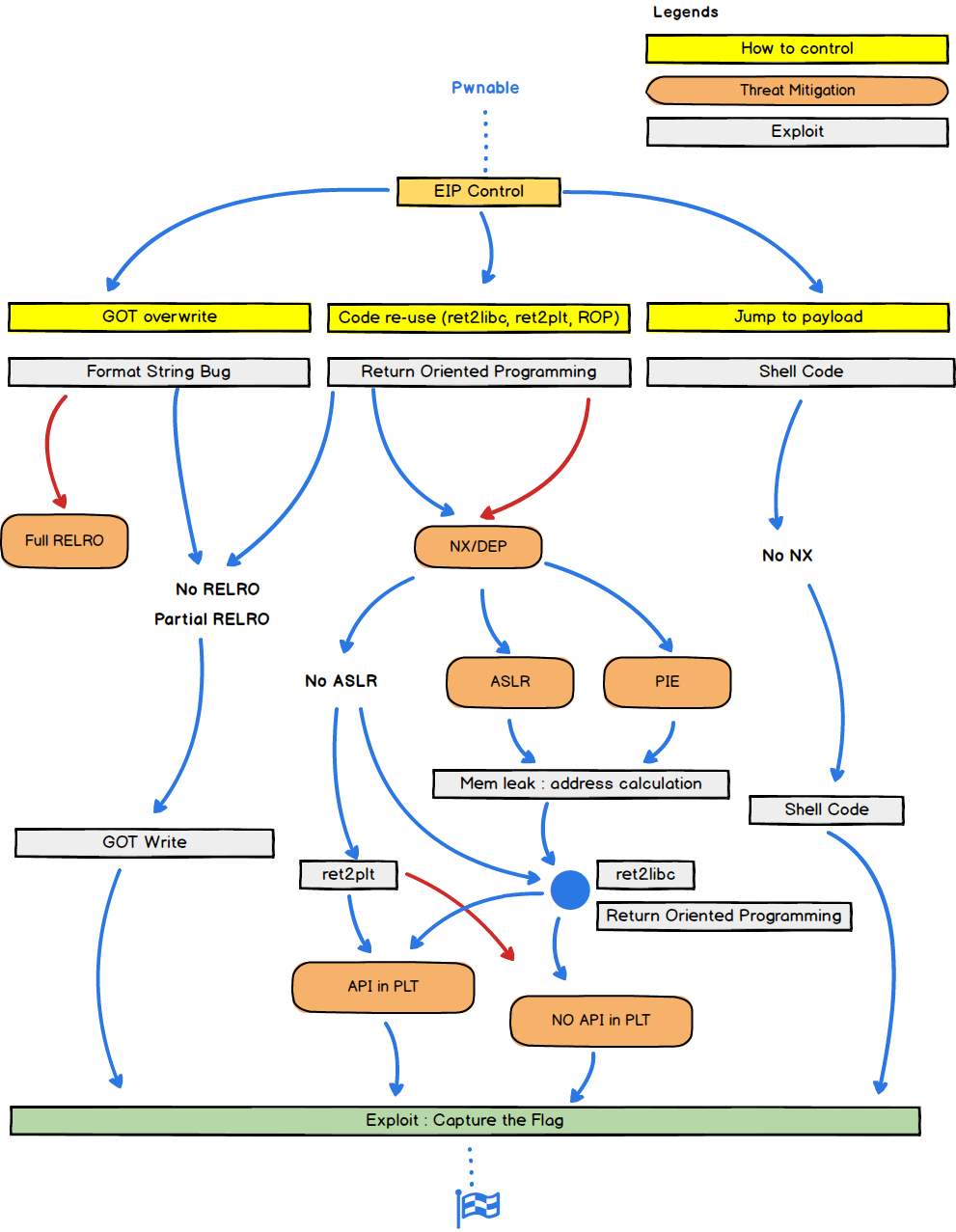
- Jump to payload
- ret2reg or jump to payload if the stack is executable and addresses aren’t randomized
- GOT overwrite
- Commonly used in format string exploitation
- Overwrite pointer in GOT with pointer to another location
- Code re-use (ret2libc, ret2plt, ROP)
- Make use of existing code and instructions to exploit the binary
- GDB enhancer : 2O2L2H/gdb-switcher
- Exploit frameworks
- Generate and search pattern string for exploit development : exploit-pattern @github
- CTF framework and exploit development library pwntools @github
- hellman/libformatstr: Simplify format string exploitation. libformatstr @github
- ROP tools
- Ropper : find gadgets to build rop chains for different architectures (x86/x86_64, ARM/ARM64, MIPS, PowerPC) : Ropper
- ROPGadget : search your gadgets on your binaries to facilitate your ROP exploitation. ROPgadget supports ELF, PE and Mach-O format on x86, x64, ARM, ARM64, PowerPC, SPARC and MIPS architectures. : ROPGadget
- LIBC database
- niklasb/libc-database: Build a database of libc offsets to simplify exploitation : libc-database