New issue
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and privacy statement. We’ll occasionally send you account related emails.
Already on GitHub? Sign in to your account
Auth Application Workflow? [Docs] #153
Comments
|
Hi @SimonLab thanks for opening this issue. 👍 To be clear: I don't expect that many people to deploy the Most people don't think in terms of code reuse or separation of concerns so they are fine with including a bunch of auth-related boilerplate in their main application; I very much prefer to separate things both for security and maintainability. Our priority is using the
|
|
I find that reviewing the ERD of an App is immensely insightful when trying to figure out what is going on. Generated manually using |
|
Same feeling:
see #153 (comment) So I'm going of the existing issues to list the features and requirements of the auth app, and to recap the why/what/how questions to see if I have more ideas to simplify the app process. |
|
Without much knowledge of database schemas, This has caused me/us no end of pain while trying to add new features ... #231 (comment) So, in addition to dramatically simplifying the database schema, If we start by deleting the tables that we don't need, we immediately simplify the ERD: If we manually edit the diagram to include the It becomes clearer what data "belongs" to a Obviously it's "unfair" to pick holes in a feature that is incomplete. |

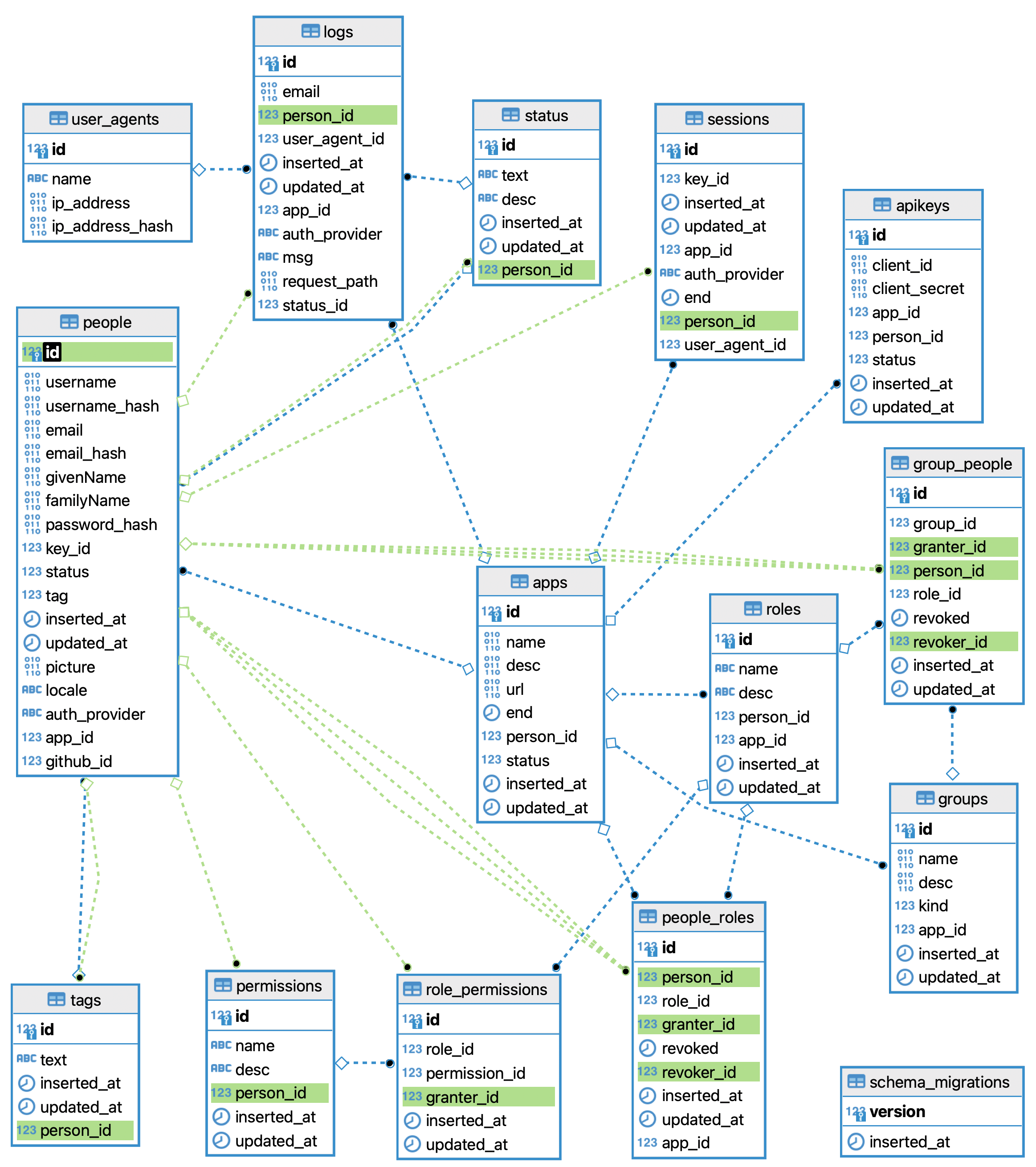



It took me a while to understand the workflow of the app after not working on it for a while. This issue contains my notes while I'm going over the code again. I'll convert them to documentation in the Readme and hopefully this will also help with #149
The application let you authenticate with Google, Github or by email:

This is done with the first part of the
indexcontroller which match the/endpoint:auth/lib/auth_web/controllers/auth_controller.ex
Lines 65 to 69 in 3a9d687
the second part of the
indexis used to authenticate user for another application. The user application redirect to the auth app and contains theauth_client_idquery parameter, eg:/?auth_client_id=123auth/lib/auth_web/controllers/auth_controller.ex
Lines 71 to 83 in 3a9d687
The redirection to the
authapp is done using theauth_pluglibrary:https://github.com/dwyl/auth_plug/blob/77963c86483c78acb3f2fe386416d67b528607e8/lib/auth_plug.ex#L32-L39
We can see that a jwt is validated and if it fails the user application redirect to the auth app with the
auth_client_id:see https://github.com/dwyl/auth_plug/blob/77963c86483c78acb3f2fe386416d67b528607e8/lib/auth_plug.ex#L47-L51
The text was updated successfully, but these errors were encountered: