New issue
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and privacy statement. We’ll occasionally send you account related emails.
Already on GitHub? Sign in to your account
Escape html places #1263
Escape html places #1263
Conversation
2515c2d
to
30ae4d6
Compare
a8c5126
to
6ba3cc0
Compare
|
I have changed the approach to make it explicit when we want to escape HTML by default on all values but by it enables unsafe HTML rendering if the "fmtDetailValue" or "fmtMetaValue" config is used as this is often used for creating custom HTML in a popup Therefore this allows the behavior or customization with HTML when users have an advanced config but safe behavior by default |
1e03e13
to
5ff43d2
Compare
|
@cmdcolin the idea of escaping by default unless one of those configs is present. I think I found a couple places where unescaped HTML might be coming through, though. It looks like it's probably happening in the mouseovers for CanvasFeatures and the description for HTMLFeatures, since the <CN0> and <CN2> are missing: |
|
I think that's true, mouseover tooltips do allow html. Another place would be like the literal htmlfeatures feature labels. There are probably a lot of places and it's a little treacherous....I am imagining that unsafe html will possibly be better managed in react land.. |
5ff43d2
to
7791809
Compare
|
I added some changes to allow explicit unsafeMouseover, unsafePopup, and unsafeHTMLFeatures. Some of this is slightly breaking if someone assumed that HTML could be safely displayed in these areas. When fmtDetailValue callbacks are used it is automatically assumed unsafe on a specific field in the popups. Otherwise you have to manually set unsafePopup on the track config. |
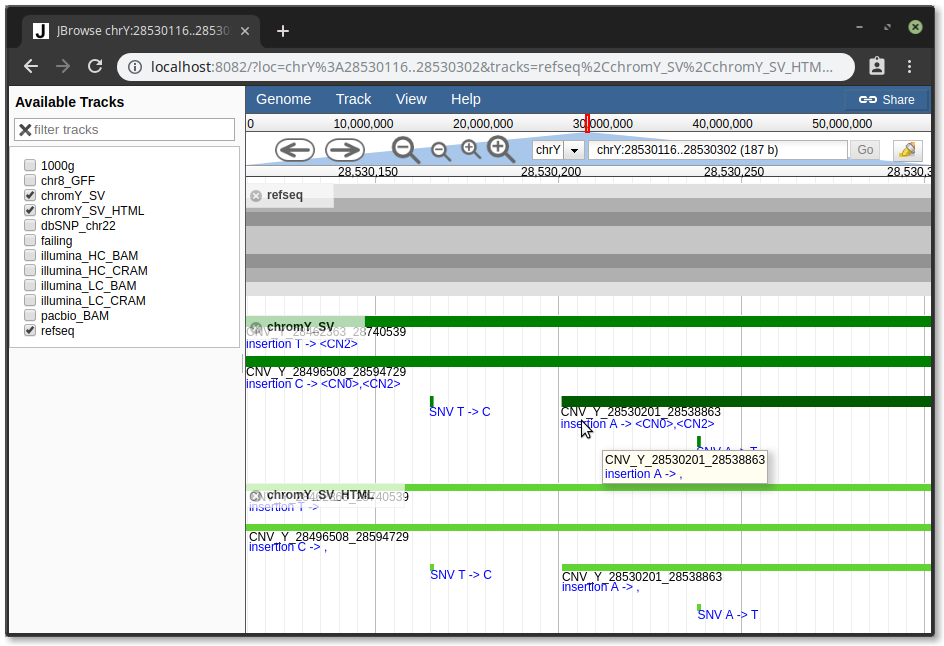

@garrettjstevens This is sort of a modification to to the escaping/unescaping approach that was going on.
If you want to test and give feedback let me know!