-
Notifications
You must be signed in to change notification settings - Fork 0
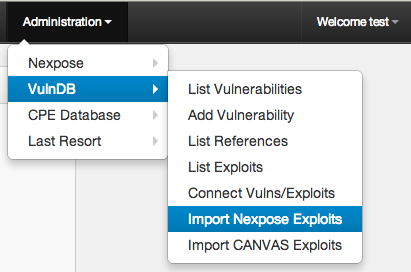
Exploit linking
Kvasir attempts to link vulnerabilities and exploits together based on the following criteria:
- Exploit list to Nexpose vulnerability ID
- CVE references
Exploit references must be imported each time since Kvasir begins as a blank slate. Kvasir currently supports two formats:
- Nexpose exploits.xml (found in /opt/rapid7/nexpose/plugins/conf)
- ImmunitySec CANVAS exploit XML
From the menu bar Exploit data can be managed from the Administration -> VulnDB section.
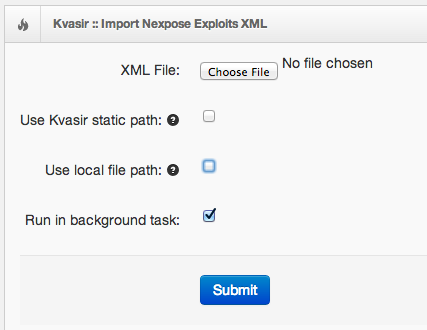
Nexpose Exploit XML data can be found in the static/etc directory or from a Nexpose installation (/opt/rapid7/nexpose/plugins/conf in Linux).
Import options:
- XML File: Upload your exploits.xml file
- Use Kvasir static path: Use the file from $KVASIR/static/etc
- Use local file path: Use the file from /opt/rapid7/nexpose/plugins/conf
- Run in background task: Send to the scheduler to run in the background
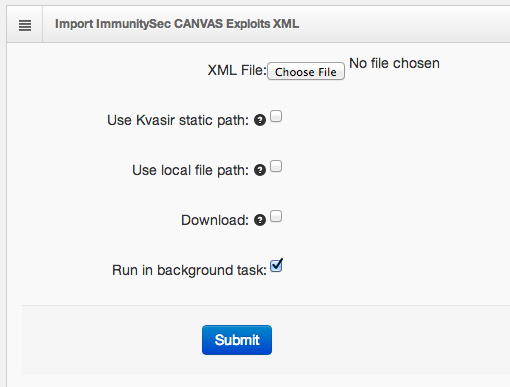
ImmunitySec CANVAS XML data can be generated from your own installation or downloaded from ImmunitySec. Kvasir will automatically download the latest file if requested.
Import options:
- XML File: Upload your CANVAS exploits.xml output file
- Use Kvasir static path: Use the file from $KVASIR/static/etc
- Use local file path: Use the file 'canvas_exploits.xml' from the provided local directory
- Download: Download the exploits file from ImmunitySec's website
- Run in background task: Send to the scheduler to run in the background
Generally exploits and vulnerabilities will be connected after scanner imports have completed. Sometimes this doesn't happen so Kvasir provides the ability to do call this function from Administration -> VulnDB -> Connect Vulns/Exploits