New issue
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and privacy statement. We’ll occasionally send you account related emails.
Already on GitHub? Sign in to your account
restrict some types of uploads #15541
Comments
|
I am trying to look into this issue and would like to suggest that we do frontend validation for the supported file type. And we can also have backend logic to check file extension and then do the database query. |
|
The most secure way is make validation on the file type (extension) in the back end , in the fronted it can bypass with (intercept the request via web proxy and change the extension with any thing else to escape from the front validation) the back end validation to check related database operation recommendation : Add new function in the back end like : if(isset($images)) { //do this for each file } (change the the image with file type and add the used extensions (CVS , SQL , XML , TXT )) and if this process succeeded : move to next step to validate your sql check I hope that help |
|
Yes, i agree to you. I suggested for both the frontend as well backend. |
|
Sure , because it missing for secure validation in back end also , i hope that fix soon |
|
Hello . I am doing this fix . Someone please send me list of valid file extension to upload. |
|
You will find the extension in @techievivek first comment @ibennetch @williamdes |
|
Okay I have done exactly like that comment for my testing. All ok then. @OverRide-BT |
|
Are this fixed! |
|
Yes it is fixed in my local . Will send PR . "Invalid file format . Valid extensions ('csv','sql','xml','txt','ods','atx','ain','aih','dbf','gz','zip','bz2') |
|
@OverRide-BT |
|
I don't really see the problem here; as far as I can tell the code isn't being interpreted when it's loaded. It's up to the user to upload the correct file — since we accept many file types, and some users don't store SQL in files with a Are you saying you're able to upload arbitrary non-SQL code or view arbitrary files from the server's file system through this? I'm a little confused about whether the initial report is that an evil user can run commands or that an innocent user can inadvertently upload a file that can't be processed. |
|
Great , i will test it again. |
|
@ibennetch about you question : yes i have already uploaded img .jpg extension as you can see and the successful message appear and this will lead to inject evil codes in the image ,And i believe that if the uploaded accepted jpg file injected by php evil function , it can accept python upload and running it the back end when the user check it and for worst cases lead to open session over the internal server also when name the uploaded file in wired name like any javascript code it will ignore the file content and show you the file have problem with the SQL codes ?! |
Great fix ! but are you checking the file content !!!!? |
I see in the images that you posted that the file did upload, but when MySQL tried to interpret the commands, as it's not valid SQL there are syntax errors. So I don't see anywhere where the file contents are interpreted by PHP or the system, it's all run through the MySQL interpreter. So I don't see yet how this could be used to run arbitrary PHP, Python, or evil image files. Are we talking about the same thing here? |
Acutely the uploaded process complete successfully as you can see in the provided screenshot, And deal with the image name as the SQL quarry |
|
@OverRide-BT we are having a hard time understanding what is the vulnerability |
|
I dont think there is a vulnerability , its just for preventing user from uploading wrong files. And It should be done because even if someone uploads a wrong file phpmyadmin tries to execute. Which leads to database hang. |
Good way to explain .... ,But there is way to manage to execute an sql commend to drop or delete database over the file content as i said so i created table called e then i uploaded an txt file contain this line : the the sql quarry executed and drop the table as you can see this is the evil method i have talk about it in my last comment |
|
@OverRide-BT Thanks for your great and logical explanation. I have done the fixation long ago but still its waiting for merging. Lets see they approve it or not. |
Thank you, and the most critical thing in this case when the user upload any SQL evil functions (Drop or Delete) the application did not alert the user with the Drop process , so that make it even worse in the application behavior |
|
to summarize the security improvements from this thread that are relevant in import upload (there are no vulnerabilities)
|
|
@emanuelb , Yes indeed , but you can make blacklist for evil function like drop or delete in case upload file contain those words it will be delete or drop the table such this function is bad for the application logic , if you drop or delete database by uploading file |
Blacklists are bad and it's easy to bypass them, there are other commands to achieve the results like deleting data such as: The sql-parser used by PMA: can be used to enforce it, but still require more testing as bypasses are probably possible, see for example the fixed issue: #12531 And even then I am not sure there is a reason to add this enforcement as the import.php work like "give me SQL file and it will be executed without validation at all" also |
|
@emanuelb yes blacklist not the solution , but if you want you can alert the user by doping the tables |

Describe the bug
in import.php
when i import new database there is no validation while the uploaded extension , for example i uploaded img and i name it like that : <svg/onload=alert(document.cookie)>
and i see the successful upload image and the app try to show me that error but there isn't any shown errors from it
To Reproduce
Steps to reproduce the behavior:
Expected behavior
A clear and concise description of what you expected to happen.

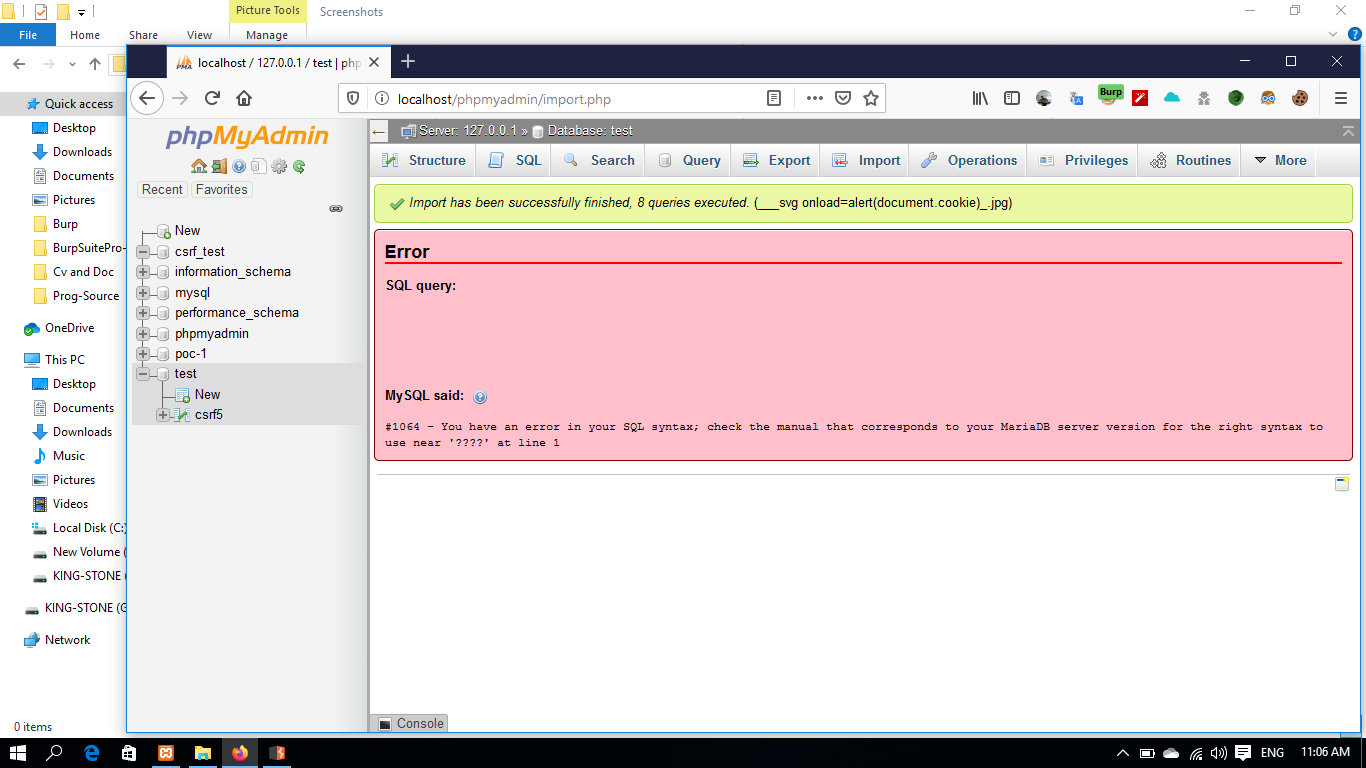
show me the error from inside the image , i injected evil function with php
Server configuration
Client configuration
Additional context
as you can see in the uploaded img
on of them show the error from the content file the uploaded php file
but when i create image with that name it's uploaded but can't read the evil function from the image
The text was updated successfully, but these errors were encountered: