-
Notifications
You must be signed in to change notification settings - Fork 3k
New issue
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and privacy statement. We’ll occasionally send you account related emails.
Already on GitHub? Sign in to your account
when broadcasting transaction, error message from server is displayed as is #4968
Comments
|
|
Thanks for the info on this. I wasn't aware this was happening. We here at Electron Cash need to do similar. A bit surprising the original code allowed rich text coming in from the server to be rendered like that.. but c'est la vie. |
|
I fell for this.. i was in a hurry and half paying attention(i know) but i didn't even think about getting phished at first since it was a pop up in the real electrum. i should have know better though. From any info you have, does there seem to be more malicious files attached to ? i.e. should i be reformatting my drive and starting from scratch or does it seem to be a localized attack on BTC? |
|
When you download the fake client they must get your seed/password somehow. I wiped electrum files then restore the wallet from seed and put a very small amount in there an let it sit. They just emptied the wallet again about 30 mintues ago. |
|
Wouldn't it better if the error message contained a hint that the following text came from a 3rd party electrum-server and should therefore never prompt you to download/update anything (or at least a hint to check electrum.org for updates if you ever want such a message about real updates)? I have no idea how many people are able to read the HTML message and still fall for it, but I don't think it can do any harm. Also the attack could work without HTML and I could see people falling for it even with the current fix. |
|
Yea, uh plain text doesn't fix anything. You will just get notices like this (made up but just example). It's hilariously the Windows XP netmsg spam problem. (which made microsoft purge it altogether from later windows). |
|
The safe way is to get the error code from servers and keep the error chart table at electrum official website. |
|
How about a It's not a true fix at all, but it might make the social engineering less effective. Error codes are good too. How about an option in settings to display detailed error messages, so that users need to go out of their way to see them? |
The sane thing is to have the decoding table in the client... |
|
It appears the error codes come verbatim from bitcoind. An unknown code could just not show any messages. |
|
In Bitcoin Core we have been fairly aggressive about not displaying human readable text sourced from the network (peers, transactions, or blocks) to users specifically because of the potential for this kind of attack. I have previously recommended everyone else do the same, and I would continue to recommend it here. |
|
We need to teach more people how to check pgp signatures. |
|
a simple anti-phishing phrase (only known to user) displayed when the app prompts to upgrade would have mitigated this? |
|
… instead parse & translate them. (#1076) This is in response to the recent sybil phishing attack discussed here in this Electrum thread: spesmilo#4968 Instead of ever displaying the server error messages in the GUI, a set of possible errors were compiles by groking the sourcecode of Bitcoin ABC and Bitcoin Unlimited. Unfortunately, an approach based on error codes is not possible because for some reason ElectrumX always returns '1' as the error code. So -- we resort to substring matching. For legitimate extant servers, this should be fine. Note that if Electron Cash is run with the `-v` option the server error response will appear in the stderr log so it will be there for developers/power users wishing to debug -- it just won't be ever displayed in the GUI. The fall-back message if a server message is not recognized is: **An error occurred broadcasting the transaction** The actual changes are isolated to `Network.broadcast_transaction` (which is nice since automatically all plugins and dependent code gets protected). The new `Network.broadcast_transaction` API is 100% backward compatible -- it just filters the server response and translates it into a fixed predefined GUI-acceptable set.
|
So the phishing message comes to an electrum legit client, then if the user fall for the phishing message the user install a the fake client and there and only there is when the coins can be stolen or they keys? Its is safe send coins with electrum 3.3.2 at the moment? Im asking this since if I understand the issue correctly the phishing message arrives to a legit electrum client. |
|
Yes, it is safe to use 3.3.2.
right |
|
Wouldn't one possible principled fix be to limit servers to only send an error code, which would select an error message out of a predefined set of messages (none of which would hopefully include a fake download link)? |
|
@zanglebert It's certainly a viable approach. It's the approach we took in Electron Cash and it's working out well so far. |
|
Really? Last I looked Electron Cash wasn't a server. |
The client (since 3.3.3) only displays error messages from a hardcoded-in-client set. The server still sends arbitrary messages (see referenced links as to why) and then the client matches them with a long list of regexes, to one of the hardcoded error messages (or "unknown error"). |
|
Perhaps. But the fact that the official client sent me to a phishing website is absurd. The client itself told me to go to electrumpal and update. I sent a not insubstantial amount of money to some rando without my knowledge.
… On Jun 20, 2019, at 5:55 AM, ghost43 ***@***.***> wrote:
They could enforce PGP signatures on the messages and embed the corresponding public key into future builds. The the broadcast messages could have a verified by @spesmilo or unverified moniker on it.
The client (since 3.3.3) only displays error messages from a hardcoded-in-client set. The server still sends arbitrary messages (see referenced links as to why) and then the client matches them with a long list of regexes, to one of the hardcoded error messages (or "unknown error").
see #4968 (comment) and #5011
—
You are receiving this because you were mentioned.
Reply to this email directly, view it on GitHub, or mute the thread.
|
It's truly worrisome. It has just happened to me, and while I understand that any software can have security holes, the Electrum website barely mentions this problem. They could have used the broadcasting message to let all users know about this problem and urge them to update. It might have saved me $270. If the next security issue is also going to be swept under the rug like this, I rather migrate to another client. |
There is no "broadcast message" functionality. The exploit is that when the user broadcasts a transaction to the connected server, the server can send back an error message. And we actually did use this functionality to warn users; but this only works if you happen to connect to an honest server. See #5452 (comment) for a list of things that has been done. |
|
Is the tweet about 3.3.3 being vunerable true? This thread seems to imply that only 3.3.2 and earlier versions are vulnerable. |
|
3.3.2 does not show rich text; |
|
Just logged into my wallet and fell victim to the hack. I want this malware off of my mac. I re-downloaded and changed my encrypted key with the official electrum 3.3.8. How do I get this crap malware 4.0 off of my computer? |
|
@Bmaz89 Where did you put the malware? /Applications? If you are on macOS Mojave -- there is little chance the malware could do anything significant like install a keyboard scanner or anything like that, due to the extremely strict permissions in the latest macOS -- you would get a notification if it tried to access anything beyond what normal applications should access. That being said -- who knows. Apple has had pretty trivial permissions breaches/escalations in recent years for locally-run apps. I would be very careful. Do you have any recent time machine backups, pre-hack... to just restore your system 100% to say 1 week ago? (Backing up your new seeds first, of course). |
spesmilo/electrum#4968 Signed-off-by: Kristaps Kaupe <kristaps@blogiem.lv>
|
And years later people are still being effected by this bug to the tune of millions of dollars. This is insane, and you should be liable for the damages here. Rendering arbitrary html on an error update page for a financial tool is not ok. I'll be send this to my local authorities. |
This comment was marked as spam.
This comment was marked as spam.
This comment was marked as spam.
This comment was marked as spam.
This comment was marked as spam.
This comment was marked as spam.
This comment was marked as off-topic.
This comment was marked as off-topic.
This comment was marked as spam.
This comment was marked as spam.
|
This Is A Big Security Issue, It Should Be A CVE LoL, But Really We Need To Fix It, Im Gonna Try Help And Yeah, Isnt Electrum A Cold Wallet? And Its Only Connected In Bitcoin Main Network?
|

EDIT2: To users: when you broadcast a transaction, servers can tell you about errors with the transaction. In Electrum versions before 3.3.3, this error is arbitrary text, and what's worse, it is HTML/rich text (as that is the Qt default). So the server you are connected to can try to trick you by telling you to install malware (disguised as an update). You should update Electrum from the official website so that servers can no longer do this to you. If you see these messages/popups, just make sure you don't follow them and that you don't install what they tell you to install. The messages are just messages, they cannot hurt you by themselves.
TL;DR: There is an ongoing attack against users where servers raise exceptions when a client broadcasts a transaction; in this case the error text is displayed as is in the client GUI. The attacker has spawned lots of servers on different /16 IPv4s to increase his chances of being connected to. The error messages are trying to get the user to download and install malware (disguised as updated versions of electrum).
In relation to #4953, we were privately sent a screenshot that was apparently floating around a German chat room (on 2018-12-21).
There wasn't really any extra information given, however most likely the following happened:
electrum/electrum/network.py
Lines 734 to 741 in b491a30
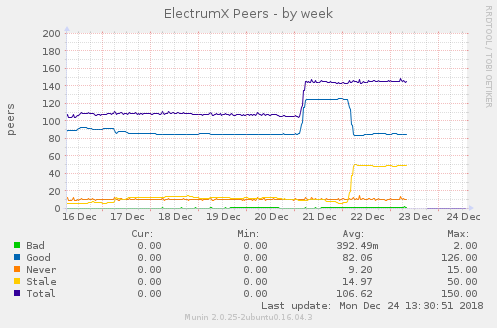
To make the attack more effective, the attacker is creating lots of servers (sybils), hence increasing the chance a client would connect to him. See this graph on the number of servers hsmiths shared re the peers found by his server:
At the very least, the message should not be displayed as rich text. It is untrusted input afterall...
We should also show some additional explanatory text at the beginning (prepend something).
For context, this mechanism of the server returning error message text to txn broadcasts is used to display error messages originating from bitcoind, such as low incremental fee or missing inputs, etc.
Maybe the server should return error codes (ints) instead, and we could have our own decoding table, but then this would need to be kept in sync with bitcoind... (EDIT3: looked into this more, see #4968 (comment))
Hours after we were sent the screenshot, we silently made mitigations in 5248613 and 5dc240d; and released 3.3.2. This is not a true fix, but the more proper fix of using error codes would entail upgrading the whole federated server ecosystem out there...
We did not publicly disclose this until now, as around the time of the 3.3.2 release, the attacker stopped; however they now started the attack again.
This is how the attack, live as writing this now, looks on 3.3.2:

This is on server
plmimservice.bitcoinplug.websiteon mainnet.My current server peers on bitcoin mainnet
Notice there are 7
*.bitcoinplug.websitedomains.There are 6
*.imaginarycoin.infodomains.There are 9
*.23734430190.prodomains.There are 7
*.cryptoplayer.fundomains.There are 4
*.krypto-familar.fundomains.(EDIT1: noticed at 2018-12-27 14:48 UTC that these domains are no longer DNS resolving)
@ecdsa @ysangkok
EDIT4: For longer term resolution of this issue, see #4968 (comment) and #5011
The text was updated successfully, but these errors were encountered: