-
Notifications
You must be signed in to change notification settings - Fork 5
Tech Talks
- One-way functions
- Elliptic curves
- Discrete Logarithm Problem
- Schnorr digital signature algorithm
- Integrated Encryption Scheme (IES)



- Block ciphers based on substitution-permutation networks
- Secure and much more efficient that asymmetric methods
- No clever maths required
- Used extensively (e.g. AES) in hybrid cryptosystems
- Requires secure key sharing
Image from https://sectigo.com/resource-library/why-automotive-key-fob-encryption-hacks-are-making-headlines

Image from An Introduction to Mathematical Cryptography by Hoffstein, Pipher, Silverman (2008)
Examples:
- Cryptographic hash functions (no trapdoor)
- Prime factorisation:
$f(p, q) = p \times q , (\mbox{mod} , N)$ - Elliptic curves:
$f(k) = k , G$

> echo -n 'Bitcoin rules!' | shasum -a 256
8109fafb32577c80ab59fa77dbea41d7bcb9bc4dc4bcf22c8b635b5ad7119c3e
> echo -n 'Bitcoin rulez!' | shasum -a 256
df4b574acf74ead4a783f7b8282a087d7b14b68c92e2e1541b6fa3c0d130b7dc
- Repetitive bitwise mixing and rotation operations
- Resulting in a deterministic one-way function
- No security proofs: reliance on "diffusion and confusion properties"
- Random Oracle model: uniform draws from
${0, 1, ..., 2^{256} - 1}$

Or rather
Note that
- We want to be able to encrypt/decrypt and create signatures
- Symmetric encryption is easy, but how to share the key?
- We need one-way functions with some structure
Over the field of real numbers
Images from https://blog.cloudflare.com/a-relatively-easy-to-understand-primer-on-elliptic-curve-cryptography/
Point "addition":
Images from https://blog.cloudflare.com/a-relatively-easy-to-understand-primer-on-elliptic-curve-cryptography/

Over the finite field
Images from https://blog.cloudflare.com/a-relatively-easy-to-understand-primer-on-elliptic-curve-cryptography/

Point "addition" still works:
Images from https://blog.cloudflare.com/a-relatively-easy-to-understand-primer-on-elliptic-curve-cryptography/
Point addition is associative:
Add a "point at infinity"
Pick a curve point
Define scalar "multiplication"
Consider the set of points
This is a cyclic group generated by
Defined in http://www.secg.org/sec2-v2.pdf
Finite field
G = 02 79BE667E F9DCBBAC 55A06295 CE870B07 029BFCDB 2DCE28D9 59F2815B 16F81798
Generates cyclic group
In this case the curve has a prime number of points
By Lagrange's Theorem, the subgroup
|G| = FFFFFFFF FFFFFFFF FFFFFFFF FFFFFFFE BAAEDCE6 AF48A03B BFD25E8C D0364141
What was the point again?
For cryptography, we need a one-way function
Scalar multiplication on the cyclic group
Given the point
We could regard
H/t https://popeller.io/schnorr-basics
Ingredients:
| private key | |
| public key | |
| message | |
| random nonce | |
| nonce commitment | |
- Lowercase
$\Rightarrow$ scalar (in the finite field) - Uppercase
$\Rightarrow$ curve point
H/t https://popeller.io/schnorr-basics
Signer:
- Computes the challenge hash:
$h = H(m || R)$ - Computes
$s = r + h , k$ - The signature is the pair
$(s, R)$
Verifier:
- Knows the public key, message & signature
- Computes the challenge hash
$h$ - Checks that
$s , G = R + h , K$
Conclusion: either the signer knows
H/t https://popeller.io/schnorr-basics
- Why do we need the (secret) random number
$r$ ?
Otherwise the signature equation
- Why must
$r$ only be used once (with any given$k$ )?
Otherwise we'd have two equations & two unknowns:
- Why is
$R$ in the challenge hash?
If instead
Hybrid encryption scheme:
- convenience of public key cryptography
- efficiency of symmetric key encryption
Secret key sharing is easy:
- Alice has private key
$a$ and public key$A = a , G$ - Bob has private key
$b$ and public key$B = b , G$ - They have the private (session) key:
$$a , B = a , (b , G) = b , (a , G) = b , A$$

Allows messages to be passed between Alice and Bob privately without E(a)ve(sdropping)

Allows messages to be passed between Alice and Bob without tampering by Eve

Allows messages of any length to be cryptographically compressed into digests that have tiny probabilities of being manufactured with other data

- Given we have digital signatures and encryption, how can entities who have not met trustfully communicate over channels using these tools?

-
Web Public Key Infrastructure is one way to bind of identity to cryptographic keys
-
It uses a combination of hashing and digital signatures of public keys to produce digitial certificates with the third party vouching for the key

-
Certificate Authorities (CAs) are responsible for signing keys to certify identity, there are many hundreds of them
-
Some major ones: DigiCert, Globalsign, Let’s Encrypt, Amazon, Google, ...
-
Their certificates are ready installed in your browser (there are well over 100 in Mozilla Firefox/Chrome/etc). Therefore your browser maker (e.g. Mozilla, Google, Apple, Microsoft, etc) assumes this trust for you
-
Three different degrees of checking:
-
Domain validation: checking the key owner controls the domain they claim
-
Organization validation: they check with third-party records and sources the organization is legitimate
-
Extended validation: they spend even longer doing the organization check
-
-
There's no field on a certificate saying which of these were performed
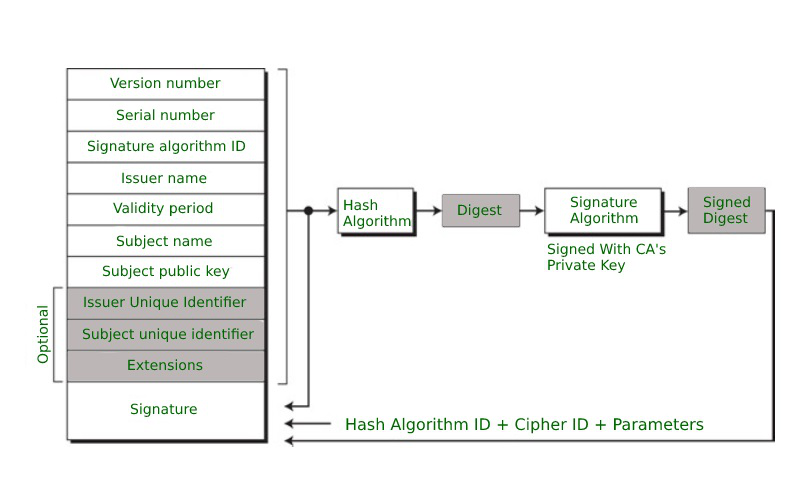
Image from: https://www.geeksforgeeks.org/x-509-authentication-service/
Image from: https://knowledge.digicert.com/solution/SO16297.html
- Click on the 🔒 in your browser address bar and
View Certificate

Image from: https://en.wikipedia.org/wiki/Transport_Layer_Security
-
TLS is the most widely used secure network protocol using this model
-
Ancestors date back to the 1980s through various incarnations
-
Updates to protocols over time have been in response to weaknesses, but general process remains similar
-
E.g. POODLE ("Padding Oracle On Downgraded Legacy Encryption") vulnerability affecting SSL 3.0
-
A customer of a bank wants to go to it's website access their account securely.
-
How does it exactly work?
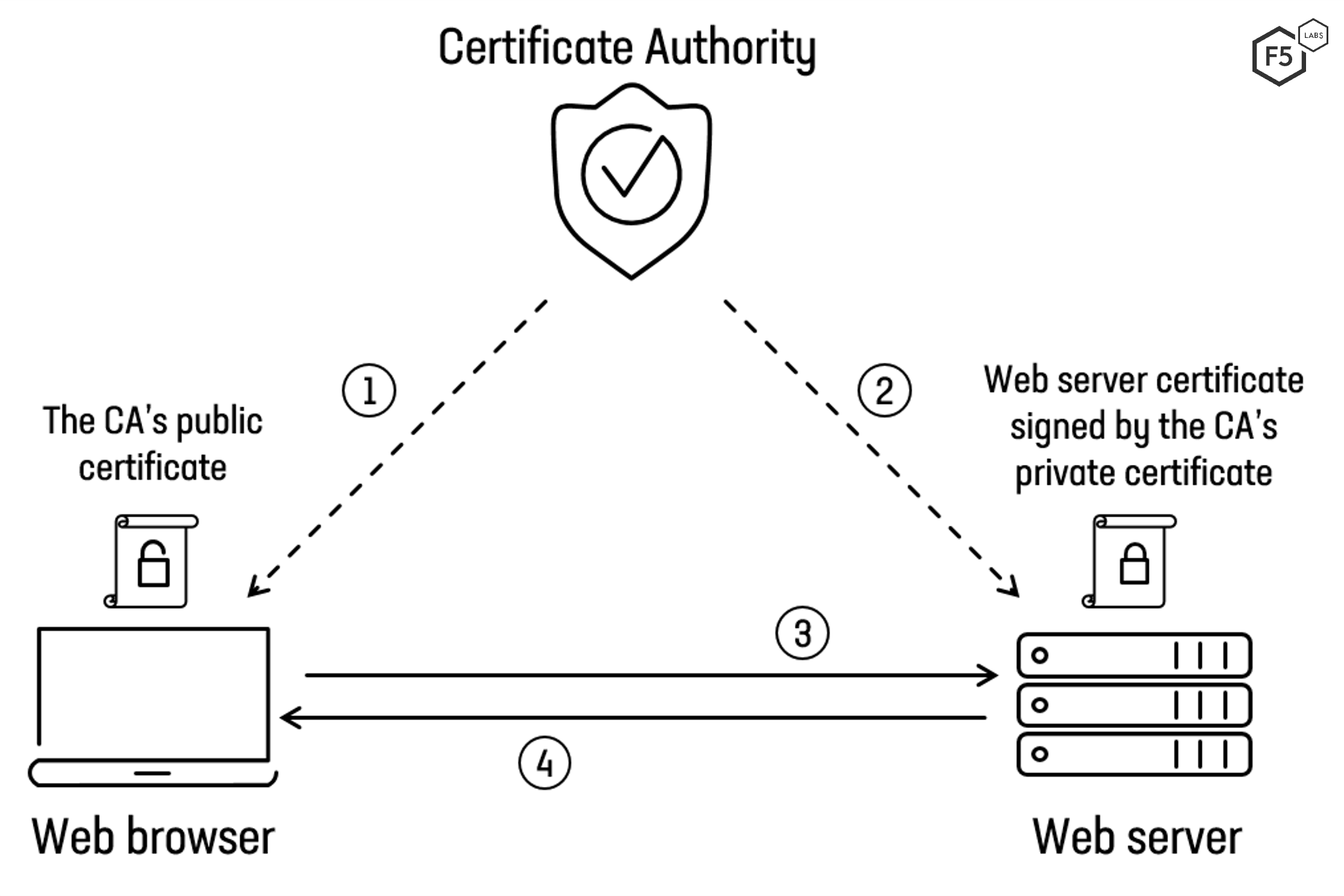
- An example of emphemeral Diffie-Hellman
-
Some specific problems were highlighted by "the Internet Architecture Board" in 2016:
-
Weak Cryptographic/Short Public Keys
-
Certificate Status Checking
-
Lack of automation for Server Administrators
-
Surprising Certificates (relates to "man-in-the-middle" attacks)
-
-
Many short keys exist in CAs (e.g. 1024-bit RSA and SHA-1, back in 2016)
-
Continuous problem as cryptographic keys get weaker over time with improved analysis methods
-
No guarantees of updates being made when they are needed and were often found to be not
-
Boils down to checking whether a certificate is currently valid
-
No guarantees of when/if your browser will do this
-
Arduous process of engagement with certificate authority means system admin do not always have the resource to do this
-
Attempts at interoperable automation have not been successful in the past
-
An issued certificate exists for a subject (e.g. a bank) that was not requested by the bank
-
The issue for the user - how can they distinguish the two certificates from CAs they trust with different keys?
-
Verifiable timestamping can help with recent optional extensions with Signature Certificate Timestamp (SCT) fields
-
However, if only one is available and it is a spurious one, the client will proceed to trust it
- Key point: Trust is placed in certificate authorities to correctly associate keys with entities real identity and there is no enforced hierarchy of trust among multiple certificates
-
Certificate authorities are a centralized trust infrastructure
-
Trust is placed by in them to correctly vouch for identity
-
The model is flawed due to its centralization; a point of failure lies within a third party
-
It relies on CAs being infallible (but they are...)
-
Trustchain aims to solve some of these problems with its key infrastructure (though not be replacing the Web PKI!):
-
No third party CAs as decentralized
-
Streamlined processes of revocation and rotation
-
Accessible and verfiable timestamped data (IPFS and Bitcoin)
-
Open software
-
Automation in reference client
-
But more on this next time!
On Thursday, February 3, 2022, attackers stole ~$1.9 Mio. from users of the Korean cryptocurrency exchange KLAYswap. The attack did not target KLAYswap itself, but exploited the trust that the WebPKI places in the internet routing infrastructure.
Attackers didn't target KLAYswap directly, but the instant messaging platform **KakaoTalk**.
The attackers used a Border Gateway Protocol (BGP) hijack.
The internet is a network of network, with tens of thousands autonomous systems (AS), each of which controls a block of IP addresses.
The BGP is responsible for directing data packets on the fastest route to their destination.