If you're already using the library, upgrading to 3.4.2 is strongly recommended for security reasons! [Read here](https://github.com/gotev/android-upload-service/releases/tag/3.4
| ℹ️ | Get started! |
|---|---|
| 📱 | Download demo APK |
- tiny library
- upload files to a server with
FTP,HTTP multipart/form-dataor binary requests - be able to easily implement other upload protocols as plugins
- handle multiple concurrent uploads in the background, even if the device is idle (Doze mode)
- automatically retry failed uploads, with a configurable exponential backoff
- possibility to automatically delete uploaded files when the upload is successful
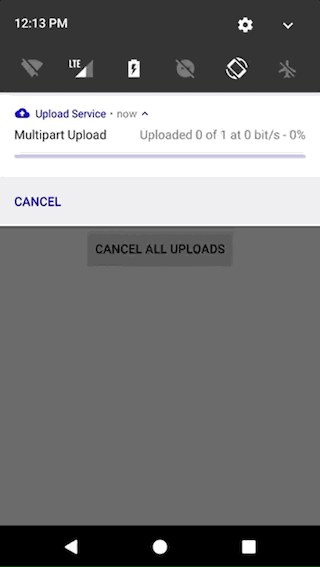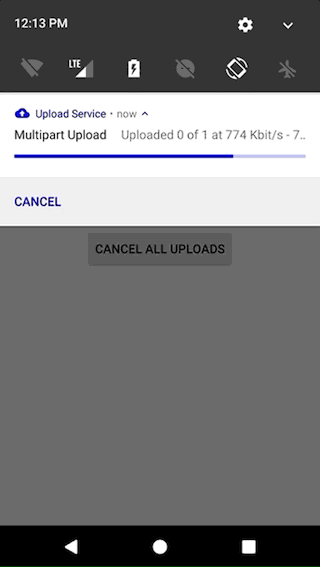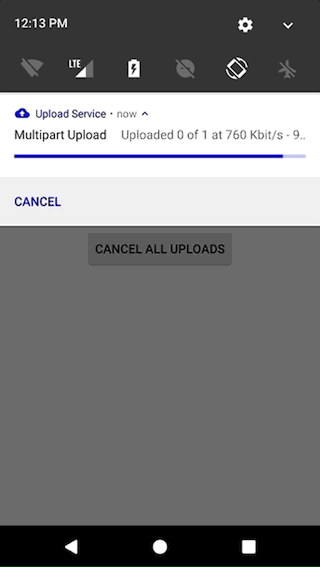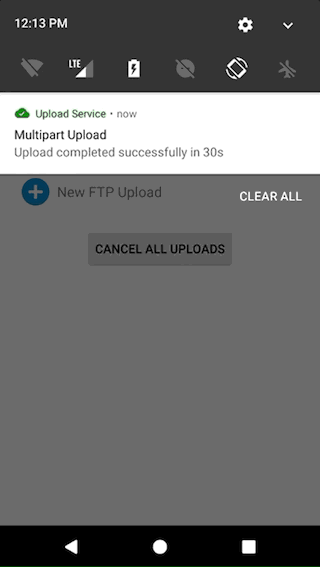
- show status in the Android Notification Center (with support for stacking notifications).
- be able to change the underlying HTTP stack. Currently
HttpURLConnection(the default) andOkHttpare supported. You can also implement your own. - be able to set library log level and to provide custom logger implementation
- easily customize the notification with text, icons and actions for the different states
At the core of the library there is a Service which handles multiple concurrent upload tasks in the background. It publishes broadcast intents to notify status. This way the logic is completely decoupled from the UI. Read further to learn how you can use it in your App.
Apps and libraries powered by this library. To be included in the following list, simply create an issue and provide the app name and a link.
- JIRA Cloud
- Quora
- crystal.io
- Fliiby
- Vydia
- React Native Background Upload
- Background Upload Plugin for Cordova
- VoiSmart IP Communicator
- Motolife
- NativeScript Background HTTP
- MyCyberLaw
- Samajbook
- Do you have a new feature in mind?
- Do you know how to improve existing docs or code?
- Have you found a bug?
Contributions are welcome and encouraged! Just fork the project and then send a pull request. Be ready to discuss your code and design decisions.
Put a star, spread the word and if you want to offer me a free beer,
Copyright (C) 2013-2018 Aleksandar Gotev
Licensed under the Apache License, Version 2.0 (the "License");
you may not use this file except in compliance with the License.
You may obtain a copy of the License at
http://www.apache.org/licenses/LICENSE-2.0
Unless required by applicable law or agreed to in writing, software
distributed under the License is distributed on an "AS IS" BASIS,
WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied.
See the License for the specific language governing permissions and
limitations under the License.
RipSecrets
We implement pipeline secret scanning on all pull request events to prevent credentials from being merged. If the pipeline scanner detects a secret in your changed files it will gate the pull request and you will need to purge the found credential from your code and re-open the PR. To prevent getting gated by this tool and as best practice you should install the secret scanner locally in a pre-commit hook to prevent the secret from ever being committed to the repo in the first place. You can find documentation on how to set it up locally here
Ripsecrets has ways to bypass secret scanning although we should not be ignoring secrets that turn up in the scans. If something is out of your control and blocking the pipeline you can bypass it in one of the following ways
- Adding "# pragma: allowlist secret" to the end of the line with the secret.
- Adding the specific secret underneath the "[secrets]" block in .secretsignore
- Adding the filepath to ignore the whole file aboove the "[secrets]" block in .secretsignore