参考文章:
https://github.com/ohpe/juicy-potato
http://www.freebuf.com/column/181549.html

参考文章:
https://hunter2.gitbook.io/darthsidious/privilege-escalation/alpc-bug-0day
http://www.ggsec.cn/ALPC-EXP.html
目标:win7、win2008
参考文章:http://www.freebuf.com/column/173797.html
https://github.com/rapid7/metasploit-framework/tree/master/data/exploits/CVE-2018-8120
https://github.com/rapid7/metasploit-framework/blob/master/modules/exploits/windows/local/ms18_8120_win32k_privesc.rb 4.过UAC UACME大量的UAC集锦 https://github.com/hfiref0x/UACME
http://www.ggsec.cn/stager-dll.html
参考资料:http://www.4hou.com/info/news/5205.html
参考资料:
http://www.ggsec.cn/Invoke-Obfuscation.html
https://github.com/danielbohannon/Invoke-Obfuscation
https://github.com/3gstudent/COM-Object-hijacking http://www.ggsec.cn/com-xml.html
https://github.com/prnd432/MMFml
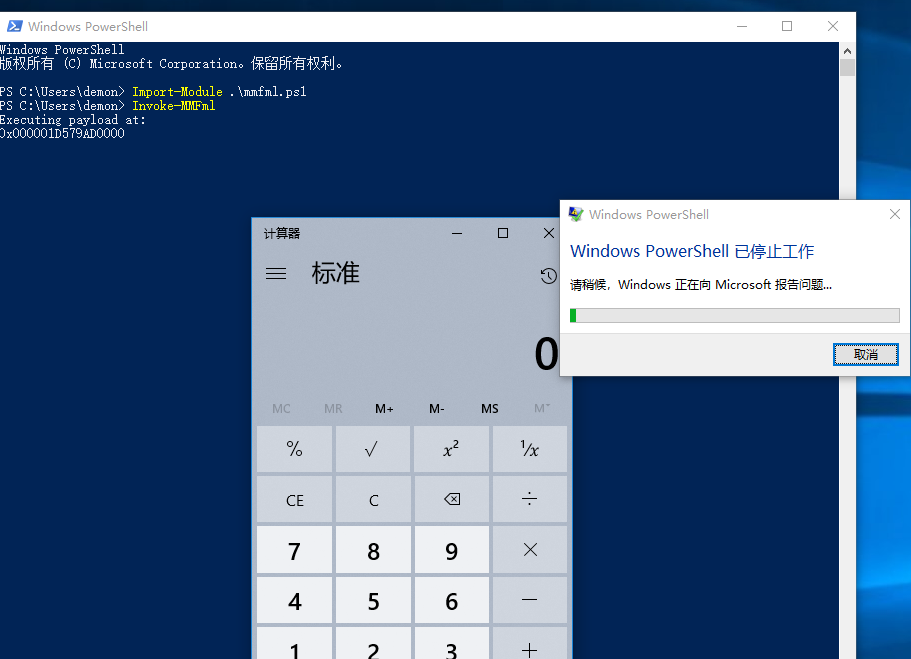
这个就自己去研究吧 https://github.com/Mr-Un1k0d3r/RedTeamPowershellScripts https://github.com/fortify24x7/FuzzySecurity-PowerShell-Suite
参考资料:
http://www.freebuf.com/articles/wireless/171108.html
https://github.com/360PegasusTeam/GhostTunnel
http://www.ggsec.cn/Ghost-tunnel.html
https://github.com/odzhan/injection
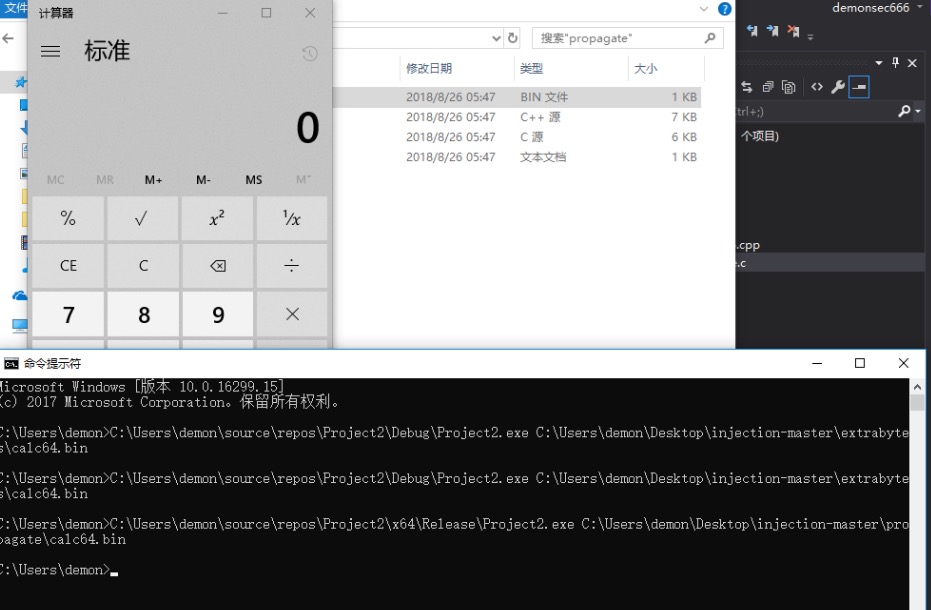
https://modexp.wordpress.com/2018/08/23/process-injection-propagate/
参考资料:http://www.ggsec.cn/propagate.html
http://www.ggsec.cn/ShellPop.html
https://github.com/0x00-0x00/ShellPop
http://www.ggsec.cn/sigthief.html https://github.com/secretsquirrel/SigThief
http://www.ggsec.cn/Linux-inject-kimi.html
https://github.com/LOLBAS-Project/LOLBAS https://lolbas-project.github.io/ https://github.com/3gstudent/Pentest-and-Development-Tips/blob/master/README.md http://adsecurity.org/?p=483 https://gtfobins.github.io/ https://github.com/CyberMonitor/APT_CyberCriminal_Campagin_Collections https://bohops.com/2018/08/18/abusing-the-com-registry-structure-part-2-loading-techniques-for-evasion-and-persistence/ https://attack.mitre.org