A landingpage for users with some links and options to change their ldap password and email. This can be used at organizations where many services are used (Rocket.Chat, Nextcloud, ...) to provide users with a nice looking overview. The application has been purpose-built for a fairly simple use-case. Due to limited time, I don't have much of a desire to widen the scope.
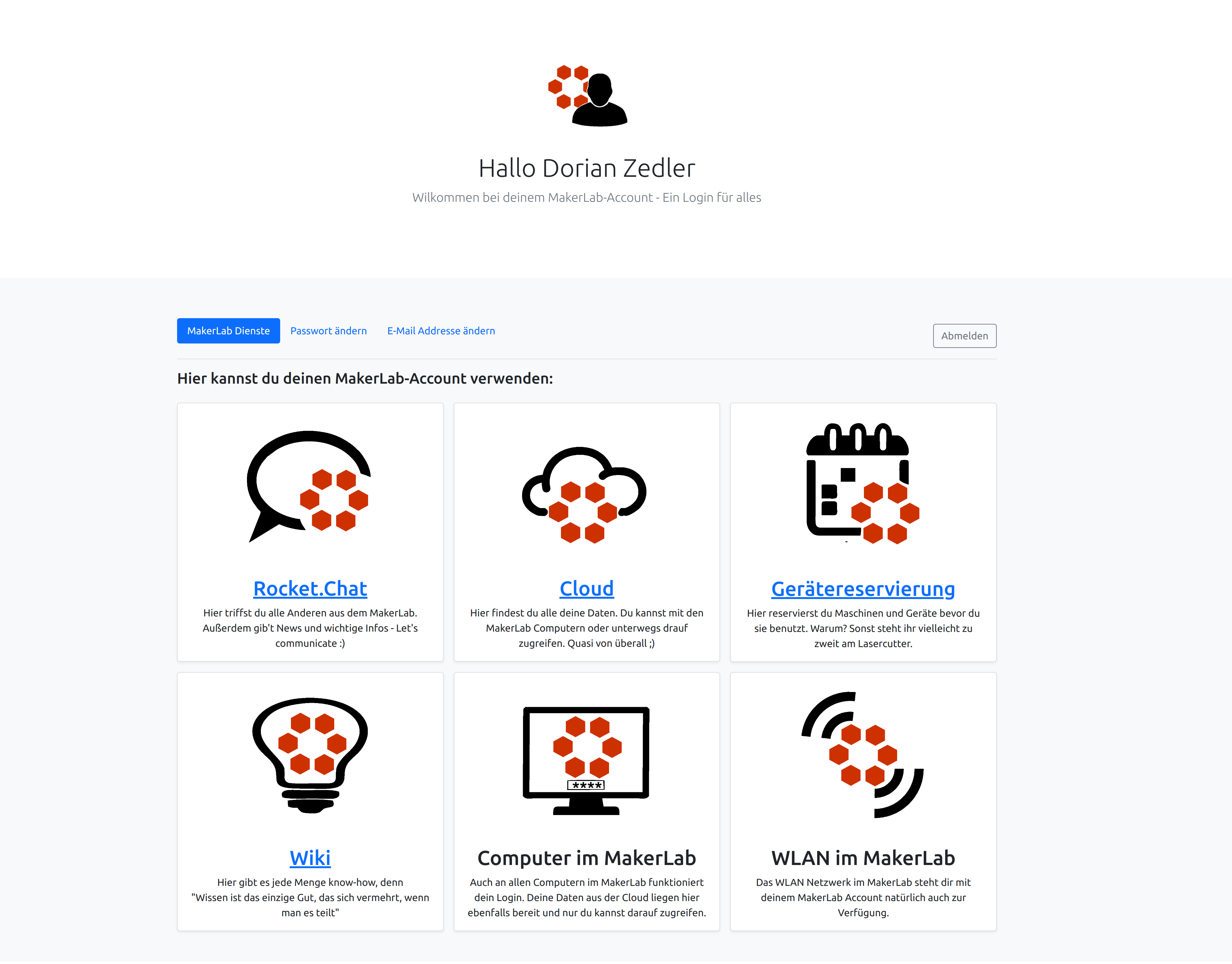
- Give users an overview of all your services
- Categorize your services
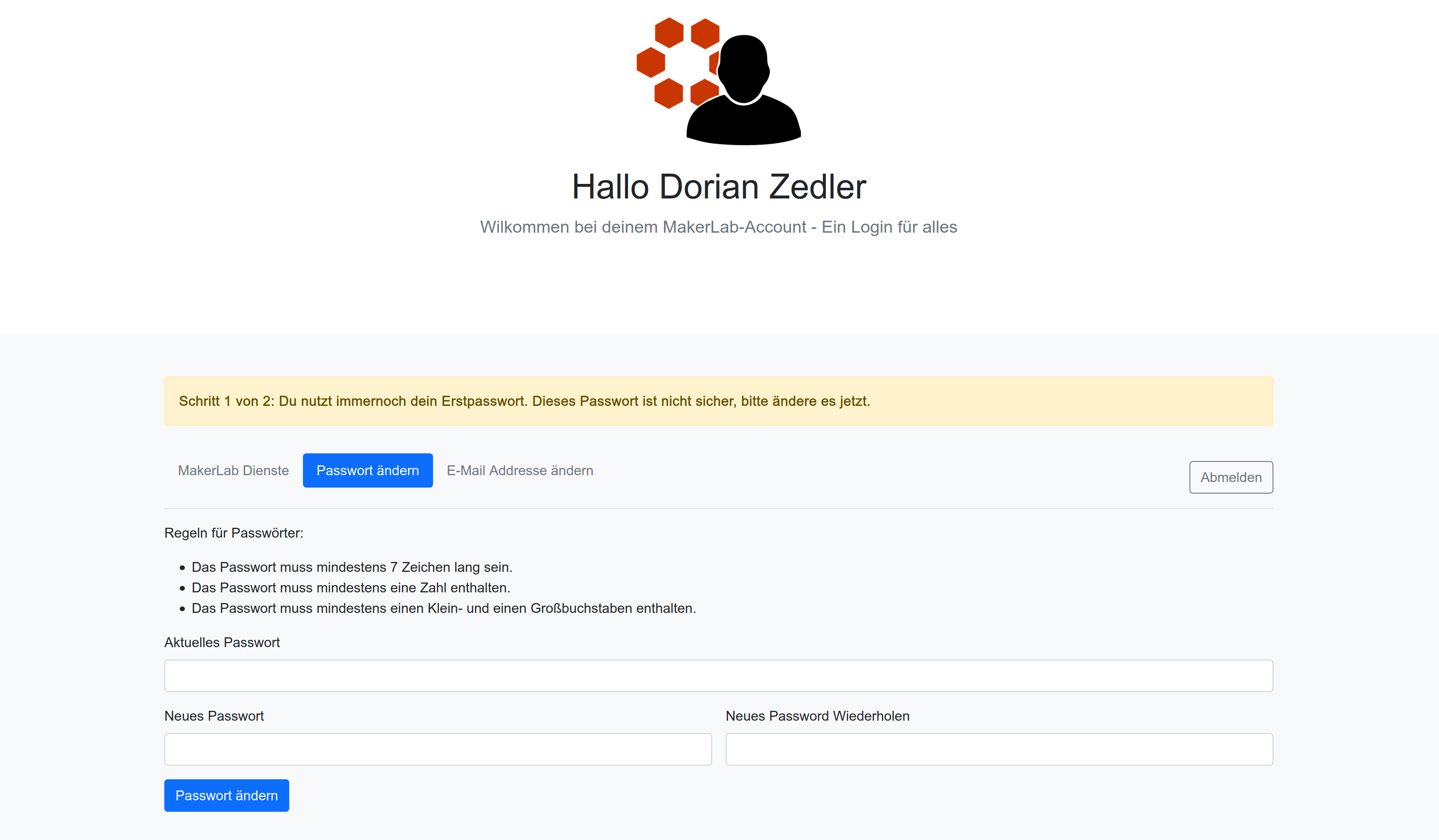
- Let users change their password
- Force users to change their password if they are still using the default password
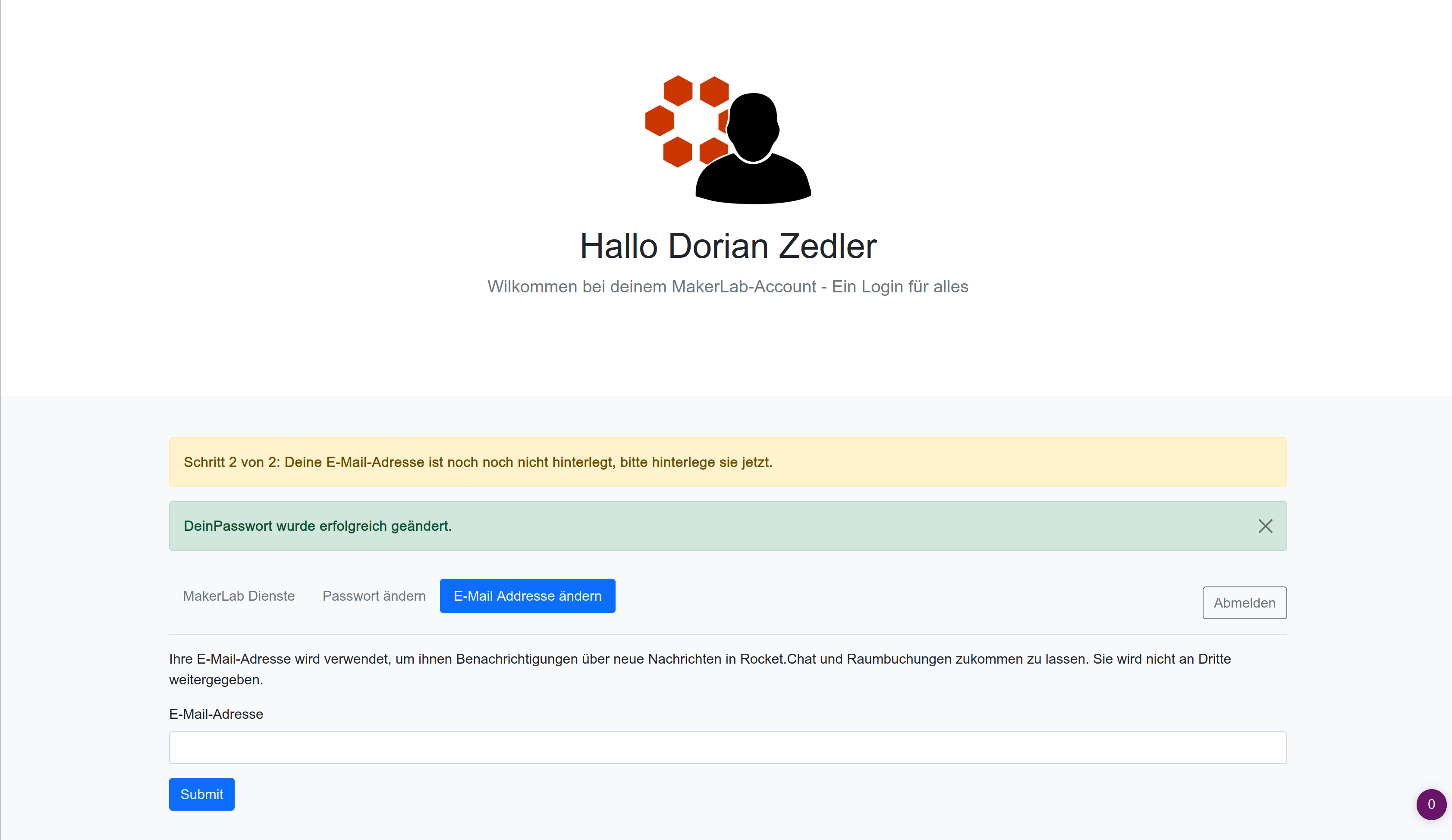
- Let users change their email
- Force users to change their email if they are still using the default email
- Let users generate Jitsi links (can be restricted to certain LDAP groups)
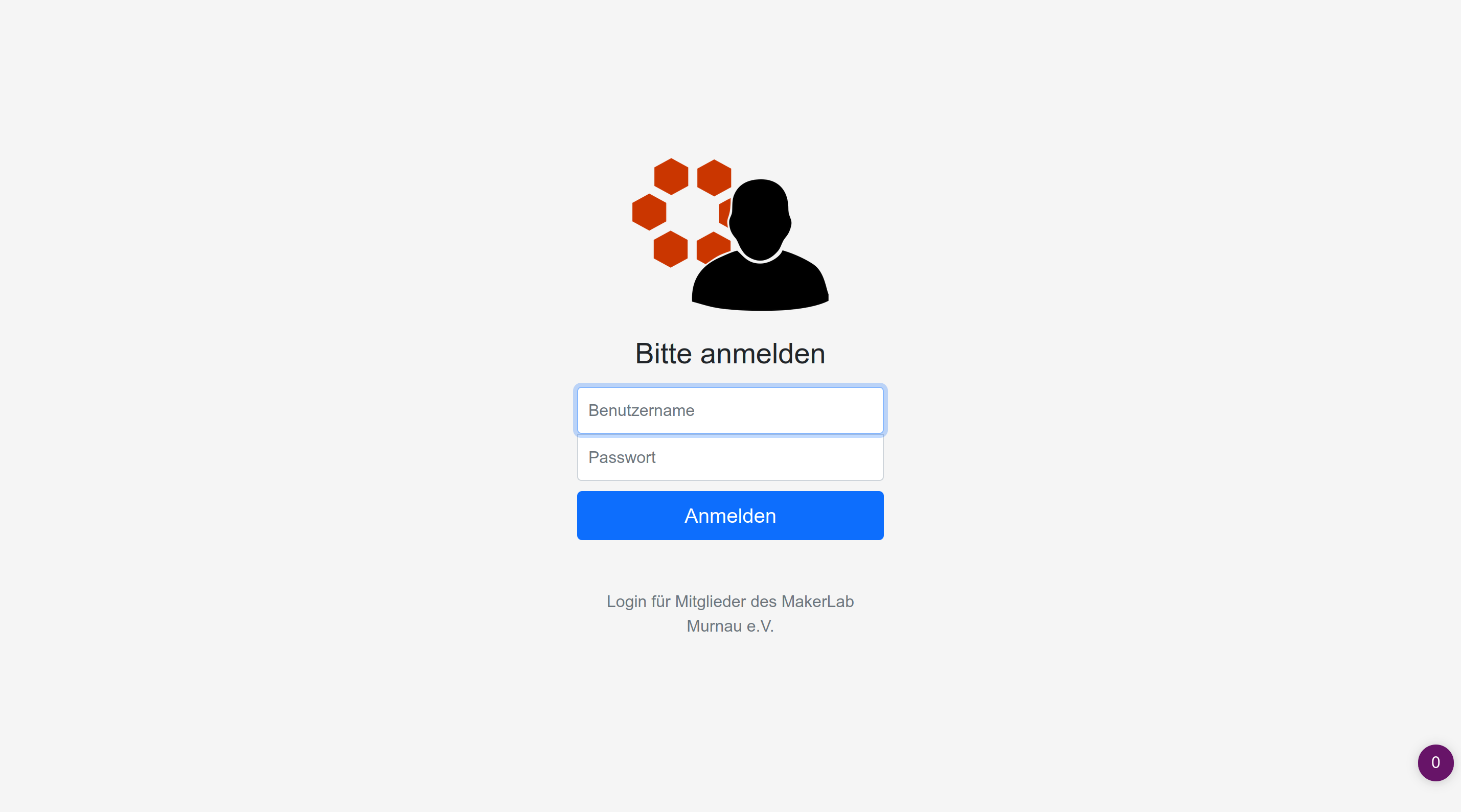
- Use OpenID-Connect user initial user authentication
The official installation method is using Docker:
- Create a folder for installation:
mkdir /opt/landingpage && cd /opt/landingpage
- Create the file docker-compose.yml with this content:
version: "3.7" services: landingpage: image: dorianim/landingpage restart: always ports: - "5080:80" volumes: - ./data:/data
- Adjust the port (default
5080) to your needs - Start the landingpage:
docker-compose up -d
- Done! You can reach your landingpage on
localhost:5080 - Adjust you
config.yamlin/opt/landingpage/data/config.yaml - [OPTIONAL] To setup ssl/https, please use a reverse proxy like nginx
To update, just go to your installation folder and pull
cd /opt/landingpage
docker-compose pull
docker-compose down && docker-compose up -dFor troubleshooting, take a look at the logs:
cd /opt/landingpage
docker-compose logs -fFor encrypted connections, there are two options:
- Use SSL:
- your host will have to look like this:
ldaps://<host>:636 - you will have to set useTls to false!
- Use startTLS:
- your host will have to look like this:
ldap://<host>:389 - you will have to set useTls to true!
In both cases your connection will be encrypted, and it will fail when there are certificate errors.
By the way: You can get your SSL certificate by running:
echo -n | openssl s_client -connect <host>:636 | sed -ne '/-BEGIN CERTIFICATE-/,/-END CERTIFICATE-/p' > ldapserver.pem
|
|
|
|


