- Http Login Bruteforce python script with WAF fingerprint and Web Protection fingerprint.
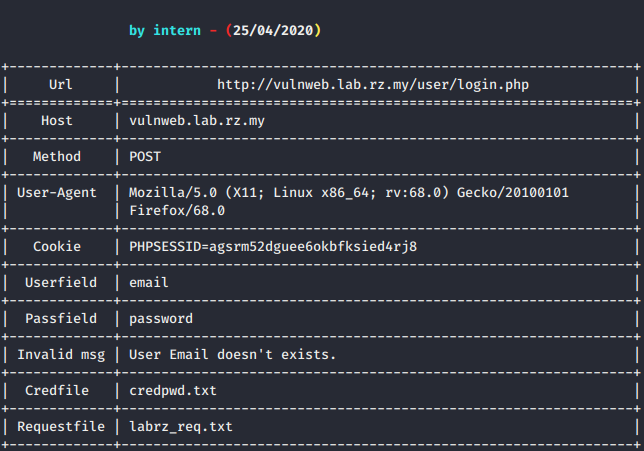
- request file from burp suite or any tool request intercept
- CREDENTIALFILE in pair of username:password format
- username field
- password field
- invalid message
- based on request or response headers.
- response page content.
-
Read request file from burp suite or any tool request intercept
-
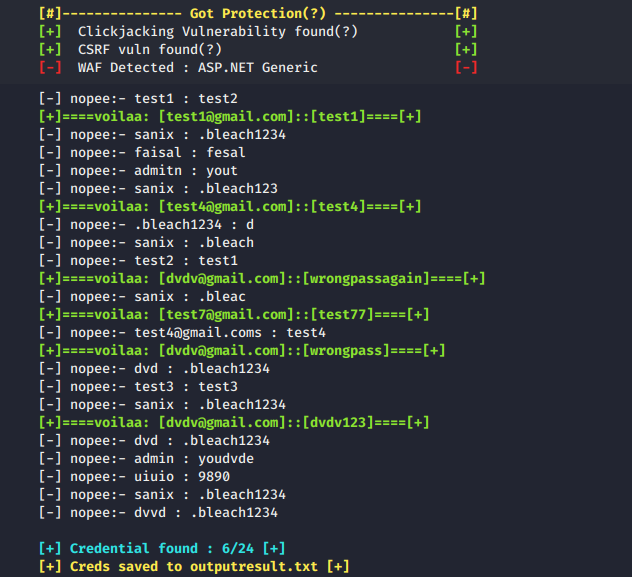
WAF fingerprint:
- Mod_Security
- WebKnight
- Cloudflare
- FortiWeb
- Imperva Incapsula
- GoDaddy
- ASP.NET Generic
-
Web Protection fingerprint:
- Clickjacking
- CloudFlare protection
- CSRF token
- Python 3
- git clone https://github.com/faisalfs10x/HttpWaf-Login-Bruteforce
- run 'bash install.sh' to auto-install module in requirements.txt
usage: httpwaf.py [-h] -r REQUESTFILE -c CREDENTIALFILE -u USERFIELD -p PASSFIELD -i INVMSG [-V]
Parallel Dictionary Login
optional arguments:
-h, --help show this help message and exit
-r REQUESTFILE, --requestfile REQUESTFILE path to requestfile.txt format from burpsuite request intercept is compulsory!!
-c CREDENTIALFILE, --credentialfile CREDENTIALFILE path to credentialfile.txt in pair of username:password format
-u USERFIELD, --userfield USERFIELD username field
-p PASSFIELD, --passfield PASSFIELD password field
-i INVMSG, --invmsg INVMSG invalid message in double quoted string
-V, --version show program's version number and exit