-
Notifications
You must be signed in to change notification settings - Fork 473
uMatrix 0.9.3.6 user-agent leak #771
Comments
|
Unable to reproduce. Your report lacks information and detailed step-to-reproduce, so I went with my own steps:
Result, the site thinks I am using Firefox 45 on Windows: I will reopen if you make a better case that there is an issue. You failed to:
|
|
Please. Reopened. I described in more detail. For me, this issue is a heartbleeding. |
|
Somebody else will have to investigate -- I can't investigate if I can't reproduce. I suggest you use another user agent spoofing extension meanwhile. |
|
Ok, I reproduce on FF53. Strangely, I can't reproduce on Nightly. |
|
The site's Content Security Policy does not allow inline script tags, this means uMatrix inline script tag to spoof window.navigator is not allowed to execute. Unexpectedly, uMatrix's inline script works with Nightly. It's unclear whether this is by design or not, maybe Nightly allows inline script injected by extensions? (would make sense since they are trusted by the user). |
|
I confirm. Firefox 55 does not have this issue. Firefox 54 and below are affected. |
|
I have a fix, but it's best called a "mitigation", it will work for this site, but there is no guarantee it will work for some other sites where there is a similar issue. It will work for this site because I created a fallback to But in the end, the reality is that I am seriously considering removing UA spoofing, it gives a false impression of accomplishing somethign useful. Turns out countering fingerprinting has become quite an undertaking, and partially spoofing some navigator entries does not accomplish much -- I rather remove this clumsy feature borne out of experimental code years ago before I understood fully all that was at stake. See for yourself using dev console, inspect In the end, UA spoofing and all other anti-fingerprinting mechanisms are best left to a specialized extension, and that will require a lot of work, this does not belong to a network request firewall like uMatrix. |
|
No.Please. Don`t remove UA Spoofing. I have not seen a good addon which could be given this job. |
It does not really prevent finding out which browser/OS you are using -- I rather remove it than mislead users into thinking the opposite. At the very least, the feature needs to be somewhere else than in the Privacy pane in the dashboard. |
|
:( |
|
Tested all the add-ons specializing in UA Spoofing. They all have the above problem. I ask you to reconsider your decision and find a proper solution to the problem. I certainly understand that your main direction is uBlock Origin but still. Please forgive me for persistence. |
|
The fix is in v1.0.1b0 on AMO dev channel. |
|
@gorhill Sure. |
|
I'm sure you are aware, that Ref: I wholeheartedly endorse that you drop the whole UA part for all the reasons you said. An earlier issue I raised (2 years ago?) was that JS did not match headers (fixed at the time by using UA JS Fixer or something add-on). Another issue raised by someone else was the real navigator values being leaked over iframes. The list goes on. There are so many "holes" and methods that add bits and raise entropy. I fully agree that this is left to a specialized extension and/or the Tor Uplift. Just my 2cents :) |
This is likely giving additional information with which to fingerprint users. i.e. if they see different UA for different requests they could assume µMatrix is installed. |
|
This is a common problem for every extension that tries to change the user-agent from inside the browser. |
The end result of the flawed UA spoofer was to accomplish the OPPOSITE of the intended goal. UA spoofing for privacy purpose turns out to be a whole complicated task on its own, and is best undertaken as a separate dedicated extension -- assuming it is possible at all. In any case, this had no place in a "Privacy" section in uMatrix, this was a bad idea to create this feature in the first place. It's never too late to correct a bad idea, and this is the purpose of this commit.

Just accidentally discovered the leak a real user-agent for which spoofing is responsible uMatrix.
In order to reproduce the leak it is necessary:
1: Go to https://mega.nz
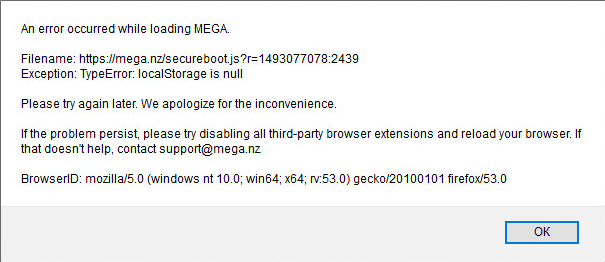
2: Open about:config in new tab and change dom.storage.enabled to false
3: Go back to the tab with https://mega.nz and you will see a window with an error and your real user-agent.
The text was updated successfully, but these errors were encountered: