-
Notifications
You must be signed in to change notification settings - Fork 176
09. 802.11 Network Selection Algorithms
- Each time a station connects to a WiFi network, ESSID is stored inside station's PNL.
- PNL is an ordered list of ESSID the station has connected to in the past.
- PNL also stores configuration information needed to establish a connection with those networks.
-
Passive Scanning = Client device listens for beacon frames from nearby access points. Client devices are typically configured by default to connect to networks within their PNL automatically. If this is the case, and the client device receives a beacon frame whose ESSID field matches an ESSID from the client’s PNL, the client will automatically connect to the access point that sent the beacon frame.
-
Active Probing = Client devices that use active probing continuously transmit probe request frames to determine what APs are within range, as well as what their capabilities are. Probe requests come in two forms: directed and broadcast.
-
Directed Probing: Clients that use directed probing will send out probe requests for each network in its PNL. It should be noted that directed probing is the only way of identify the presence of nearby hidden networks.
-
Broadcast Probing: Broadcast probe requests work almost exactly the same way, but are sent with the ESSID field set to NULL (i.e. "Broadcast ESSID"). This addresses the broadcast probe to all nearby access points, allowing the station to check if any of its preferred networks are nearby without revealing the contents of its PNL.
-
Important: Following attacks only work on open networks.
- Abuse Active Probing.
- This attack consists in dynamically generating Rogue APs.
- The AP listens for directed probe requests, and sends back directed probe responses with the same ESSID.
- The client then receives the ESSID, thinks he is near a network from its PNL, and connects to the rogue AP.
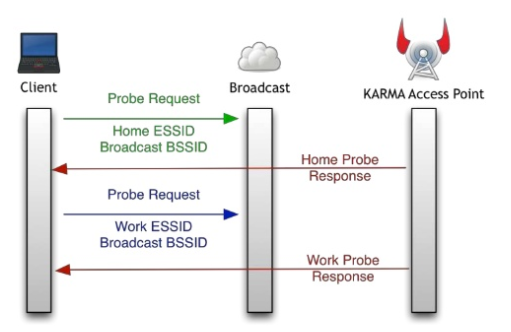
Ref: https://www.slideshare.net/sensepost/zacon-2015-zombie-mana-attacks
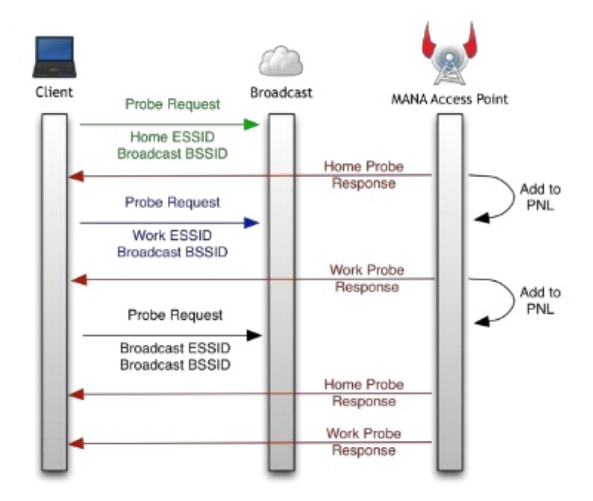
Improvement of KARMA attack in which the rogue AP reconstructs the PNLs of nearby clients.
When AP receives a Probe Request:
-
If Directed Probe Request:
- Add client's MAC to hash table,
- Add requested ESSID to that device's PNL,
- Respond with directed Probe Response (might not work on client if no response to Broadcast Probe previously).
-
If Broadcast Probe Request:
- Respond with Probe Responses for each of the networks ESSID in that device's PNL
Variant of MANA attack in which the rogue AP sends Beacon & Probe Response Frames for each ESSID in the union of all PNLs of nearby clients.
- If Directed Probe Request:
- Same as with MANA Attack
- If Broadcast Probe Request:
- Respond with Probe Responses for each of the networks ESSID in EVERY device (seen before) PNL (union of PNLs)
- Abuse Passive Scanning.
- Rogue AP broadcasts dictionary of common SSIDs, that the nearby WiFi clients have likely connected to in the past (i.e. are in PNLs), in order to force a connection.
-
Device ignores Probe Responses from APs that did not first respond to Broadcast Probe
- Circumvent this using MANA instead of KARMA
-
Device relies exclusively on Passive Scanning (no Active Probing)
- Circumvent this using Loud MANA or Known Beacons attacks
-
Windows 10 Countermeasures:
- Open networks are by default not added to the PNL.
- Clients will send a probe request frame after receiving the correct beacon frame.
- 01. WiFi Basics
- 02. 802.11 Specifications
- 03. WPS (WiFi Protected Setup)
- 04. WPA Protocol Overview
- 05. WPA/WPA2 Personal (PSK) Authentication
- 06. WPA/WPA2 PSK Traffic Decryption
- 07. WPA/WPA2 Enterprise (MGT)
- 08. Evil Twin Attacks
- 09. 802.11 Network Selection Algorithms
- 01. WiFi Interfaces Management
- 02. WiFi Connection
- 03. WiFi Monitoring (Passive Scanning)
- 04. Hotspot Captive Portal Bypass
- 05. WiFi Denial of Service
- 06. WEP Authentication Cracking
- 07. WPA/WPA2 Personal (PSK) Authentication Cracking
- 08. WPA/WPA2 Enterprise (MGT) Authentication Cracking
- 09. WPA/WPA2 Personal (PSK) Traffic Decryption
- 10. Basic AP (Manual Configuration)
- 11. Open Network (no passphrase) Rogue AP / Evil Twin
- 12. WPA/WPA2 Personal (PSK) Rogue AP / Evil Twin
- 13. WPA/WPA2 Enterprise (MGT) Rogue AP / Evil Twin