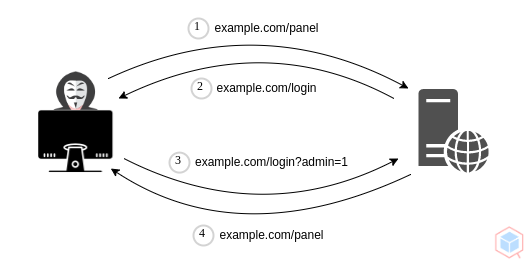
An adversary may gain access to data and functionalities by bypassing the target authentication mechanism
- Threat actor requests a web application interface
- Sever sends a login request
- Threat actor adds a parameter that bypasses the authentication
- Sever sends the web application interface
High
- Gain unauthorized access
- Validate access control
0b73c51c-728c-4005-a1f1-84e303bbac1e