Python3 script to generate portable TTP intelligence from a web-based report
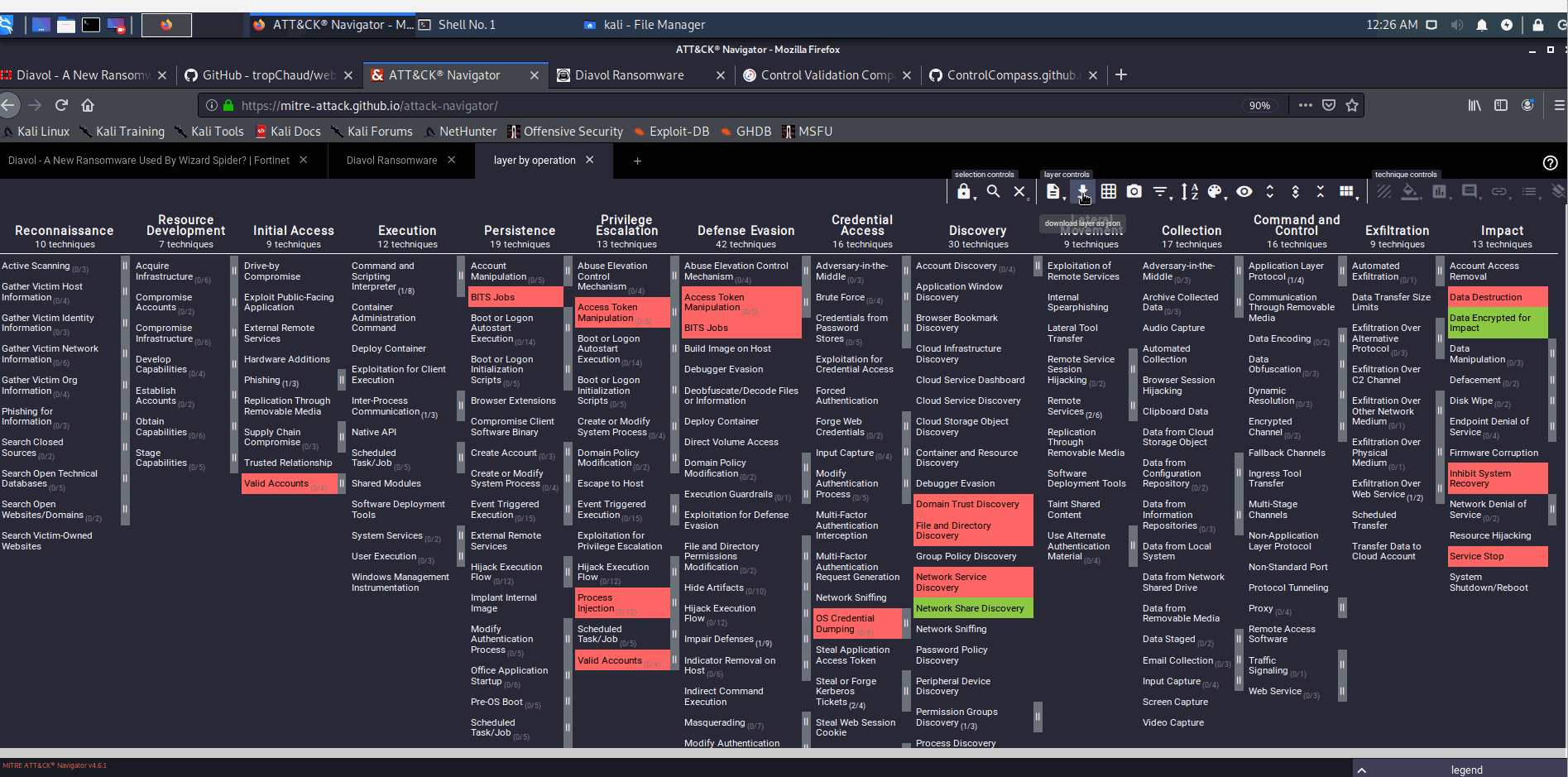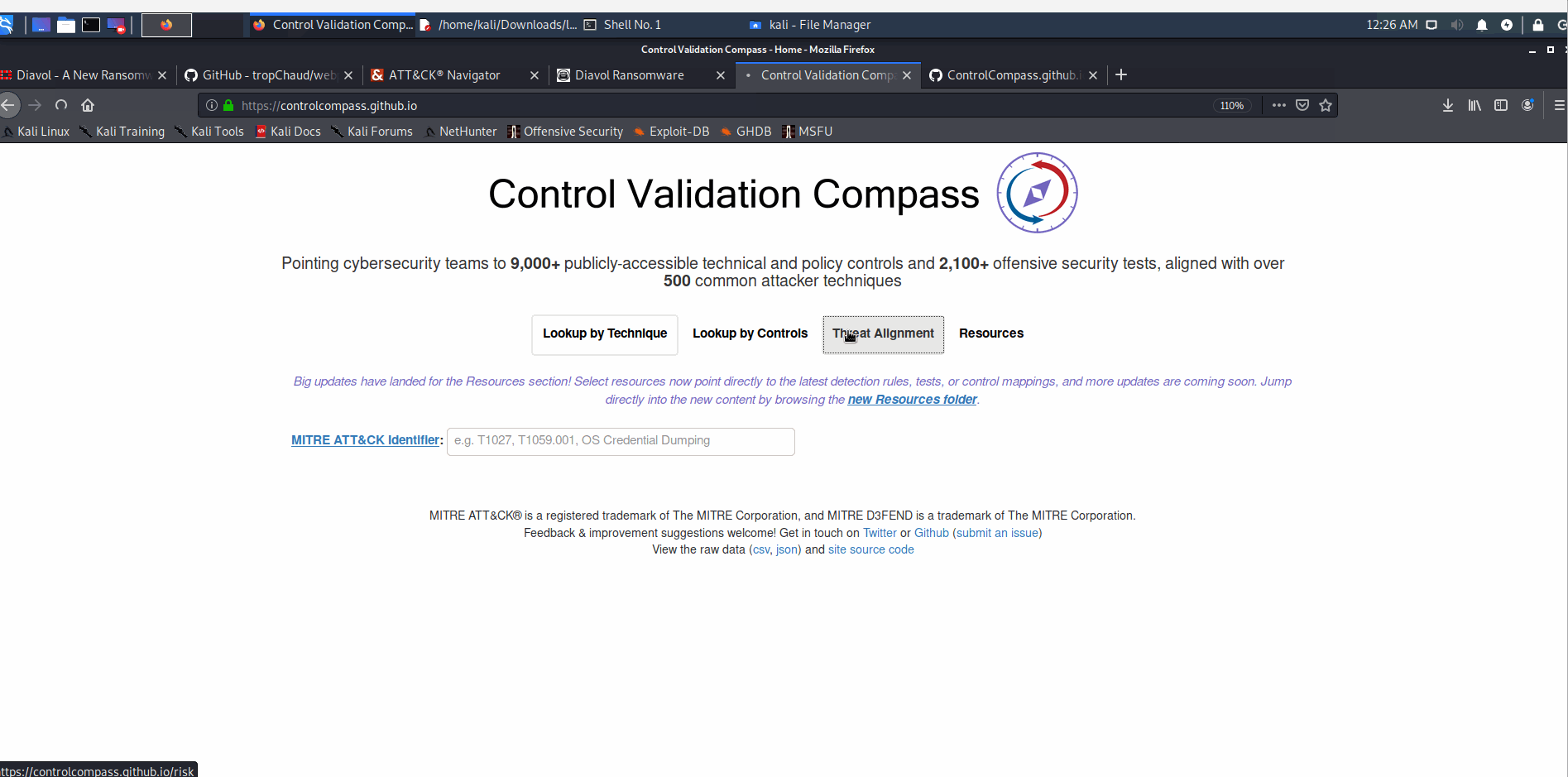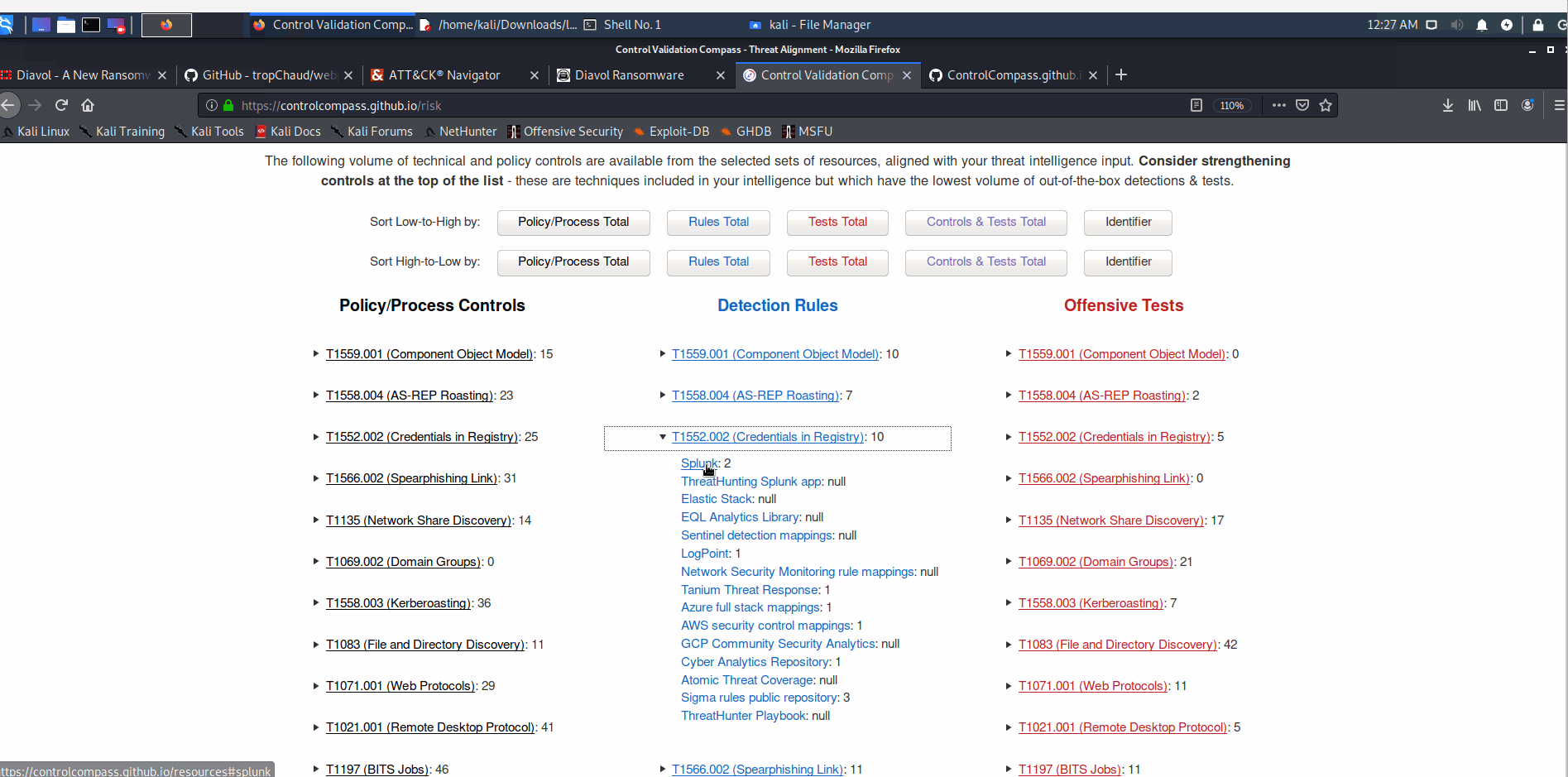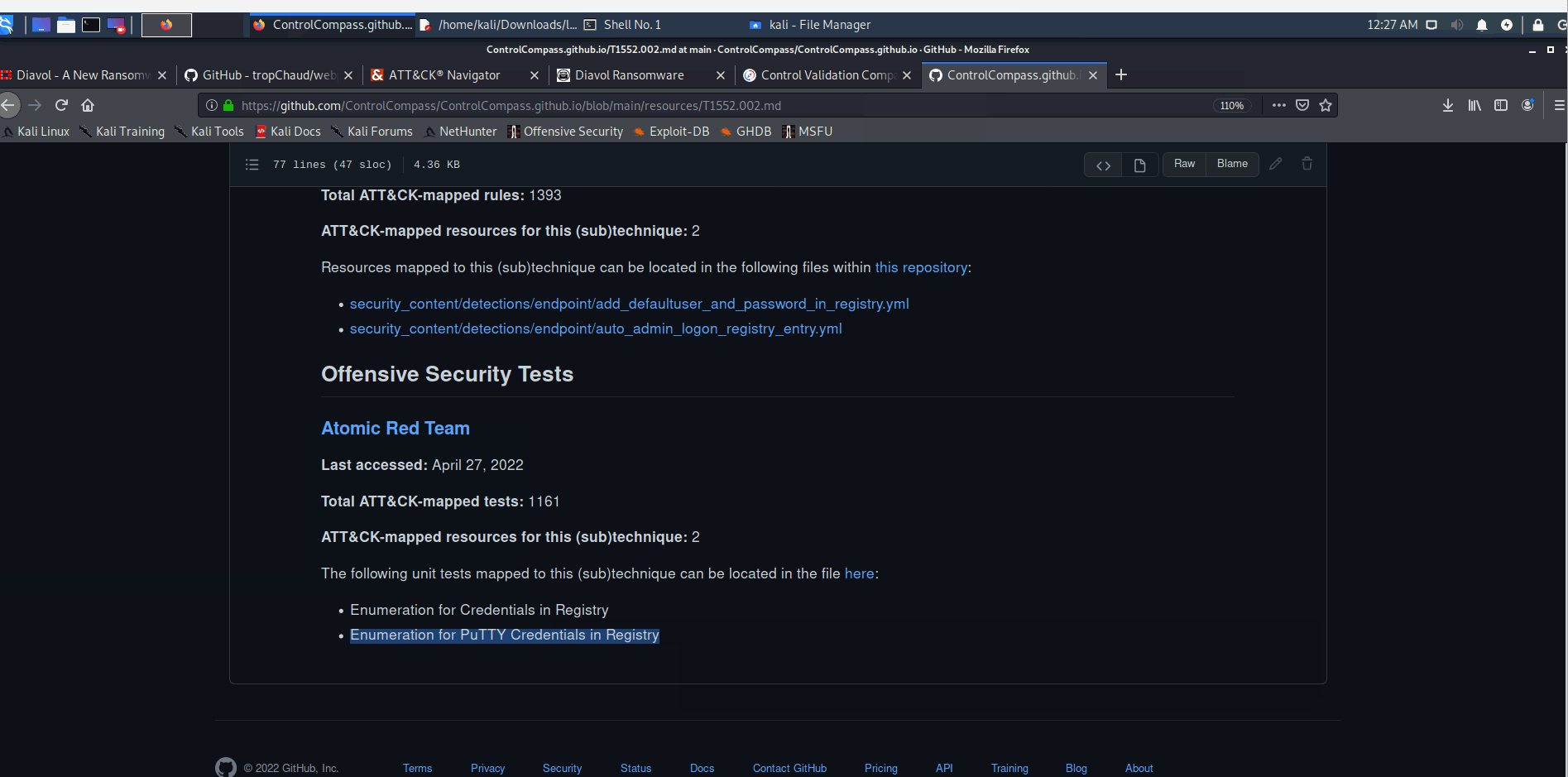
Tallies explicit mentions of MITRE ATT&CK (sub)techniques (e.g. T1027 or T1027.001) on a single html webpage, and outputs a .json file compatible for use with the ATT&CK Navigator visualization tool.
Note: The script currently only covers ATT&CK Enterprise techniques, but updates around Mobile and ICS techniques are being explored
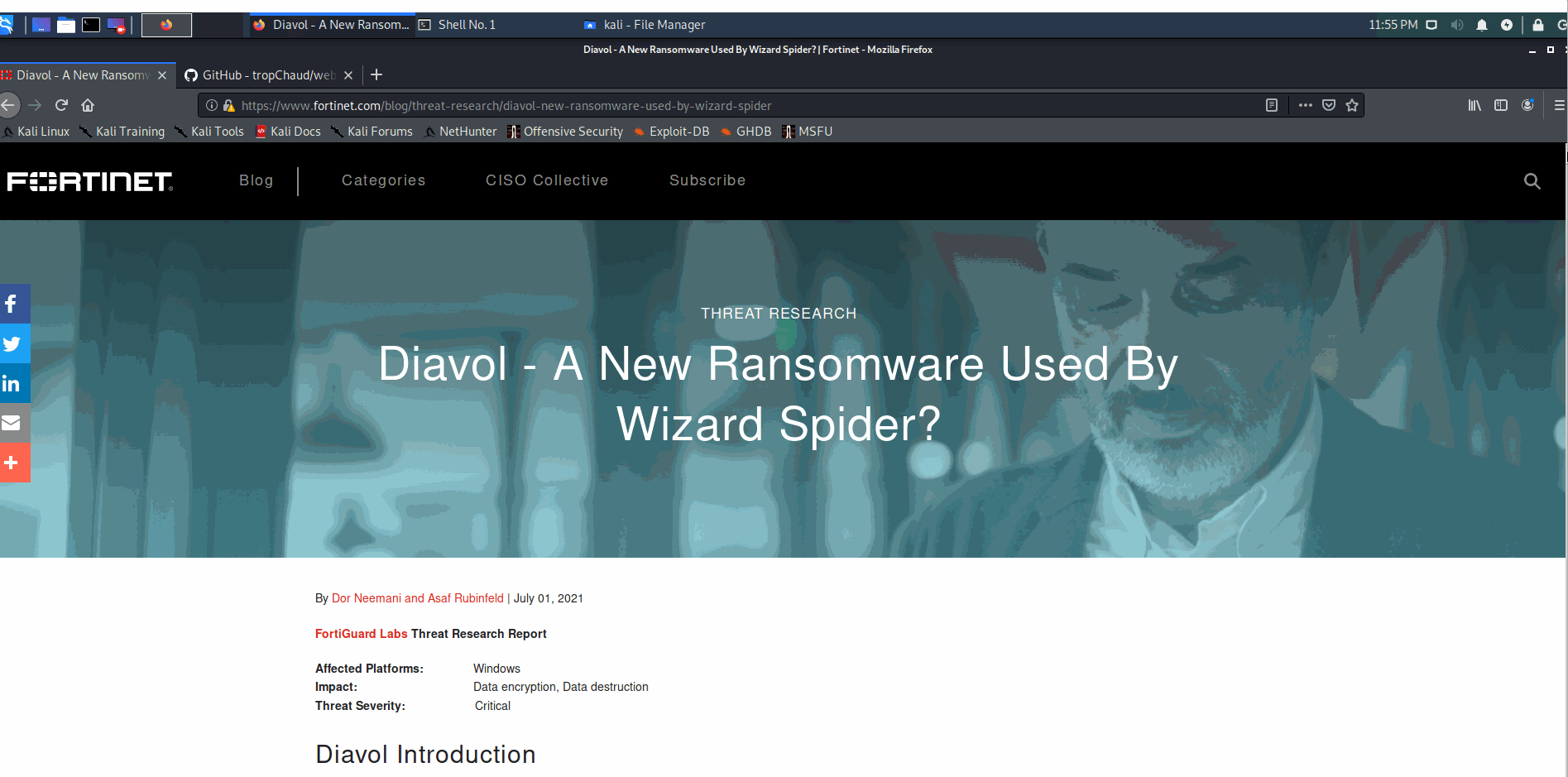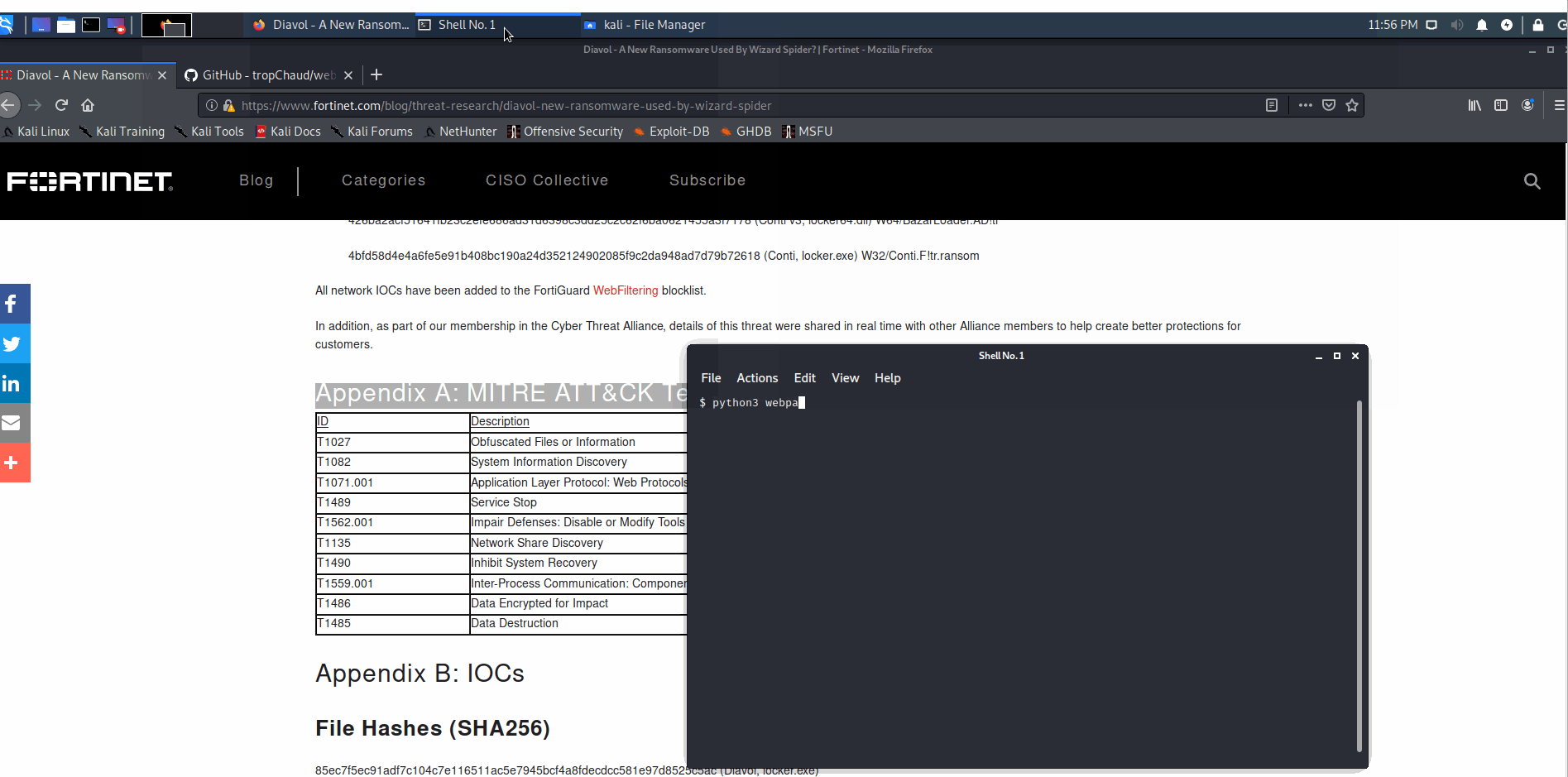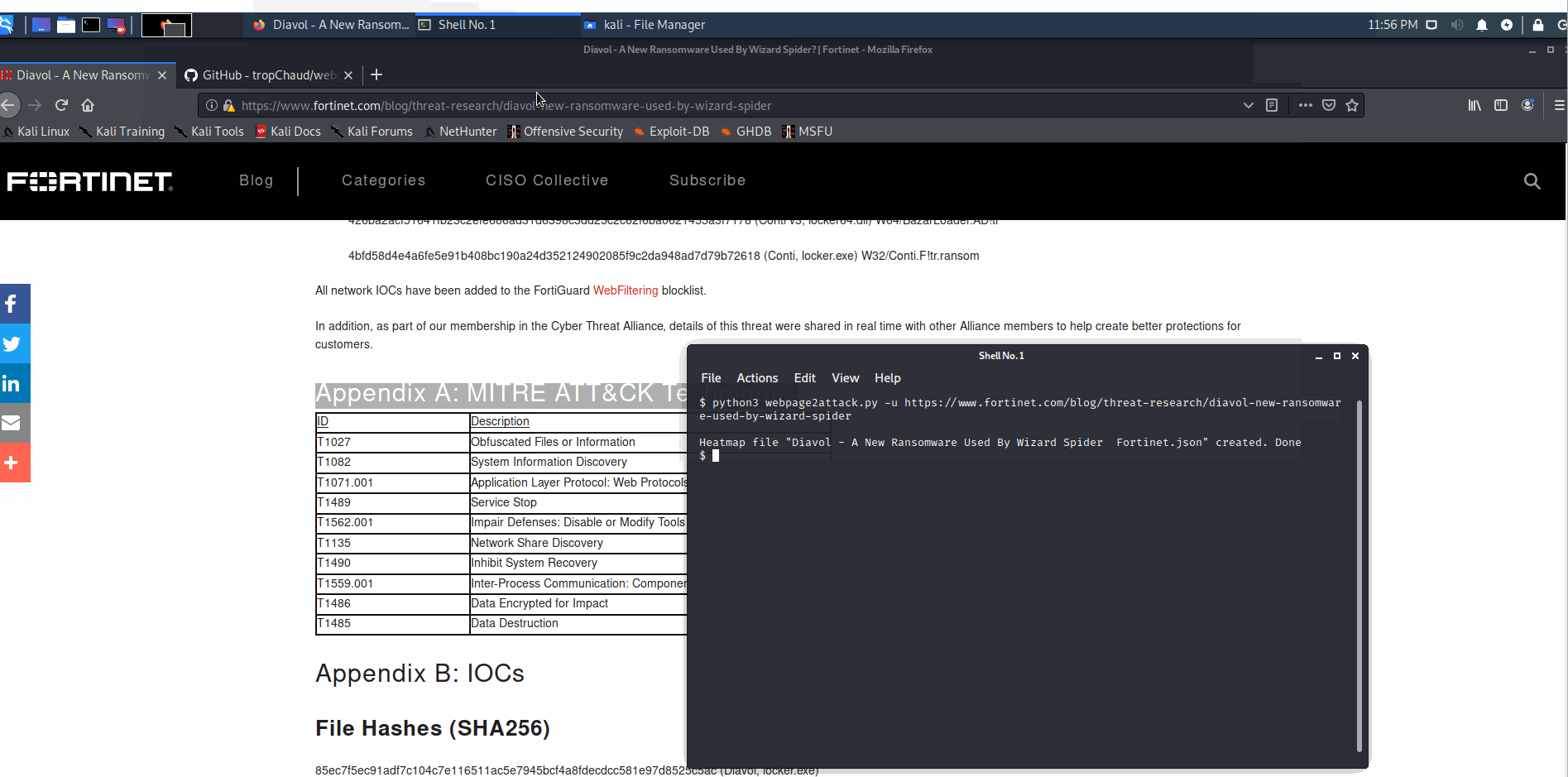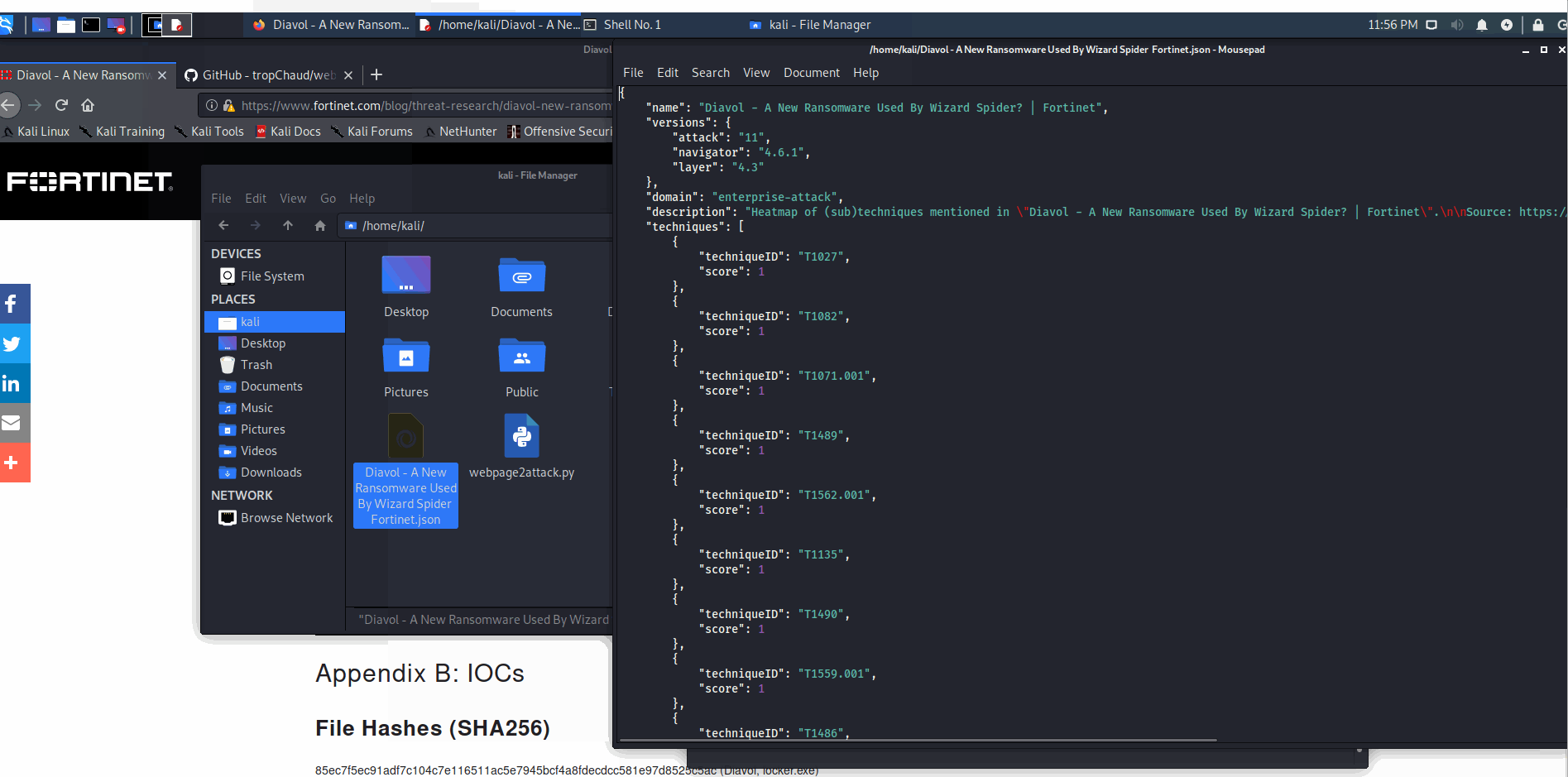
Quickly extract TTP identifiers from a given technical report, for threat intelligence analysis, visualization, and operationalization (e.g. paste the output json content in the Threat Intelligence dropdown here to identify potentially relevant controls aligned with each TTP).
python3 mitre2attack.py -u [your url]
Running the script:
Processing another report and combining the Navigator layers:
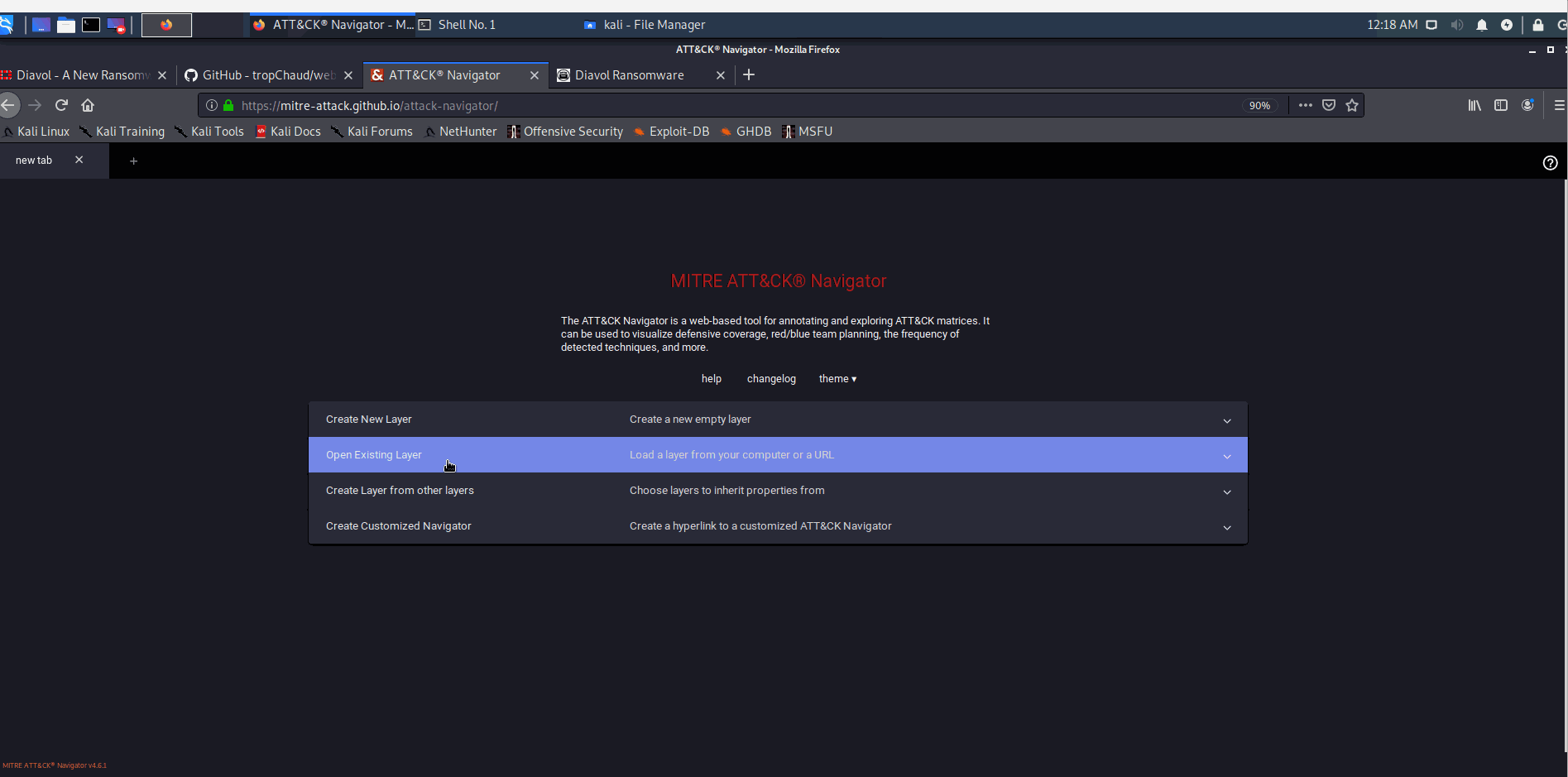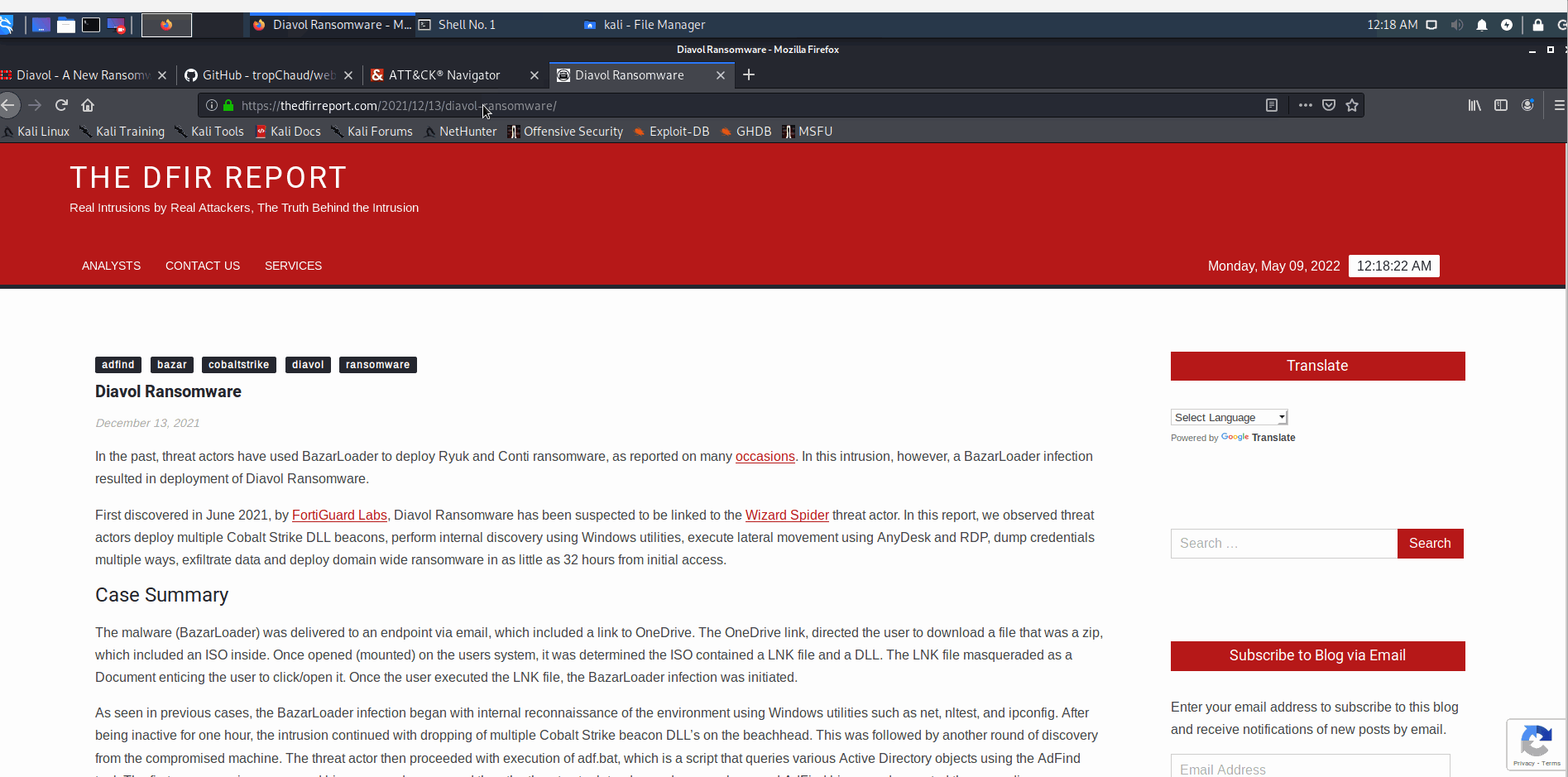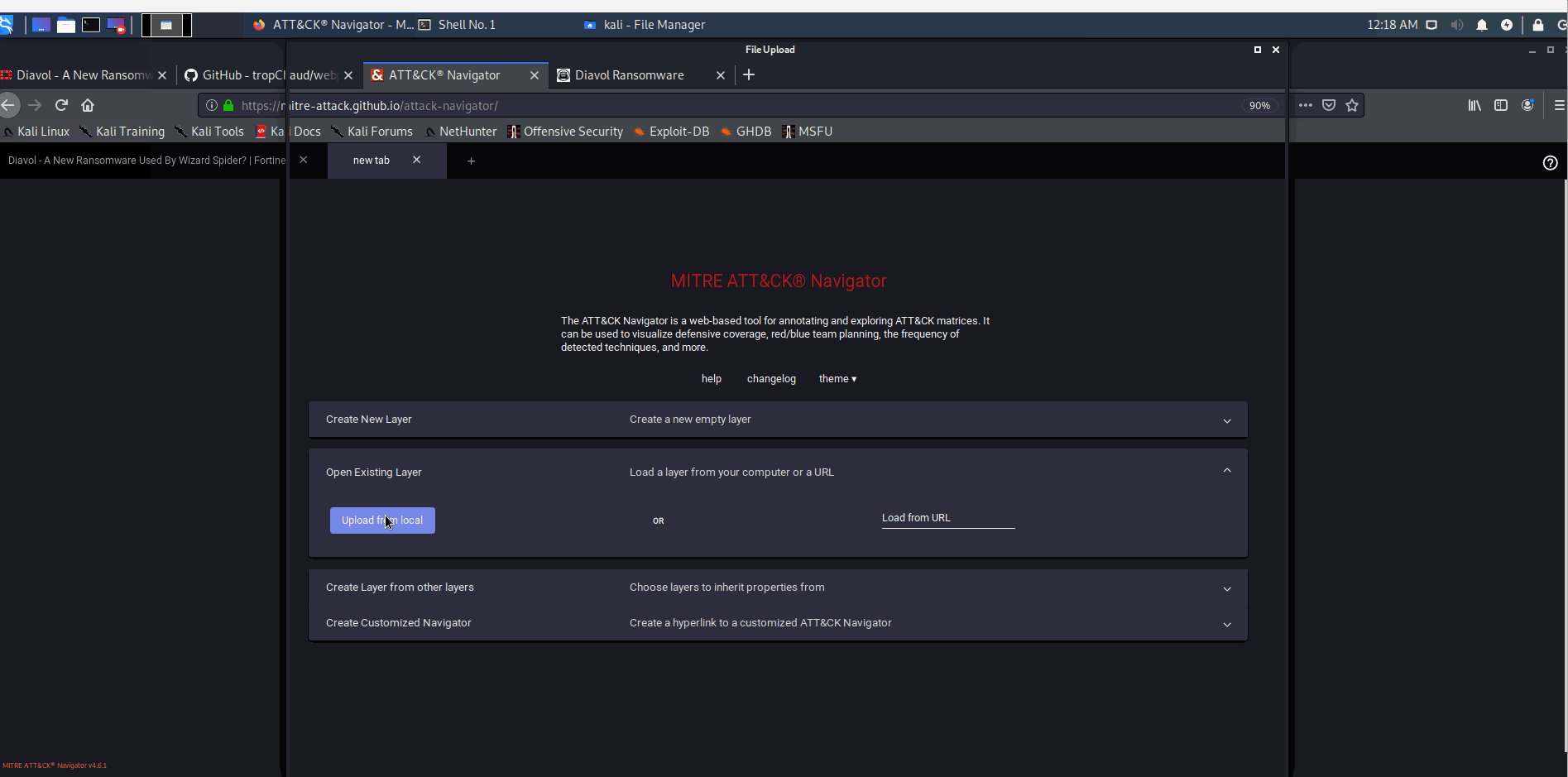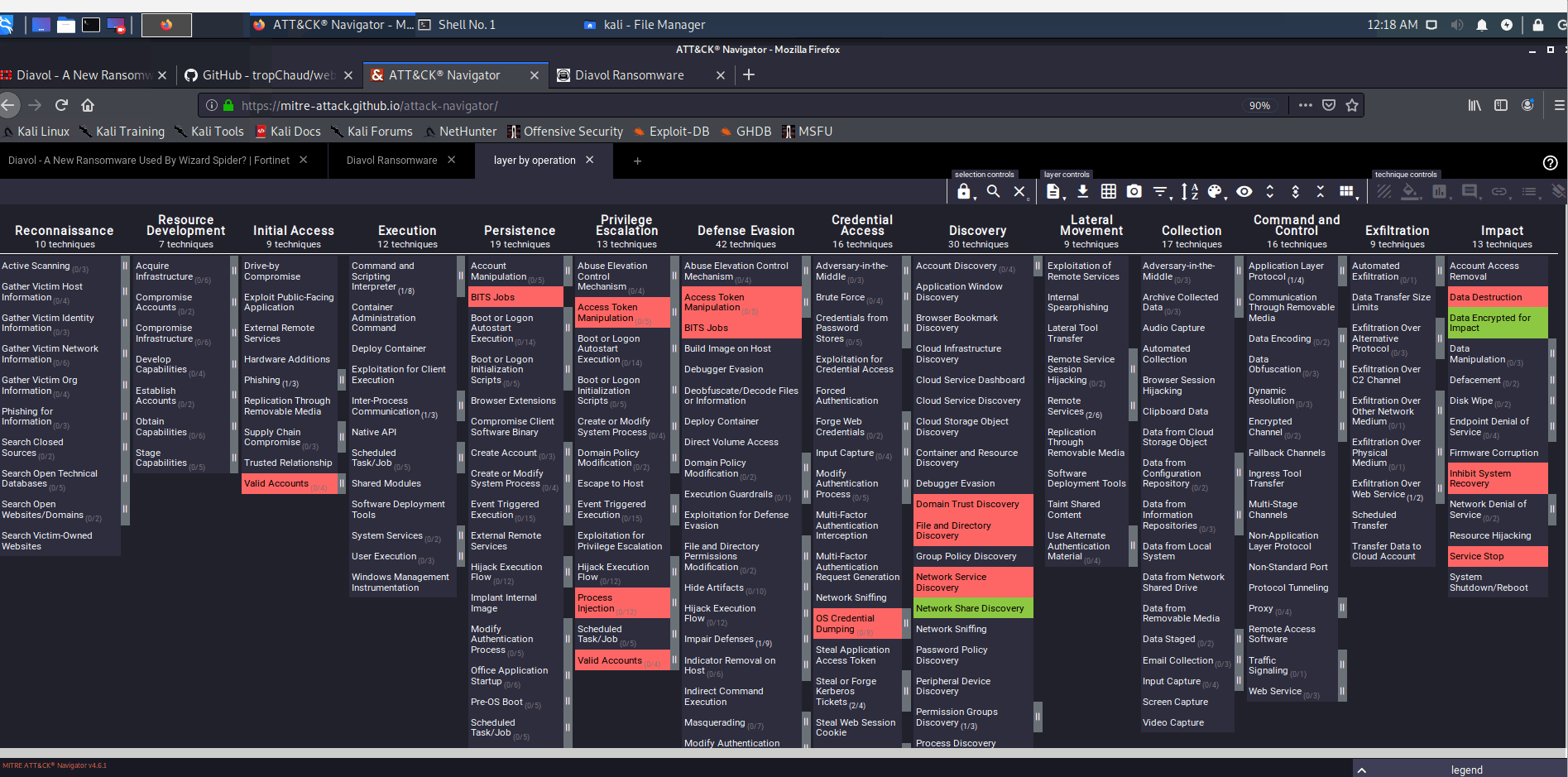
Exporting the combined heatmap to quickly identify potentially relevant detections and tests aligned with each TTP:
MITRE ATT&CK® is a registered trademark of The MITRE Corporation