-
-
Notifications
You must be signed in to change notification settings - Fork 951
New issue
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and privacy statement. We’ll occasionally send you account related emails.
Already on GitHub? Sign in to your account
Very bad performance on NVME SSD #136
Comments
|
It is problem not only for SSD. Due to this issue CPU speed does not make a lot of sense to estimate how fast disk encryption will be. UPDATE I had to switch my storage system to DiskCryptor solution due to this issue. The only drawback of DiskCryptor for me is no audits. |
|
Is there any news on this matter? |
|
@RcTomcat Unfortunatly I think it's not gonna change. |
|
No news on this task? I have the same problem: Without encryption (Windows 10, samsung ssd 960 evo m2 500gb): With encryption (AES, mounted file container) As you can see in the screenshots - the speed is less than 10-20 times. read more Are there ways to solve this problem? |
|
@InSys I'm curious how DiskCryptor performs on your system. |
|
I have the exact same issue, just on regular SATA SSDs. DiskCryptor and BitLocker both perform very well (maybe ~5-10% decrease in the disk I/O), but performance with VeraCrypt is just abysmal. And yes, it is noticeable in normal workload, especially when operating on many small files at once. For this reason I have been using BitLocker for now (because DiskCryptor seems abandoned and does not support GPT). I do not have top-notch hardware here but still... (AMD A10-7860K, 16GB RAM, 2 x SanDisk x110 256GB, Windows 10 LTSB 2016). |
|
Is there any effort to fix those ridiculous performance penaltys? Affect normal SSDs aswell not only NVMe ones. |
|
I noticed the same thing on a new laptop I planned to encrypt. I've loved TrueCrypt and VeraCrypt for a while now, but due to time constraints had to buy BestCrypt. I hope the devs get this figured out. |
Why do you need GPT if you do not have partition more than 2TB? |
GPT is required for disabling CSM, And disabled CSM is required for SecureBoot. |
|
BUMP. Also how is Trim and Provisioning effected when software FDE is implemented? |
|
I just encrypted my system drive with VeraCrypt (ver 1.23) on the almost identical HW configuration as listed in the first post. I see the same slow read speed in Samsung Magician and in CrystalDiskMark. Sequential read is down to 20% . Bitlocker compared to no-encryption is almost identical. Now the good news. When I measured the real-time for programs to open, there wasn't much of a difference. Lightroom and Photoshop both take approx 2 seconds to be ready, just like with no encryption. Starting another windows 10 from Oracle VM VirtualBox takes 21.5 seconds with no encryption and 23 seconds with Veracrypt. All programs are installed on my Samsung EVO 960 500GB and the startup time for each program is measured after a fresh system reboot. |
|
I know it costs money, but I'm very happy with BestCrypt. Also, the older DiskCryptor works great for a MBR SSD if you don't mind disabling UEFI and all the modern settings. |
|
yeah but who wants to use something not open source to secure their shit |
|
Most people. We use Sophos Safeguard at work. Many use CheckPoint FDE. I build VPN's with Cisco, Fortinet, Palo Alto all day long. AES is a standard. Being open source is irrelevant. |
Such tools like FDE, encrypting messengers and so on MUST be open source! P.S. Let's stop flooding here. |
|
I've just ran into the same problem. Unfortunately I can't see a solid alternative... Bitlocker isn't available on all Windows versions and DiskCryptor is dead. Btw, does your SSD also show a disk activity of 100% when only writing about 20 MB/s with a response time of a couple of thousands ms? I do have this problem when moving things from a HDD to encrypted SSD. |
|
bxkx, the people here would tell you not to use Bitlocker. Cuz it's not open source. sigh... |
|
Plus bitlocker uses hardware-based encryption... which has it's own problems. https://www.howtogeek.com/fyi/you-cant-trust-bitlocker-to-encrypt-your-ssd-on-windows-10/ |
|
VeraCrypt tends to be slower for random read/write access because of its driver architecture and the way it handles IRP for I/O. Because VeraCrypt supports file containers (which is not the case of DiskCryptor and Bitlocker), it can not handle IRPs in place and it must create a new IRP to the holding file for every read and which in turn causes a thread context switch. This explains the performance drop. VeraCrypt uses the same IRP logic for both file containers and disks. Ideally, we should handle IRP in place for disks without context switch to have maximum performance and this requires a big architecture in order to keep both IRP logic working at the same time (a user can mount a file container and a disk simultaneously). Some time ago I have implemented a prototype with a dual logic for file containers and disks but there was huge stability and reliability problems and I could find an easy solution for them. Clearly the next version of VeraCrypt must address this and I hope there will be enough resources to work on this. Of course, external help is welcomed for such complex technical task especially that we want to keep file containers support. |
|
@idrassi thank you for the explanation! |
|
It explains a lot, but regarding this:
All my above posts are about sequential read and write. |
|
Is there any update about the issue / an estimated release date for solving this issue? VeraCrypt is a great software and I would never trust Bitlocker in any way. EDIT: So if there would be two different IRP paths the performance suffer would still exist for containers. So If you have for example a D: drive on a fast storage you should not create there a container and mount it, but instead encrypt the whole device and mount that for maximum performance. Right? |
|
Bonjour @idrassi, based on your comment about IRP, what about having 2 separate "versions" of Veracrypt, one that supports both disk and file as you envision and one that implements IRP in place, supports only disk container and doesn't incur such performance loss. |
|
@steamp0rt — it is possible to disable hardware encryption in group policy. |
|
Any Updates here? This is a really high performance impact |
|
I want to donate for the project, but the only problem stopped me is this issue. We can think in 2 ways : |
|
Too bad. Wanted to use veracrypt. Would have happily donated some money. This makes the project unusable. |
I must partially disagree. VeraCrypt is not unusable. There is no trustworthy alternative for Windows. By "trustworthy" I mean "open" + maximally realiable with bulletproof stability and FULLY compatible with Win10/11. The problem of low speed has no notable impact during office-like usage. |
Because everyone knows there is no real alternative. But to deal with their frustration, they start crying instead of being thankful that awesome ppl have put a lot of effort, time and money into a open-source project that does a great job and even is free for everyone😋. Crying is just trendy these days I suppose😅. |
|
@TheRealKasumi |
|
@PhamHoangLong Also regarding responsibility… it’s not like something is really broken. In facts it is working perfectly reliable and stable. So in the Ende it is nothing more than a optimization problem. And finally… donating money to open source projects to support them is a nice thing ofc. I am doing it myself regularly. However I feel like you are highly overestimating your impact there. Also it shouldn’t make you feel like you can then decide over other ppl and how they spend their time. So sorry kid, I don’t agree with some points there. No matter if you dislike that or not, that’s my opinion😋. |
|
Just use Linux with LUKS :P ok but seriously - we need to find ppl who will fix that and pay them. |
|
I made a video for people who just want an outline of this thread with the thought that this issue needs more publicity... |
|
Maybe it would be easier to just merge functions from DiskCryptor into Veracrypt and use funding to get an audit on these code parts. The German developer who took care of DiskCryptor also seems to be willing to develop it further if he gets some monetary compensation. |
|
The changes that have been made since the release of version 1.25.9 indicate that this project is far from dead: https://sourceforge.net/projects/veracrypt/files/VeraCrypt%20Nightly%20Builds/ I still hope that this will be solved, since it's a serious issue and NVMe drives are becoming more and more popular, but I can understand that it can be very difficult, if it requires a change in architecture, especially for a security software where you have to make sure that any change doesn't introduce any new vulnerabilities. |
|
Does this issue affect Linux device containers encryption too? |
|
@idrassi This particular issue/feature request remains to be by far the most commented-on issue on this repository, and I doubt there is any fix/feature that is more sought after than this by VeraCrypt's community. You mentioned before that you had previously attempted a work around to improve VeraCrypt's performance but it didn't work out in the end due to reliability problems. Is there any more development happening in that direction in the background so that hopefully this performance problem could be addressed sometime in future, or is it a lost cause? |
|
Let me think a bit: if "suddenly", as by miracle, VeraCrypt appears with a solved problem, I'd rather wait for the evaluation of the "purity" of the source code... |
|
Hey @idrassi, |
|
I'm about to switch to PCIe 4.0 NVMe drives on two systems. Is this still an issue? One of those systems can not afford the slowdown. Which means I will finally have no other choice than to surrender to Bitlocker. |
|
Don't forget about DiskCryptor. I have switched to it a few years ago. It has less functionality than VeraCrypt and is Windows-only - but it is open source and is specifically designed for system volume encryption and encrypting whole partitions in general, and as such does not suffer from the performance issues. On SATA SSDs and on older NVMe drives it gives almost full speed (vs no encryption). Haven't used the newest ones yet. However, over a year ago I have encrypted with DiskCryptor a virtual 100TB image formatted as NTFS, delivered by Synology ds1821+ via iSCSI with 8 physical 20TB IronWolf Pro disks in RAID6 via 20 GBit dedicated link. I'm using it daily since - no issues so far! It doesn't reach 20 GBit for some reason, maxes out at about 4-6 GBit sustained read/write (probably because I haven't used NVMe cache yet) but it is still a lot faster than VeraCrypt. |
|
I'm no developer but I think one of the main performance penalties come from the fact the Veracrypt encrypt the whole drive (Its not NVME related, its probably NAND related). Keep in mind Veracrypt is from a time HDD was common. When a drive is 100% full u have performance issues. Maybe a workaround could make ~25% of the drive unavailable and unused. So the SSD isn't "full" and the performance should heavily increase compared with 100% usage. 25% less amount of space is a noticeable penalty and maybe 10-20% "hidden" space is enough to dodge the major performance penalty. I think its worth to test this and this change doesn't affect the cryptographic way how Veracrypt works. P.S.: I would also love to donate if Veracrypt become useable again in an acceptable way on NVME / SSD drives. |
It doesn't seem like this is the issue. But you can easily test it by using your SSD manufacturer's software to enable over-provisioning and have some percentage (20-30% if you want to be extreme) of the drive reserved for that. (Although I think high-end SSDs already have some over-provisioning built into the drive by default that you can't even turn off, as well.) Then Veracrypt won't even see that space on the drive. If you actually find a big performance difference, please report back! |
|
Tested with Samsung SSD with OP 20% and without OP many month ago. The speed results did not differ. |
Nope, the exact reasons have been explained long time ago by the developer himself in the comment above: #136 (comment)
This would not help, unfortunately. I'd assume that the reverse would be helpful instead: paying for the development of the feature upfront. Provided it is not easy, it would also not be cheap though. |
|
@idrassi I unterstand that IRP handling under Windows (e.g. Windows 10) is not perfect. But why does performance drop down after some runtime/data written/data read (e.g. 50GB with NTFS) from e.g. ~10MByte/s to ~200kB/s. |
|
~10MByte/s to ~200kB/s? |
|
You are talking about MBit/s and not MByte/s? If MBit/s, then it is about in the same range in MByte/s (sometimes it goes up to 20MByte/s). To be precise: it happens with several WD Elements 5TB USB devices but also with several Samsung T7 Portable SSD - 2 TB USB devices. |
MEGABYTES per second. Sorry Im NOT talking about external USB stuff (I have missed, that you are) but about internal NVMe drives. USB stuff is always much slover. Im not using another external drives than GB LAN devices. |
|
I am thinking about deploying Veracrypt Full Disk Encryption on an (very) Old System with a small SSD. The performance seems to be quite bad indeed. I know most of the Following Description is NOT for Windows, but I still believe there might be something similar going on. I wonder if the Issues outlined here are similar to what happens in the GNU/Linux World (and maybe also FreeBSD) with ZFS: there is a HUGE write amplification going on (depending on file size and ZFS recordsize/volblocksize Dataset-ZVOL Settings) especially when running KVM Guests (Proxmox VE Host with ZFS, Guests typically using EXT4 as a Filesystem using a ZVOL Virtual Disk). The Write Amplification can easily reach 20-50 x (meaning a fairly small 10 GB/day write inside a VM can result in 2000 - 5000 GB/day being written in the NAND) !!! And it's also related to IOPS: heck I can't even use One helper could be to turn off A quick Google Search brings up this to Disable Access Time on Windows. In this way, each time you READ a file, you will NOT cause an additional WRITE. That will improve IOPS Performance and also reduce the SSD Wear/Tear. The other possibility is that the clustersize (Unfamiliar with the Windows Term, sorry) is not configured Correctly. Just like ZFS So, when you combine the two, it might look as follows: you READ one (in reality: A LOT) File of say 6kB. Maybe your clustersize is set to 64kB. Just to update the Access Time ( And maybe (on top of that) Veracrypt has ANOTHER value of sector/block/cluster size than NTFS ! Then you will have to write 64kB in another portion with the updated timestamp. And maybe TRIM is also not activated, so cleanup will be extremely slow. Can anybody Benchmark if Write Amplification is what is causing the Issue here ? I mostly gave up on Windows, but I believe there are some Experienced People around here that could help 👍 ! EDIT 1 I suggest doing this with small Files as random I/O and IOPS falls much faster than sequential Writes. There is also more write Amplification and "fragmentation" / Overhead with small Files as well. But of course, while doing this test, make sure that there is no significant "other stuff" going on (e.g. Antivirus Scanning, File Copy, several other Processes running, etc). |
@idrassi Can you post the commit(s) for the prototype so others can review and potentially help? |
|
Figured I'd post my experience as well. Because SSD Model seems to be important, I am using a TeamGroup MP34 SSD as my boot drive. CPU has AES-NI capability. |
|
I personally would be happy with a non-container version of VeraCrypt that can only mount partitions but at full speed. |


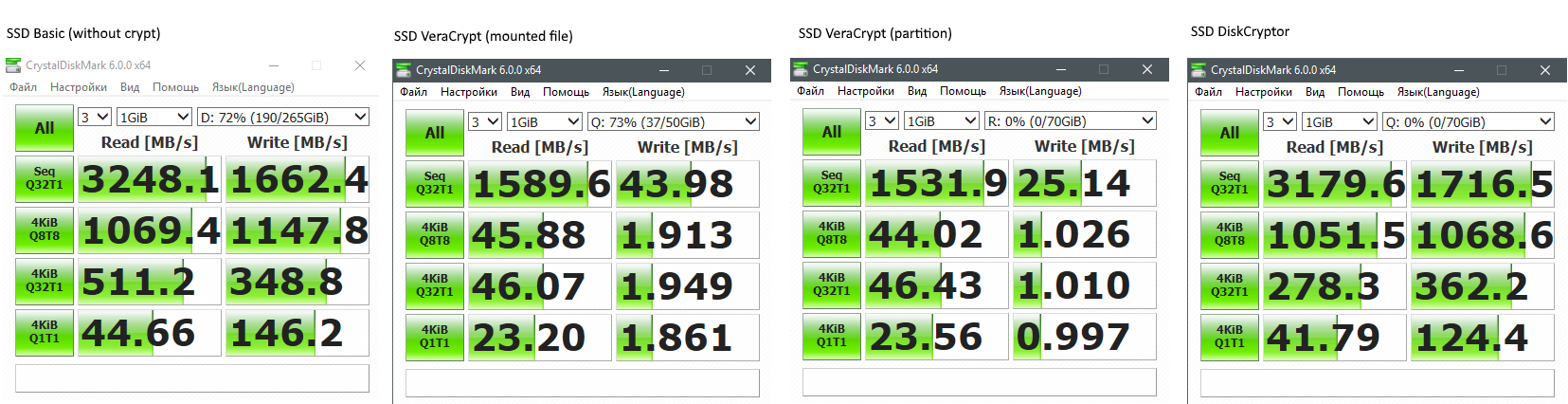






Hi,
Please don't take that as a complain, I only wish to help improve the software so I can use it.
I achieve very bad performance on Windows 10 LTSB 2016 with a Samsung EVO 960 250Gb and Veracrypt AES encryption:
Before :
After :
My hardware :
I7 7700k @ stock
16Gb Corsair DDR4
Samsung 960 Evo 250Gb with up to date Samsung NVME driver
Windows 10 LTSB 2016 up to date
Veracrypt 1.19 64 bits
Veracrypt Benchmark :
How can I manage to get close performance to non encrypted drive ? Is this even possible ?
Thanks and best regards,
Nicolas
The text was updated successfully, but these errors were encountered: