-
Notifications
You must be signed in to change notification settings - Fork 11
Remove trailing slash in server URL #169
New issue
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and privacy statement. We’ll occasionally send you account related emails.
Already on GitHub? Sign in to your account
Conversation
|
Looking at this, I'm just thinking of different edge cases and wondering if there's any way we can have a more friendly error message when someone gives a bad hostname (e.g. "writefreely" or "write.freely" or "write.as//" or "write.as/matt"). Do you think that'd be pretty involved? I'm just thinking about how we make this as robust as possible, and handle a wide variety of invalid inputs, rather than just this one particular case. |
We could try extending NSDataDetector to check if a link is valid — there's an example here that seems to be more useful for our use case than, for example, checking against a regex. However, that won't catch the "write.as/matt" case, because that's a valid URL, so I guess we'd still have to check that individually. I'd probably just validate that similar to the trailing-slash case: if Right now we just rely on getting back an error after sending the login request to the server to trigger the If that sounds like a good plan, I'll edit the linked issue's title to be "Make server URL validation more robust" for this work. 👍 |
|
Could you just parse the hostname out of the user input, and use that? Here's an example of what I mean, written in Go. I believe Swift provides similar URL parsing abilities? The critical goal here is that the app helps the user enter in the correct Instance URL (i.e. a valid URL and the correct instance). So I think the ideal UX would be: the app takes the Instance URL, automatically makes it valid, and then only ever complains to the user if they entered in a URL that isn't a WriteFreely instance. So once we have a valid URL, are we also showing a specific error message that would help them to this end when the |
|
Perfect, that clarifies for me. We can use URLComponents to get the protocol and host, which will return |
Turns out that, according to URLComponents, Let me find a workaround, maybe using the NSDataDetector option above. |
|
I guess that makes sense if you have a local server named |
|
Yeah, that's what I think we have to do. NSDataDetector recognizes the same as a URL, so we can't count on that. Which, as you point out, makes sense. I imagine that there's some case where a string is not considered a valid URL (like emoji?), so there's error handling that'll catch this and present the following alert: Otherwise, we just have to let the app make the request and see what happens. |
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
Good to go! Thanks.
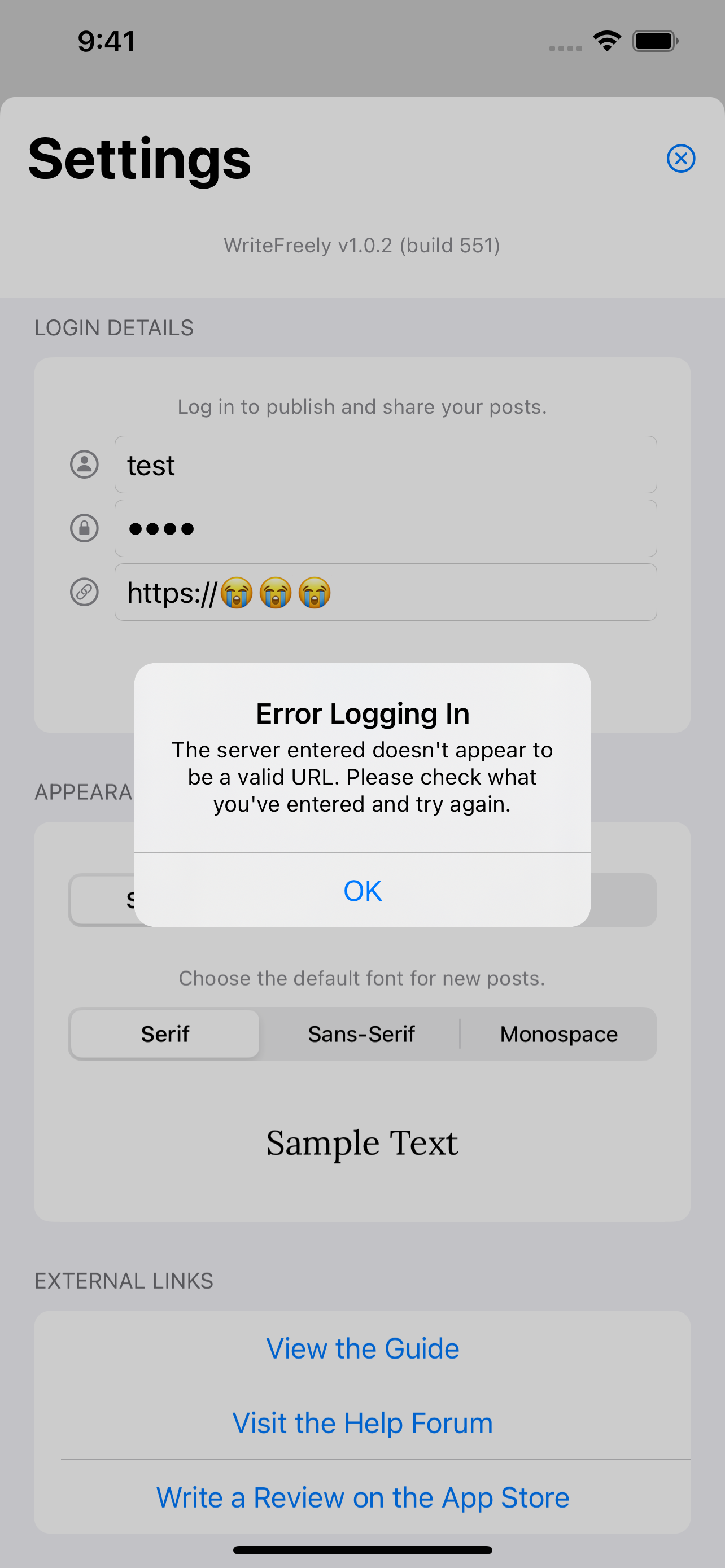
Closes #105.
This PR includes some cleanup. It turns off smart-dashes for the iOS body-text editor (to match the Mac app's behaviour per #168), and refactors the WriteFreely model into four files: