Twig Sandbox Escape by authenticated users with access to editing CMS templates when safemode is enabled.
Moderate severity
GitHub Reviewed
Published
Nov 22, 2020
in
octobercms/october
•
Updated Feb 1, 2023
Description
Reviewed
Nov 23, 2020
Published to the GitHub Advisory Database
Nov 23, 2020
Published by the National Vulnerability Database
Nov 23, 2020
Last updated
Feb 1, 2023
Impact
An authenticated backend user with the
cms.manage_pages,cms.manage_layouts, orcms.manage_partialspermissions who would normally not be permitted to provide PHP code to be executed by the CMS due tocms.enableSafeModebeing enabled is able to write specific Twig code to escape the Twig sandbox and execute arbitrary PHP.This is not a problem for anyone that trusts their users with those permissions to normally write & manage PHP within the CMS by not having
cms.enableSafeModeenabled, but would be a problem for anyone relying oncms.enableSafeModeto ensure that users with those permissions in production do not have access to write & execute arbitrary PHP.Patches
Issue has been patched in Build 469 (v1.0.469) and v1.1.0.
Workarounds
Apply octobercms/october@106daa2...7cb148c to your installation manually if unable to upgrade to Build 469.
References
Reported by ka1n4t
For more information
If you have any questions or comments about this advisory:
Threat assessment:
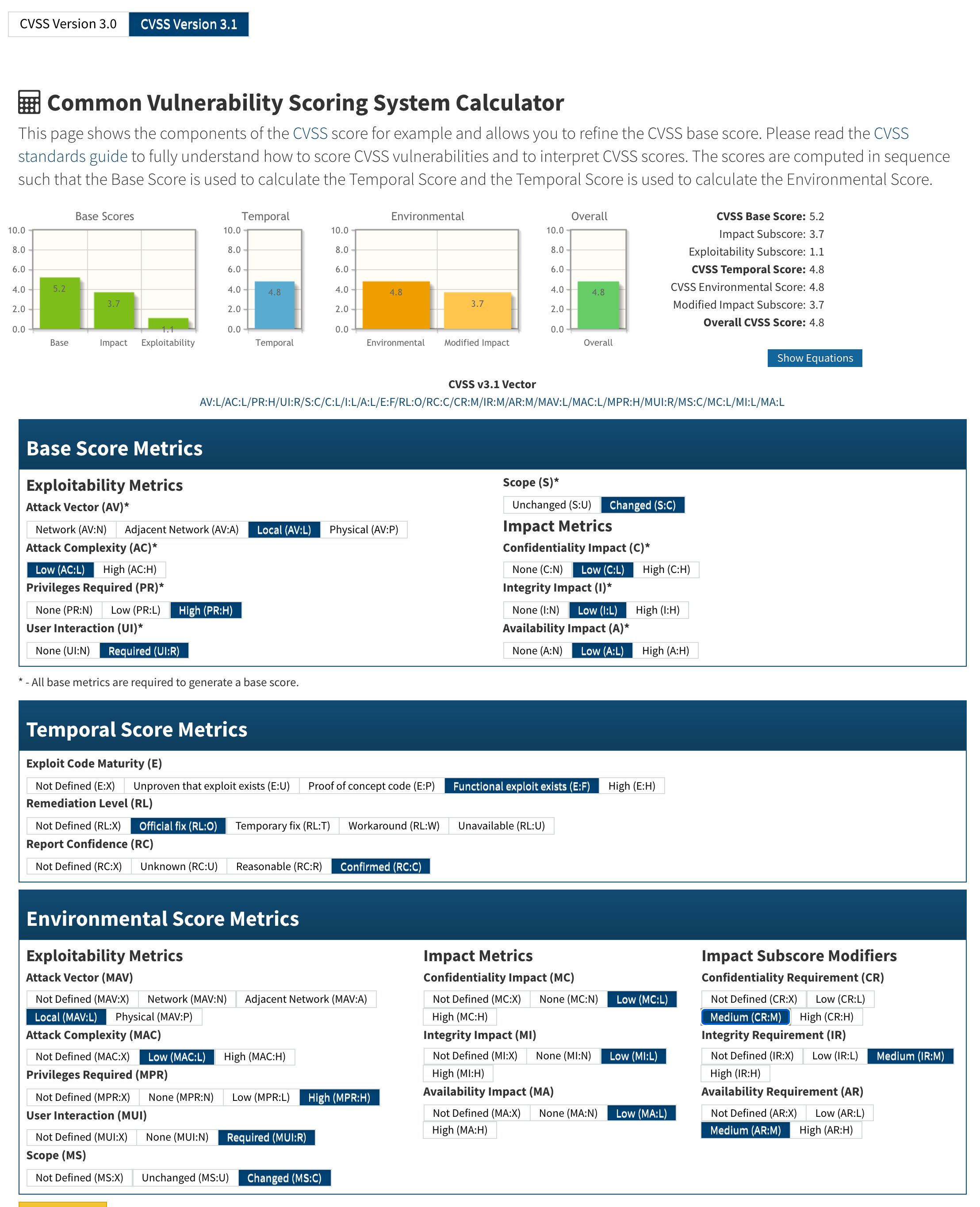
### References - https://github.com/octobercms/october/security/advisories/GHSA-94vp-rmqv-5875 - https://github.com/octobercms/october/commit/4c650bb775ab849e48202a4923bac93bd74f9982 - https://nvd.nist.gov/vuln/detail/CVE-2020-15247