LibreNMS vulnerable to SQL injection time-based leads to database extraction
Description
Published to the GitHub Advisory Database
Apr 22, 2024
Reviewed
Apr 22, 2024
Published by the National Vulnerability Database
Apr 22, 2024
Last updated
Apr 23, 2024
Summary
SQL injection vulnerability in POST /search/search=packages in LibreNMS 24.3.0 allows a user with global read privileges to execute SQL commands via the package parameter.
Details
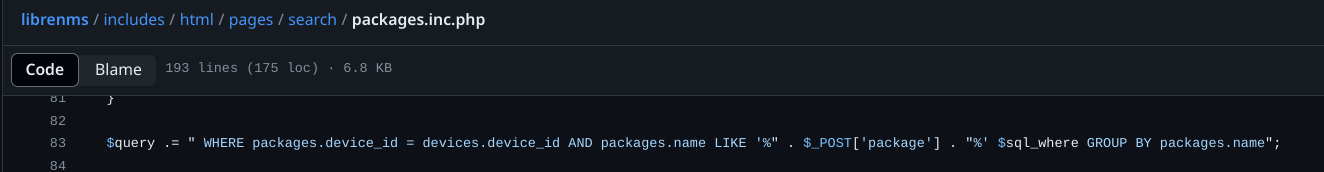
There is a lack of hygiene of data coming from the user in line 83 of the file librenms/includes/html/pages/search/packages.inc.php
PoC
https://doc.clickup.com/9013166444/p/h/8ckm0bc-53/16811991bb5fff6
Impact
With this vulnerability, we can exploit a SQL injection time based vulnerability to extract all data from the database, such as administrator credentials
References