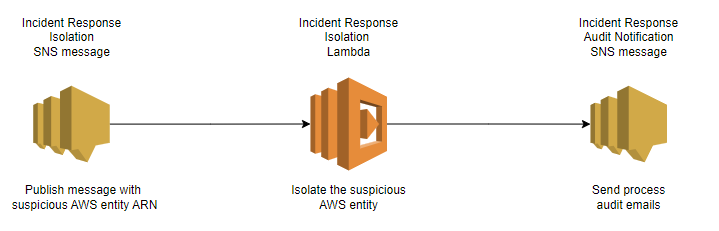
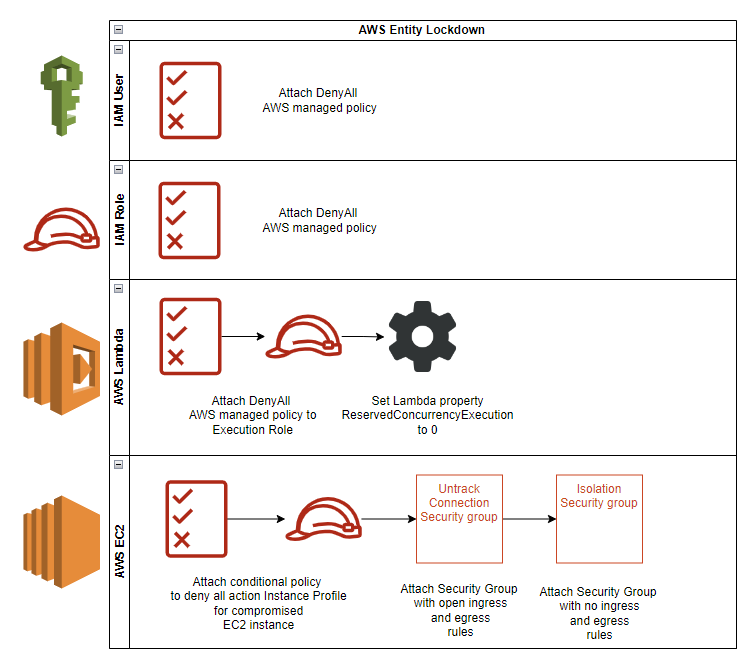
AWSEntityIncidentResponse is an automated entity lockdown solution for an AWS incident that allows security responders to do forensics, eradication, and recovery during an Incident.
This solution focuses on separating multiple targets so that each target only sees and affects itself—as a containment strategy. AWSEntityIncidentResponse automates lockdown of an Amazon EC2 instance, an IAM User, an IAM Role, and an AWS Lambda by using an AWS Lambda function that AWS SNS triggers. The solution supports cross-account and cross-region Incident Response.
Before you begin, ensure you have met the following requirements:
- You have an active AWS account.
- You have IAM permissions that meet requirements to deploy solution resources through AWS Cloudformation.
- You have AWS CLI configured (if you plan to test the solution locally)
To install AWSEntityIncidentResponse, follow these steps:
To get started, download the CloudFormation template from Amazon S3 . Alternatively, you can launch the CloudFormation template by selecting the following Launch Stack link.
Deploy the Incident Response solution AWS cross-account IAM Role (only if using multiple AWS accounts):
Download the CloudFormation template from Amazon S3. Alternatively, you can launch the CloudFormation template by selecting the following Launch Stack link
To use AWSEntityIncidentResponse, follow these steps:
export AWS_ACCESS_KEY_ID=AKIAIOSFODNN7EXAMPLE
export AWS_SECRET_ACCESS_KEY=wJalrXUtnFEMI/K7MDENG/bPxRfiCYEXAMPLEKEY
export AWS_DEFAULT_REGION=us-east-1
./publish_entity_for_incident_response.py \
--sns-topic-arn=arn:aws:sns:us-east-1:888888888888:entity-lockdown-sns-topic \
--entity_arn=arn:aws:ec2:us-east-1:888888888888:instance/i-0d205360XXXXX9a9XXX \
--external_id=123xyz*&^
./publish_entity_for_incident_response.py \
--sns-topic-arn=arn:aws:sns:us-east-1:888888888888:entity-lockdown-sns-topic \
--entity_arn=arn:aws:iam::888888888888:user/user1 \
--external_id=123xyz*&^
./publish_entity_for_incident_response.py \
--sns-topic-arn=arn:aws:sns:us-east-1:888888888888:entity-lockdown-sns-topic \
--entity_arn=arn:aws:iam::888888888888:role/service-role/role1 \
--external_id=123xyz*&^
./publish_entity_for_incident_response.py \
--sns-topic-arn=arn:aws:sns:us-east-1:888888888888:entity-lockdown-sns-topic \
--entity_arn=arn:aws:lambda:us-east-1:888888888888:function:function1 \
--external_id=123xyz*&^
To use AWSEntityIncidentResponse, follow these steps:
To get started follow the instructions in the Installing AWSEntityIncidentResponse section.
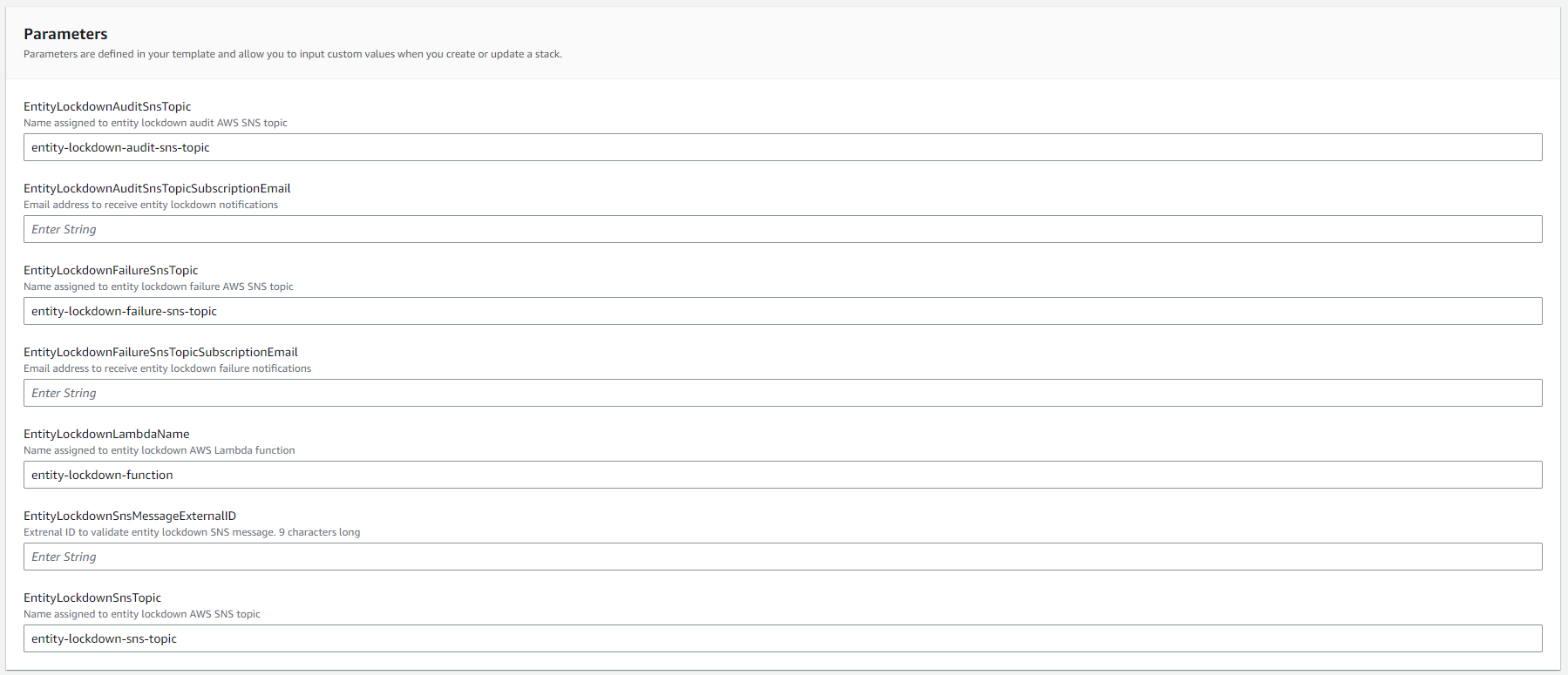
You can leave the default values for the stack as long as there aren’t any resources provisioned already with the same name. Otherwise, the naming convention is fully customizable from this screen, and you can modify the parameters as you see fit.
The SnsMessageExternalId Parameter does not have a default. This value is user-defined and static. Add this id to the SNS message attribute when publishing an SNS message with entity details.
The EntityLockdownAuditSnsTopicSubscriptionEmail and EntityLockdownFailureSnsTopicSubscriptionEmail Parameters also do not have a default. These email values will be used to send Incident Response notification emails. When deploying the AWS CloudFormationstack, email address inputs will receive one-time notifications from subscribing to the newly created SNS topics. If no action is taken on the requests, then Incident Response notification emails will not reach the recipients.
After you complete these steps, the following resources will be provisioned:
If you are using one AWS account, then this template is all you need. However, you will need to deploy two templates if you have a multi-account setup and want a cross-account Incident Response solution. Deploying the first template in your AWS security account will host Incident Response resources. The second template will create a cross-account IAM Role in the other accounts you like the solution to cover.
Set the EntityLockdownLambdaHostAccount Parameter with the AWS account that hosts the Incident Response resources deployed by the first CloudFormation template.
This stack will only create one resource. And AWS IAM Role that will give the Incident Response Lambda cross-account assume role permissions.
For walkthroughs and full documentation, please visit blog.