-
Notifications
You must be signed in to change notification settings - Fork 10.4k
ApiAuthorizationDbContext updates #21100
New issue
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and privacy statement. We’ll occasionally send you account related emails.
Already on GitHub? Sign in to your account
ApiAuthorizationDbContext updates #21100
Conversation
…ing a different key type.
…ent key type for User.
|
reopening to retrigger builds |
|
This looks reasonable to me, @ajcvickers does this match the current DbContext best practices? |
| /// </summary> | ||
| /// <param name="options">The <see cref="DbContextOptions"/>.</param> | ||
| /// <param name="operationalStoreOptions">The <see cref="IOptions{OperationalStoreOptions}"/>.</param> | ||
| public ApiAuthorizationDbContext( |
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
Note that this won't be usable with DbContext pooling. If IOptions<OperationalStoreOptions> needs to be resolved from the request scope for each context instance, then this is unavoidable. Nevertheless, people will complain.
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
This is a big drawback and can't happen.
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
I don't think I'm understanding this as I haven't yet used DbContext pooling. That being said, I guess I'm not seeing how this differs from the current implementation. Could you provide some clearer direction on what a possible solution could be?
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
@StevenRasmussen Why is there a need to add IOptions<OperationalStoreOptions> operationalStoreOptions as a dependency here?
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
This comes from IdentityServer and it has an impact on the DbSchema, so I'm not sure what can we do here.
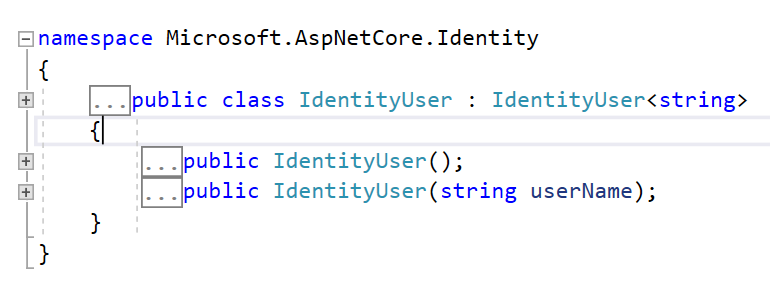
| /// Initializes a new instance of <see cref="IdentityDbContext"/>. | ||
| /// </summary> | ||
| /// <param name="options">The options to be used by a <see cref="DbContext"/>.</param> | ||
| public IdentityDbContext(DbContextOptions options) : base(options) { } |
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
This looks incorrect to me. A public constructor should use DbContextOptions<TContext>. If this class is intended to also be a base type, then it should get a protected constructor that takes DbContextOptions.
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
@ajcvickers - I just followed the pattern of all of the other existing contexts in the file. Let me know if you still think this should be changed.
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
@StevenRasmussen Any context that may be both used directly and inherited from should have both constructors. If there are other context classes that have this requirement but do not follow this pattern, then they should be changed as well.
|
@ajcvickers this PR is also trying to address the same issue I think #13064 we should probably pick one PR and close the other, which do you think is the one we should keep? |
|
When will this issue be fixed? |
|
@StevenRasmussen this looks promising, if you can address Arthur's feedback I think we would take this |
|
@ajcvickers - I think it might help if I provide a high level view of the problem this is solving along with what actually changed here: Problem: At the moment, What this PR changes:
I think we're getting stuck in the weeds here with perhaps other potential changes that may/may not be necessary (I don't know since I don't know enough about the inner workings of EF Core). That being said, if those changes are necessary, then I think they might better be addressed in a follow-up PR since it would be changing things in a more fundamental way. For example, if we were to change all the
Anyway, hopefully that helps clear things up. Let me know if you still want/need anything addressed in this PR. |
Just for clarity, ApiAuthorizationDbContext is a convenience class for the default scenario. We don't want to be living with a parallel class hierarchy to support all the options Identity does. The recommendation for more customized contexts is to extend IdentityDbContext directly and add the IdentityServer OperationalDbSchema on top. The code is literally this: |
|
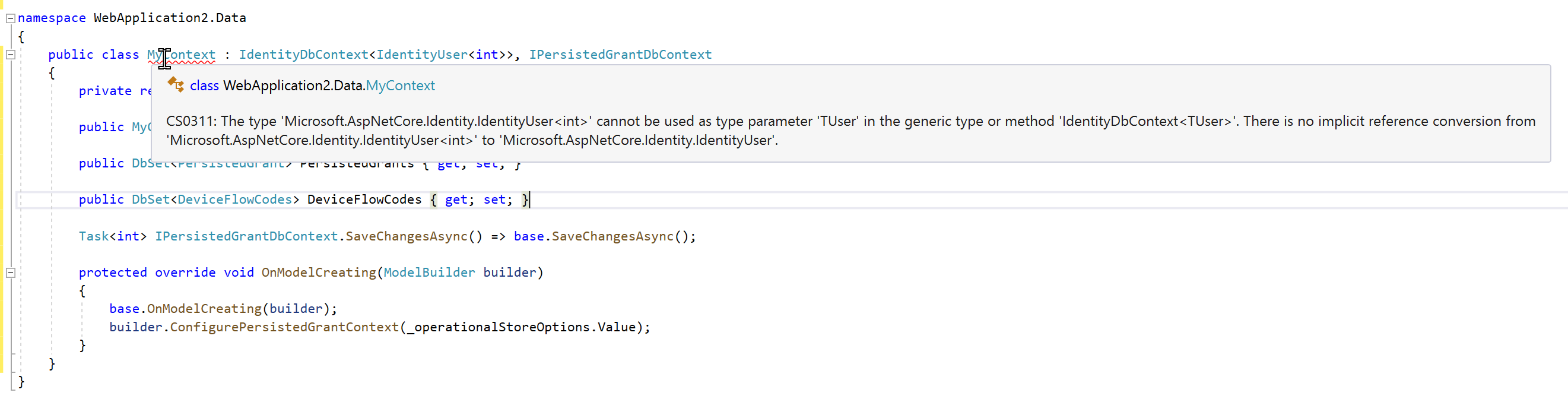
@javiercn - Thanks for the code... which actually demonstrates the current issue nicely ;). Right now we can't do that because This PR actually allows you to do as you are suggesting because it introduces a new public class IdentityDbContext<TUser, TKey> : IdentityDbContext<TUser, IdentityRole<TKey>, TKey> where TUser : IdentityUser<TKey>
where TKey : IEquatable<TKey>
{
/// <summary>
/// Initializes a new instance of <see cref="IdentityDbContext"/>.
/// </summary>
/// <param name="options">The options to be used by a <see cref="DbContext"/>.</param>
public IdentityDbContext(DbContextOptions options) : base(options) { }
/// <summary>
/// Initializes a new instance of the <see cref="IdentityDbContext" /> class.
/// </summary>
protected IdentityDbContext() { }
}FYI - Here is a screenshot of the error using your code above: |
Sure, I wasn't specifically talking about the IdentityDbContext changes, I'll let @HaoK and @ajcvickers speak for that. The only thing I want us to avoid is introducing a parallel class hierarchy for ApiAuthorizationDbContext since it will be expensive to test and maintain over time and the alternative to extend IdentityDbContext directly is much cheaper. |
|
If I'm hearing @javiercn correctly, it sounds like its mostly meant as a convenience class, and its not too much of a burden for them to plug in their own derived IdentityDbContext, so there isn't too much value in adding generics. Does that sound accurate? |
Yep, but any change to IdentityDbContext I'll let you be the judge of. |
|
@ajcvickers sounds like we are probably fine with things the way they are for 5.0 then here? |
|
Agreed |
|
Thanks for the PR @StevenRasmussen but I don't think we are looking to add generic support for this db context when its pretty straightforward to directly extend IdentityDbContext and use that instead |
|
@HaoK, @ajcvickers - To be clear: the changes to the That being said, I don't think the changes to the |
|
What do you mean? Can't an app just add |
|
Doh! Ok... you're correct. It's been several months since I've been working in this area. That being said... I'm trying to remember the issue that I ran into that sparked this whole thing and I think it has to do with using all of the default IdentityServer plumbing when registering everything in your web project. Let me try to work this out again and I'll post my results here. Thanks for your patience. |
|
Coming to this late, but I'm trying to convert my app from Blazor Server using a customised User class that uses an I've seen the answer on this SO post which implies that I can build my own derived |
|
Hi @Webreaper. It looks like you just commented on a closed PR. The team will most probably miss it. If you'd like to bring something important up to their attention, consider filing a new issue and add enough details to build context. |
Summary of the changes (Less than 80 chars)
ApiAuthorizationDbContextto follow best practices per @ajcvickers commentIdentityUser<T>Addresses #9548