-
Notifications
You must be signed in to change notification settings - Fork 185
Description
Hello,
We are using python-iptables v0.12.0 in production within a dockerized environment orchestrated by kubernetes.
The container application that uses python-iptables library consists of the following networking:
-
Two interfaces, let's name them eth0 and eth1, to which are assigned one ipv4 and one ipv6 address for each one and are used only for internal communication purposes among the containers running in the kubernetes cluster.
-
One interface, let's name it ext0, to which two ipv6 addresses are assigned and is used only for external communication purposes i.e. between the kubernetes cluster and the outside world.
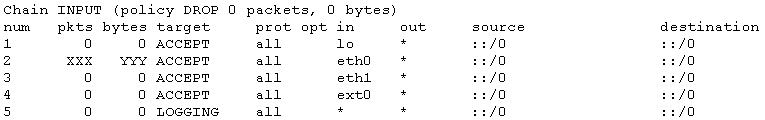
At startup, our application has the following ip6tables configuration created totally by python-iptables library. We will focus only on INPUT chain as it suffices in order to describe our issue. Note that LOGGING target is used only to log dropped packets:
Our intention, essentially, is to drop all incoming ipv6 traffic that is coming from the outside world through ext0 interface. (Of course, take into account that there is a lot of traffic coming through ext0 interface).
However, as you may notice above, not only no packet is actually dropped but at the same time all packets match the second rule which corresponds to one of our internal interfaces.
Things get more interesting when we try on the fly to modify our INPUT chain of our ip6tables list.
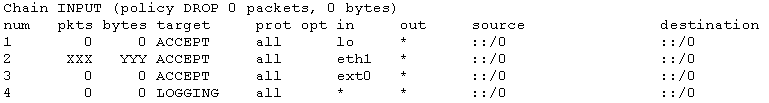
In our first modification, we proceed to accept all traffic for our ext0 interface and thus ip6tables becomes as it follows:
Still all traffic goes through eth0 interface instead of ext0.
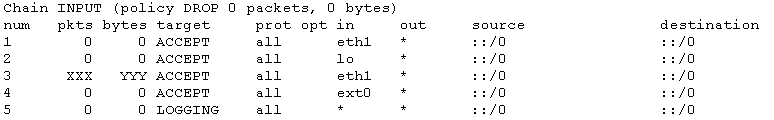
In the next modification, we delete the second rule of INPUT chain hoping that traffic is going to match our external interface,
Still the same issue persists but now all traffic matches eth1 interface!
Until now it seems that the issue could originate from our networking configuration, but the next modification cancels this potential root cause.
We now add the same exactly rule so as to accept traffic using eth1 interface, but now instead of using python-iptables we use Linux iptables package:
For some unknown reason the same rule generated by Linux iptables package works as expected (not matching packets destined for ext0 iface), whereas the rule generated by python-iptables misbehaves.
From the above scenario, it seems that there is potentially some difference on how ipv6 rules are generated between python-iptables and Linux iptables packages.
It's kind of a complicated issue, but I hope I made myself as clear as possible :)
Could you please provide some guidance on how to troubleshoot/approach this issue?
Thank you in advance for your suppport.
BR,
Giannis