-
Notifications
You must be signed in to change notification settings - Fork 30.6k
New issue
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and privacy statement. We’ll occasionally send you account related emails.
Already on GitHub? Sign in to your account
General Discussion on Workspace Trust Feature #106488
Comments
(closes #15525) This change enables the new "Trusted Workspaces" feature of VS Code (see microsoft/vscode#106488) for the extension. For now a user must put `"workspace.trustEnabled": true` in their settings.json to trigger the functionality (and it only works on VS Code insiders).
|
Thanks for working on this feature. This will help extensions address the security issues around untrusted repositories in a more consistent and reliable way. A couple of questions:
|
|
@hwsamuel, disable |
|
It is definately showing me this prompt every time vs code starts and I open a given workspace if I elect not to trust the workspace in question the previous time. ...and in one case it showed it to me multiple times within the same workspace during the same vs code executation instance when I was navigating around subdirectories within the project. Ultimately I do trust the workspace in question, but imo I don't think I should have to - to my knowledge I don't have anything that should be executing arbitrary files inside the project when I launch vs code? And if I do, I wish for that to never happen. This behaviour, automatically executing arbitrary code within the workspace directory on editor start, should be opt-in not opt-out if I disable the prompt, right? edit: Just now I tried setting |
|
Also.. just wanted to share my 'lol' at the setting item 'Trust: Empty Window - Controls whether or not the empty window is trusted by default within VS Code' what even is this? |
This should not be the case. |
^ that doesn't work. For example, I open the file via Filezilla, and I still get the pop-up. I expect execution to be disabled without any prompt. |
|
@sybrew, the |
|
Hello, While the motivation for this is very well explained above, and it can certainly protect less experienced users, I suggest that one of these two options be considered:
From a user's point of view, there's nothing worse than your trusted software behaving differently than before, with no explanation, especially when it just keeps bugging you (Y'see, I tend to trust my own workspaces 😊). |
|
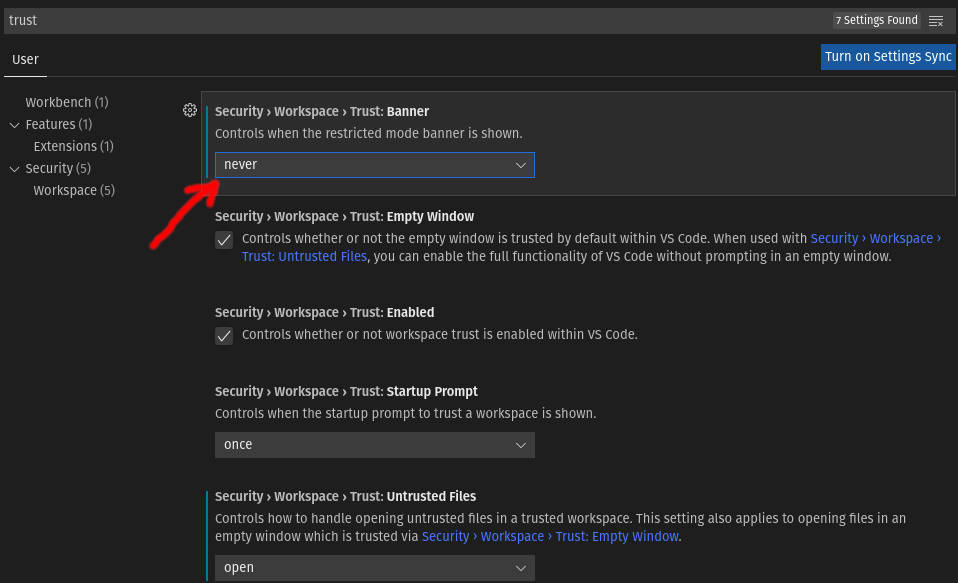
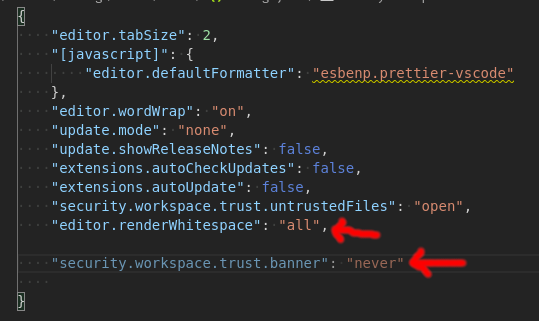
with the following in my project's "security.workspace.trust.startupPrompt": "never",
"security.workspace.trust.enabled": false,...i'm still seeing a prompt with "Do you trust the authors of the files in this folder". this is preventing my end-to-end tests from running to completion. is there a way to entirely disable this feature in this context? edit: ah, i see there'a flag i can pass in apologies for the noise 🙏 |
|
One use case that I have as a prof is to download and grade student submissions. I do this thousands of times per semester, and I really wish I had a checkbox to Not trust a parent folder once vs. only being able to blanket Trust the parent: For me, I'd be find to not trust Could that checkbox be altered to affect the parent for either the Yes or No case? |
|
There needs to be a way to trust "just once" for the current open editor. I don't want to have to maintain a list of trusted folders. |
|
This is a very noisy feature. Throwing up a modal every time a new folder is opened is annoying. Please use a sane default. One idea is to open everything untrusted and then have the user trust a folder if they want the addition features. |
|
This feature is a piece of SxxT, could vscode just to be a quite, swift and silenced TEXT EDITOR or IDE only? This feature will prevent non-programmers to use vscode, they will ask for notepad++ or something else instead, even a computer HAS installed a vscode, because they do not understand what they should do to this dialog. Trust or untrust, why should I care? As an IDE, no such kind of IDE such as visual studio or jetbrains has such fXXking idiot feature to annoying users, but they definitely do more than a vscode do, is that it? Just do what vscode should do, leave other things to expertise softwares (such as anti-virus softwares), please! |
Many features get disabled with this, for example language support. If we did this without prompting, many users would not discover language support for Python for example and assume it's broken.
@Coresi7 the reason this feature exists it because we received several security vulnerability reports, both for core and for extensions. And what was starting to happen was core and extensions were all implementing their own system to cover this. This feature consolidates it so there is a single prompt and that's it. If it's annoying you can essentially disable it by checking this box: For finer grained control, run the manage workspace trust command and add your I agree it's unfortunate that we need this at all, but we (vscode core and 1st party extensions) have a hard requirement to not cause a potential remote code execution vulnerability upon the opening of a folder. It's pretty obvious why we need to do this. @sbatten @lszomoru is there anything else to do on this issue? Are we for example considering a checkbox to just trust everything to help the class of users that don't care, or is that too heavy handed? |
|
Yes, maybe devs and IT techs could understand this (but not all of devs or it guys), but users do not. They will complain vscode is hard to use, because they do not understand why. They even do not know how to install a plugin, or use settings, they care how fast it can be or how to make the fonts or words rendered correct and meaningful without install heavy text editor tool (such as an IDE, or office like document editor). For this part of users, they do never care about trust or not. |
|
@Coresi7 that's why we link off to extensive docs. It's a complicated problem that needs to balance usability and discoverability and this is what we came up with after months of discussion. One of the main reasons it's not as you're suggesting is because VS Code isn't really that useful without workspace trust since so many things are turned off, so we ask immediately upon folder open. It actually is already kind of is as you ask actually as several features request workspace trust immediately upon folder open (tasks, git, terminal, python language smarts). Again it's unfortunate it needs to exist, but it's there to protect users. |
|
There are likely other feature requests that I did not account for, but reading through the recent discussion and cross-referencing with out feature requests, I am closing this item in favor of the individual issues per problem. |
|
@Tyriar what did you mean by this?
Is there a command like |
|
@TamaMcGlinn open the command palette (f1 or cmd/ctrl+shift+p) and select manage workspace trust: You can then add whatever directory you want to permanently trust to the list in the bottom. For example I trust |






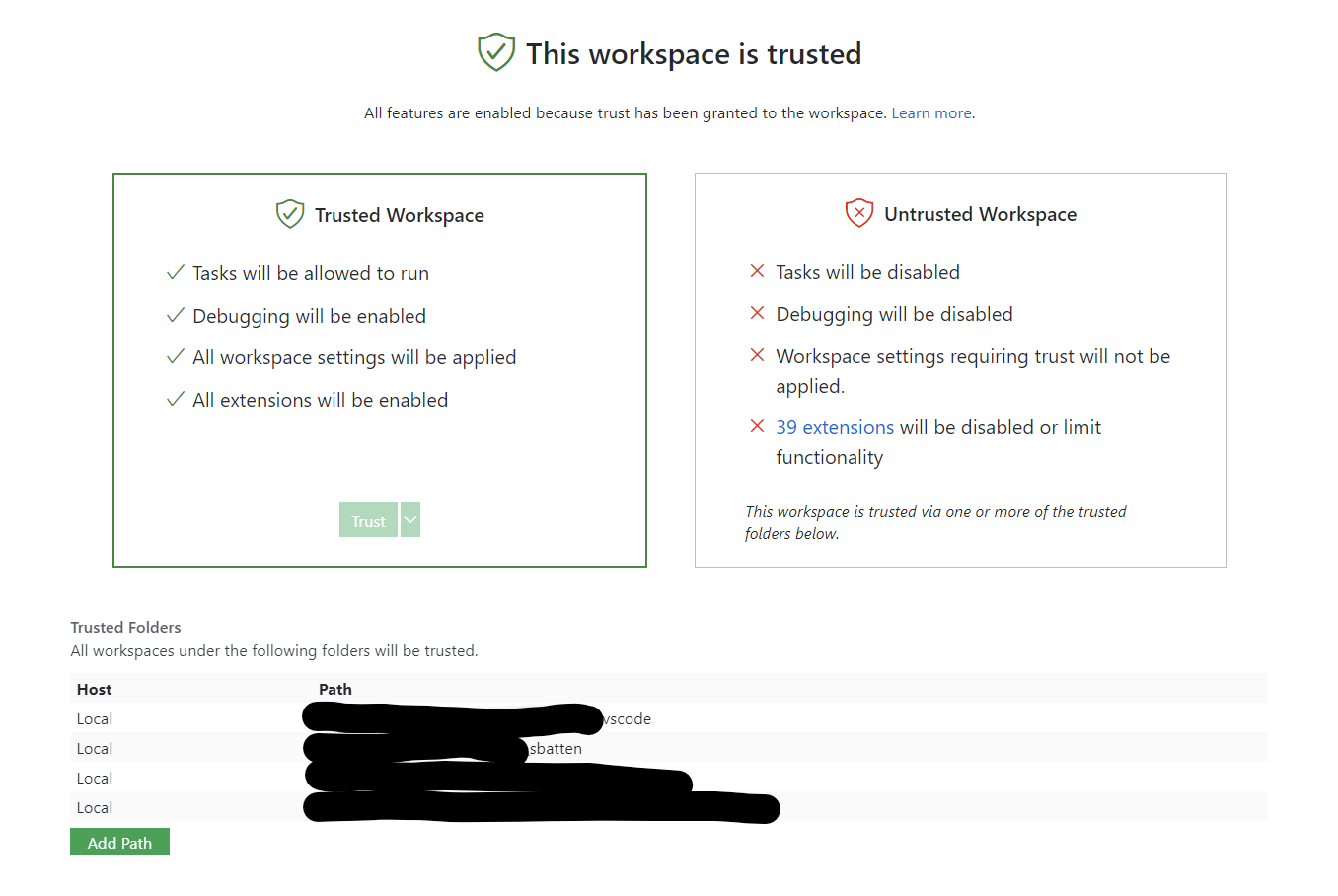
Trusted Workspace
The trusted workspaces concept is intended to centralize and unify a security conscious decision required by a variety of VS Code features. The easiest existing example to understand of this decision is with the ESLint extension. The ESLint extension will try to use the eslint module in the current folder that is opened in VS Code and execute code from it. Since you may have checked out a random repository from the web, this could be dangerous if the repository contains a corrupt eslint module. Notice that ESLint is not trying to be malicious, but rather, the repository/corrupt module is taking advantage of this automatic code execution.
With Trusted Workspaces, the user will be able to declare whether or not they trust the folder that is opened in VS Code before these features are executed.
Current Subscribers
Extensions
Extensions should use this guide to participate in workspace trust.
Tasks
Tasks will not execute in an untrusted workspace.
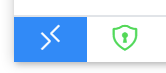
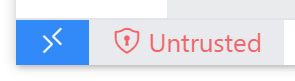
Status Bar Indication
A trusted state is indicated with a small green icon. An untrusted state is indicated with the icon and text.
Management
The following json editor is a stand-in for a more feature-rich editor. We intend to replace this soon.
Try it out
Enable the setting
Add
"security.workspace.trust.enabled": trueto yoursettings.json.The text was updated successfully, but these errors were encountered: