Automation through Patch Manager & Maintenance Window services allows us to manage operating system updates and upgrades for Windows and Linux computers implemented in AWS, on-premises environments or other cloud providers. We can quickly review the status of available updates on all agent computers and manage the process for installing required updates for servers.
- Create a Default Patch Baseline1
- Add Instances to a Patch Group
- Create a Maintenance Window for Patching
- IAM Managed Roles:
AmazonEC2RoleforSSM- All EC2 instances need to this permission to be attached.AmazonSSMMaintenanceWindowRole- Not down the ARN, We will need this ARN to configure maintenance window.
- Make sure all EC2 instances to be patched have AWS SSM Agent Installed and communicating with SSM
- Requires outbound
443to internet SG Rule
- Requires outbound
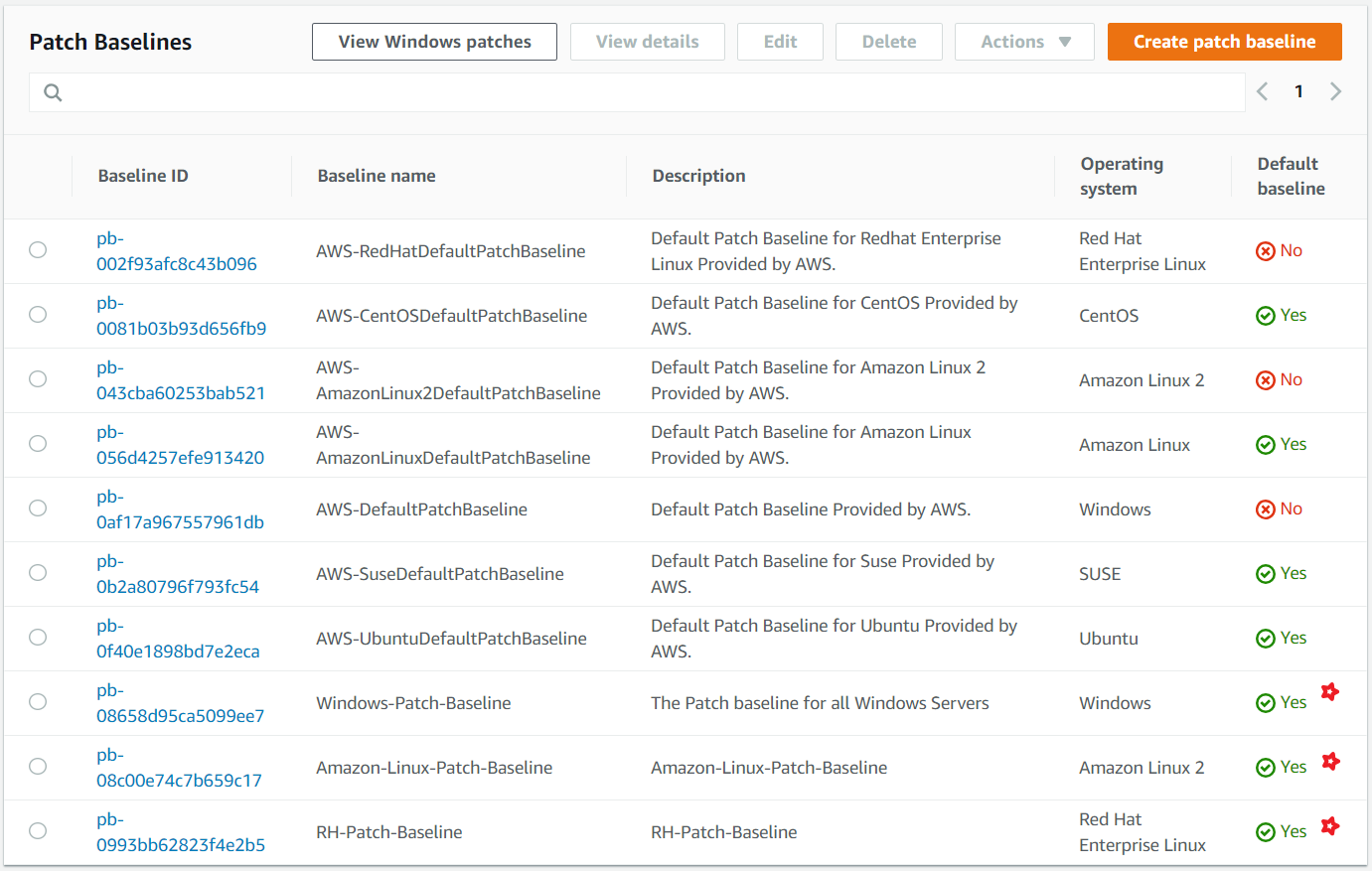
AWS provides default baselines for all major OS's as recommend by the ISVs, If needed we can customize these patch baselines for inclusion or exclusion of any specific patches. The default configuration is good place to start with in most use cases. The same can be duplicated and used for your clients, and made the default baseline to allow for future customizations.
To allow fine control over the patching of virtual machines running different OS's(example Windows 2016, Windows 2012, RHEL7.x, Amazon Linux etc) and different business functions like (Webservers running IIS or Apache or nginx etc) each of them need to have a special tag key Patch Group DO NOT CUSTOMIZE TAG; USE AS-IS
| Tag Key | Tag Value | Effect | Schedule |
|---|---|---|---|
| Patch Group | Windows | ALL windows flavors will fall into this category | |
| Patch Group | RHEL | ALL Redhat flavors will fall into this category | |
| Patch Group | Windows2012 | ALL Windows 2012 servers will fall into this category ALL Security patches will be installed | |
| Patch Group | Management Server | ALL Shared Service Servers | cron(00 23-5 ? * TUE#1 *) |
| Patch Group | Web Server | ALL Web Servers | cron(00 23-5 ? * THU#1 *) |
| Patch Group | Application Server | ALL Application Servers | cron(00 23-5 ? * THU#2 *) |
| Patch Group | Database Server | ALL Database Servers | cron(00 23-5 ? * THU#3 *) |
*The advantage of Thursday patching is that people are available on Friday in case something should not have gone well. Customize as required.
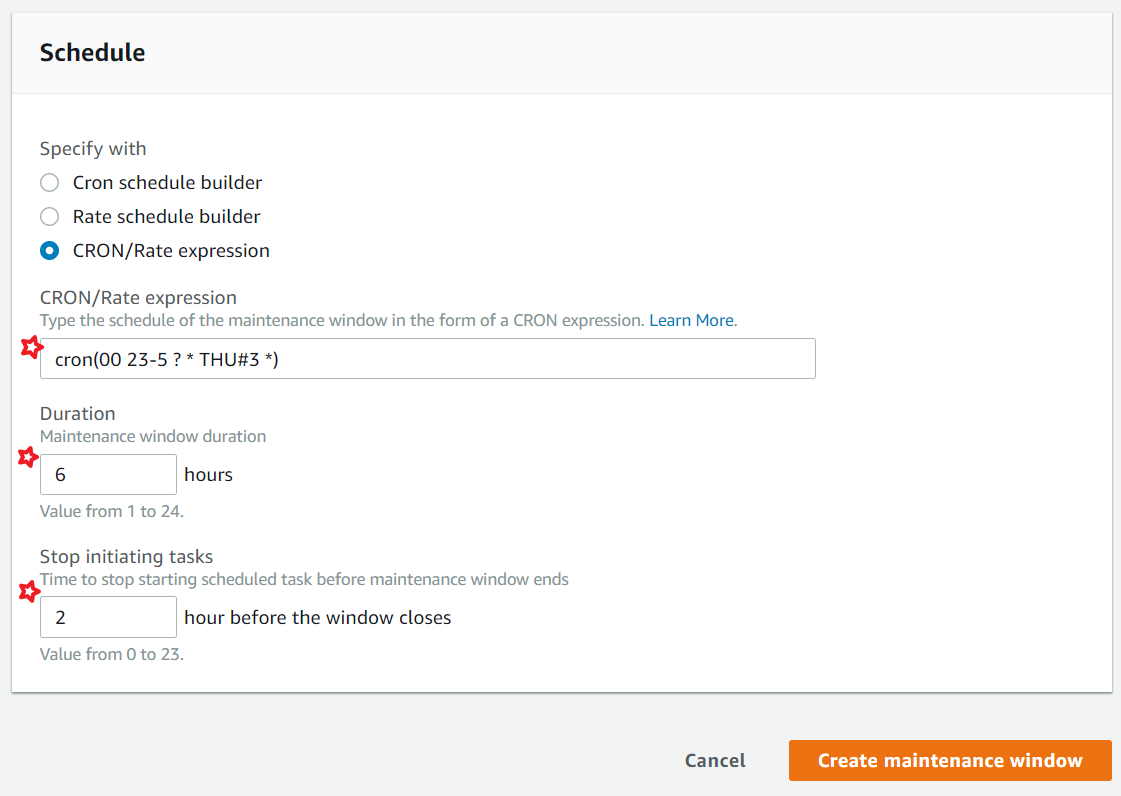
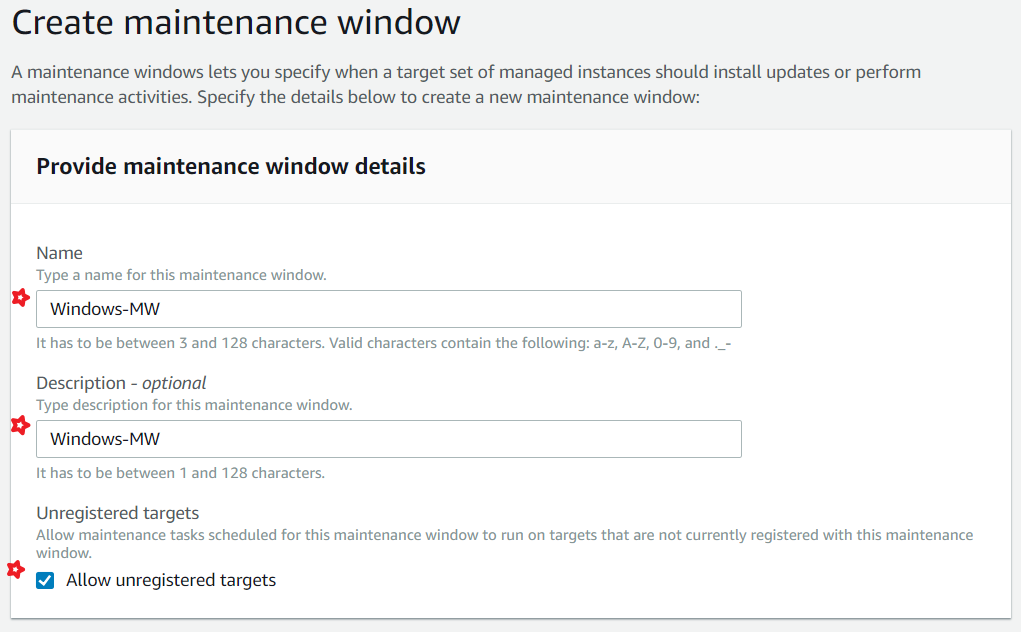
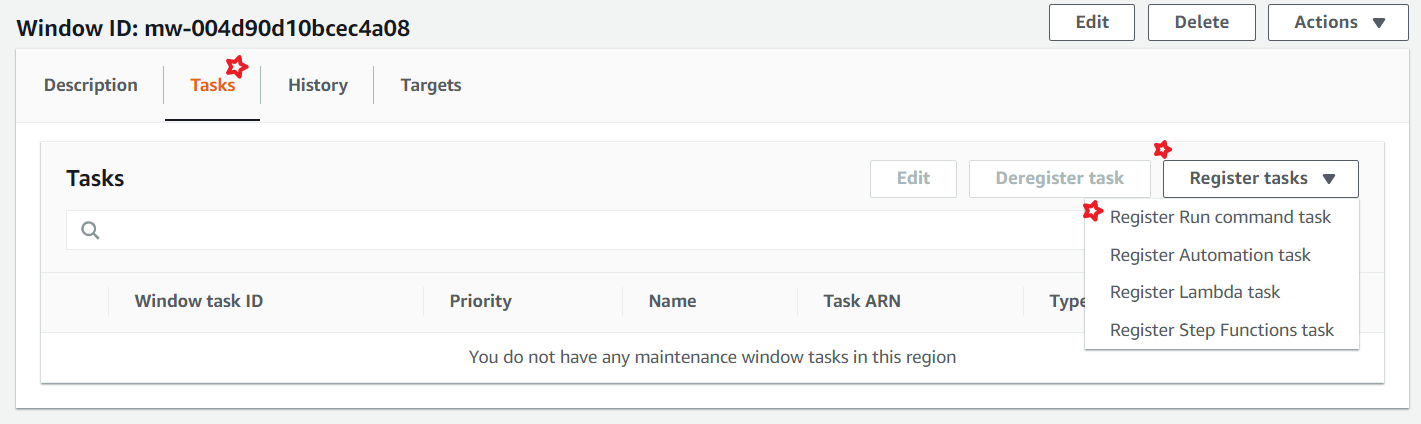
To minimize the impact on service availability, It is recommend that we configure a Maintenance Window to execute patching during times that won't interrupt business operations. AWS Systems Manager Maintenance Windows let you define a schedule for when to perform potentially disruptive actions on your instances such as patching an operating system, updating drivers, or installing software or patches. Each Maintenance Window has a schedule, a duration, a set of registered targets.
< 2 images>
Choose the maintenance windows that suits your environment needs. You can choose a cron expression. Customize as required.
| Environment | Patching On | Time |
|---|---|---|
| Sandbox | Weekdays | 10PM-3AM |
| Development | Weekdays | 10PM-3AM |
| Test | Weekdays | 10PM-3AM |
| Acceptance | Weekend | 6AM - 11AM |
| Production | Weekend | 6AM - 11AM |
Important: After installing patches, Systems Manager reboots each instance. The reboot is required to make sure that patches are installed correctly and to ensure that the system did not leave the instance in a potentially bad state.
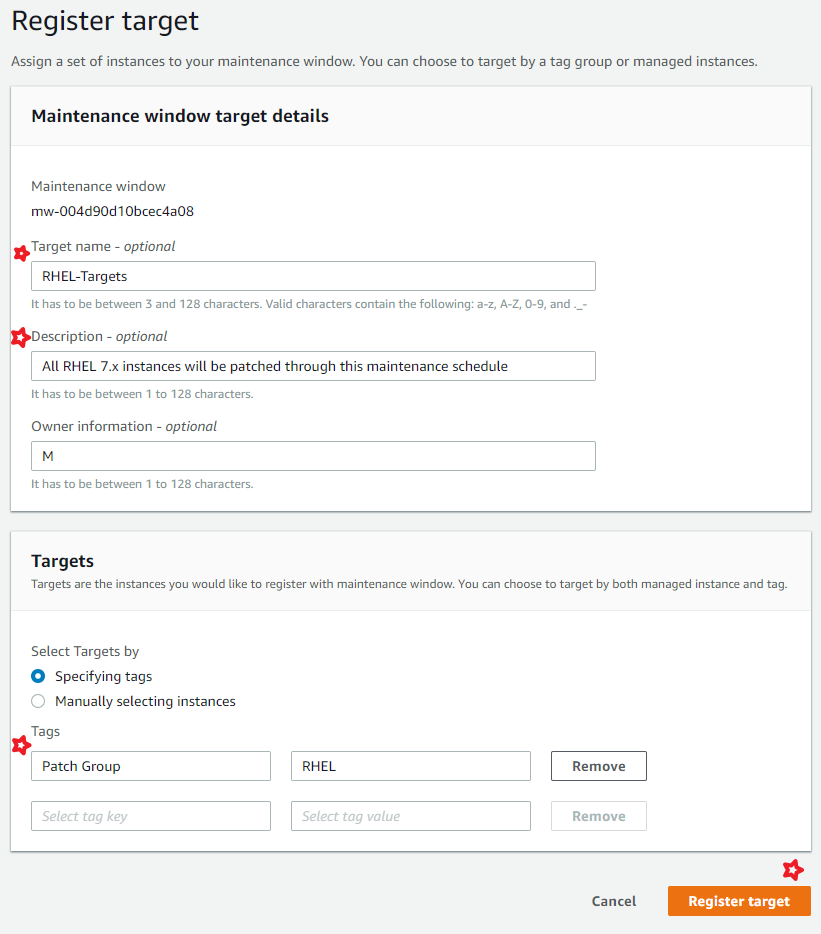
The easiest way to attach targets is to use the tag key Patch Group and have multiple values suiting your needs.
Create Patch Group for your environment, For example,
Win- For patching all windows ServersLinux- For all servers running Linux OSesWeb Servers- For pathing all Web Servers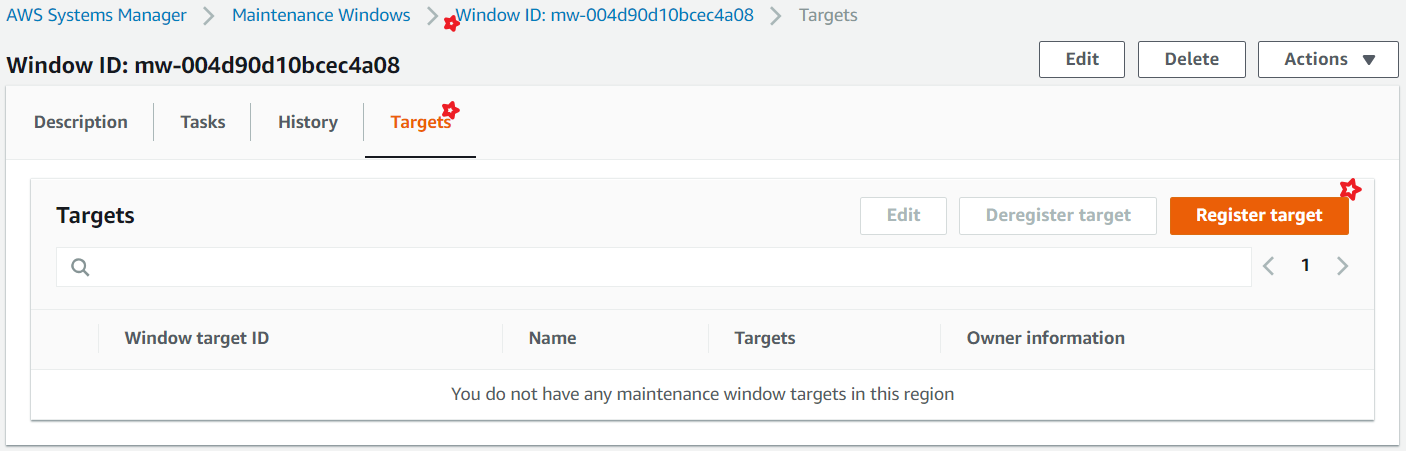
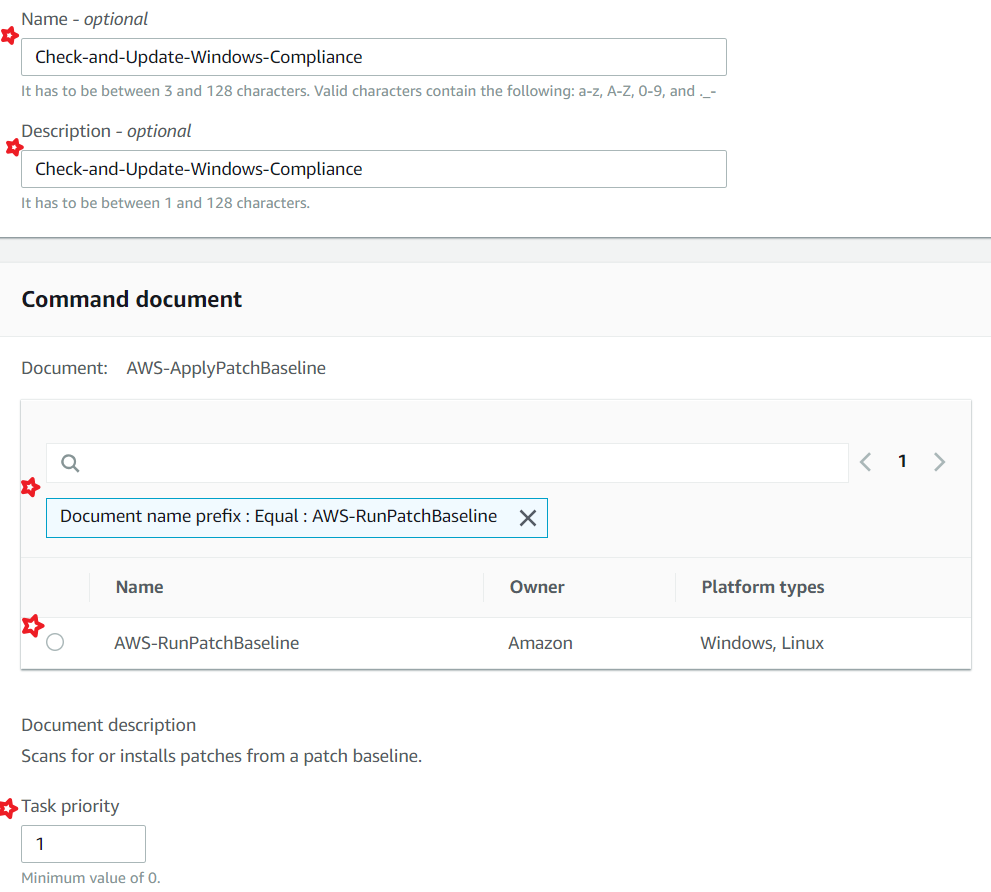
AWS-RunPatchBaseline - This is the latest version of document recommended by Amazon to install/scan patches.
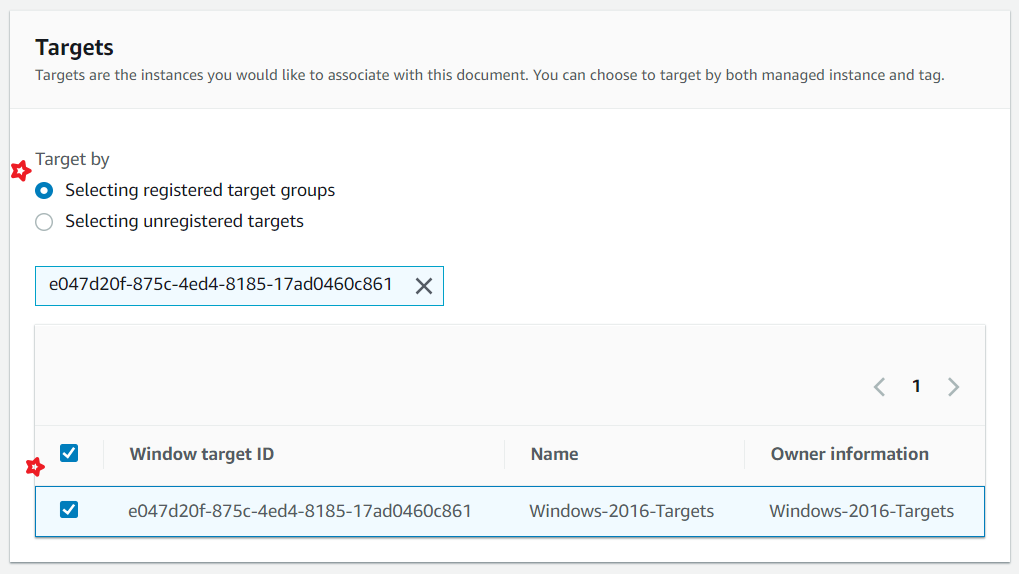
You can control how many instances are patched at any given time and how to handle errors using Rate Control
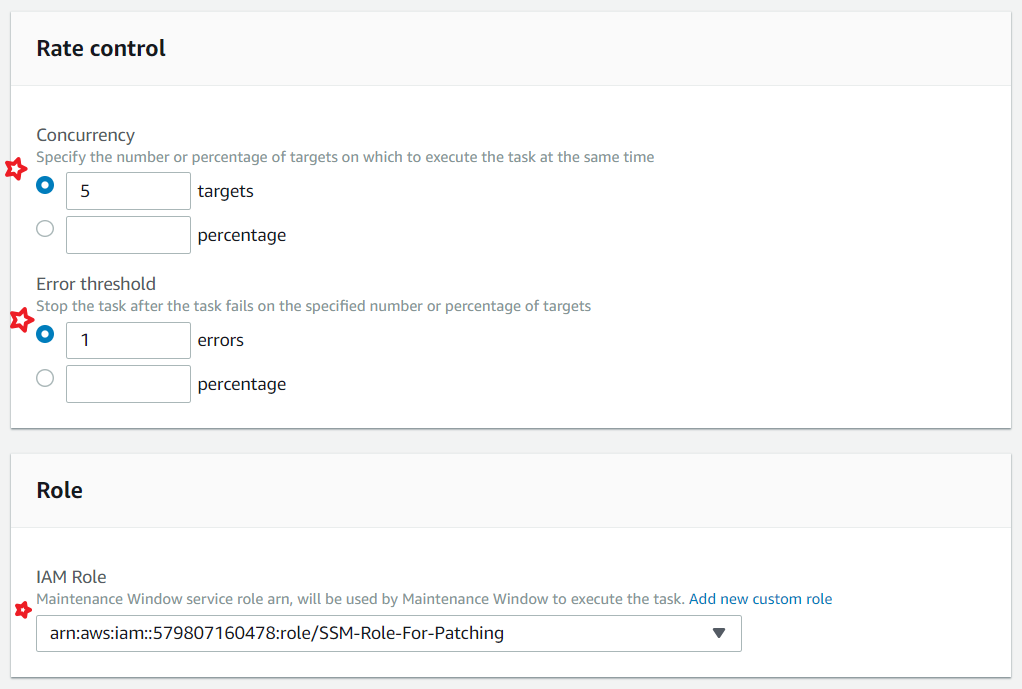 Update the Role ARN, that was created in the Pre-Requisites.
Update the Role ARN, that was created in the Pre-Requisites.
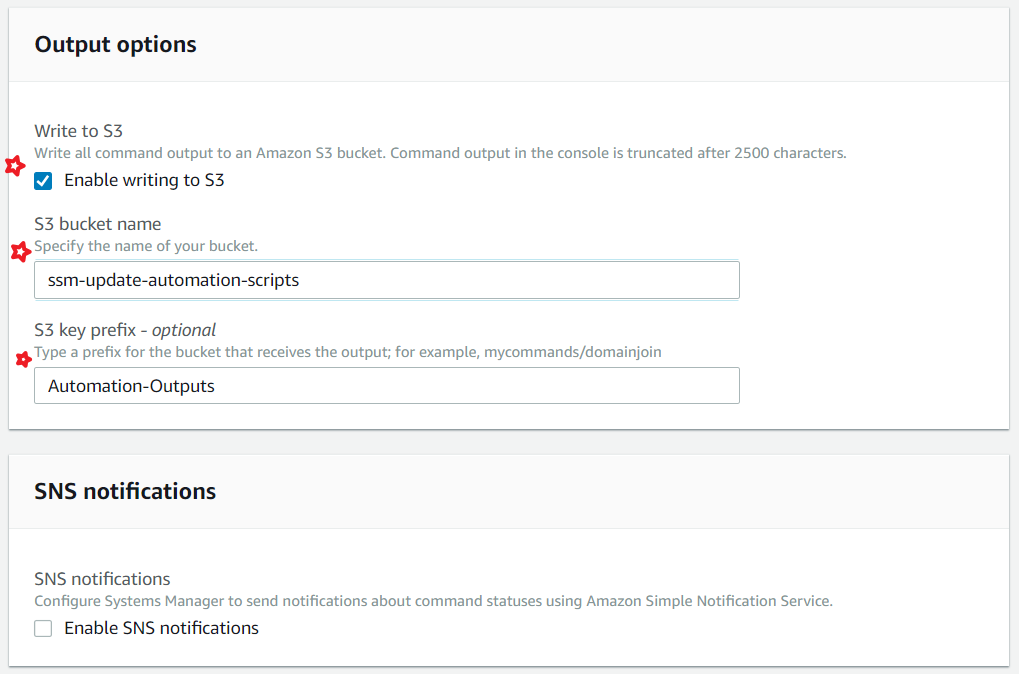
In case you want to analyze the patch update logs, you can save them to S3
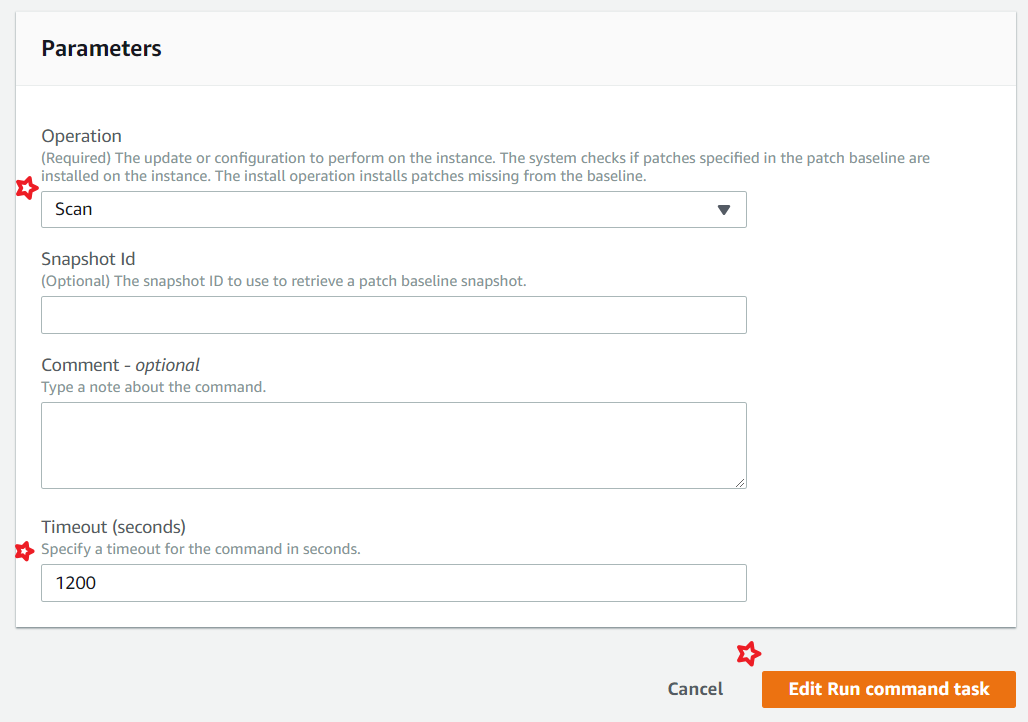
If you want to only Scan your instances for missing patches then use the Scan option, If you want the patches to be installed, use the Install Option. _The below screenshot shows only scan.
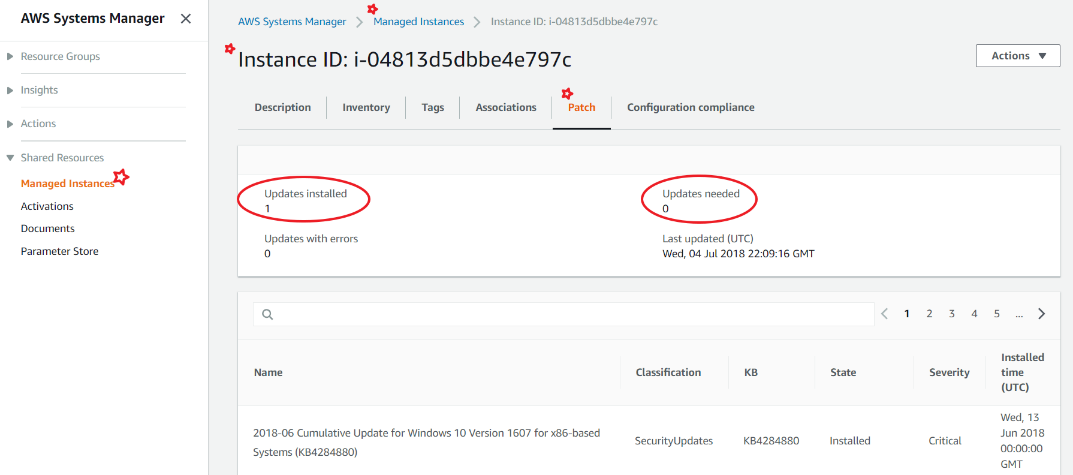
Now that all the steps are completed. The automation will kick in as per the schedule chosen.
Under managed instances of SSM, we can find all the missing and installed patches. Under compliance section the overall view can be seen.
| Example | Details |
|---|---|
| cron(00 23-5 ? * THU#3 *) | Run third Thursday of every month between 23:00 and 05:00 UTC time |
| cron(0 2 ? * THU#3 *) | 02:00 AM the third Thursday of every month |
| cron(15 10 ? * * *) | 10:15 AM every day |
| cron(15 10 ? * MON-FRI *) | 10:15 AM every Monday, Tuesday, Wednesday, Thursday and Friday |
| cron(0 2 L * ? *) | 02:00 AM on the last day of every month |
| cron(15 10 ? * 6L *) | 10:15 AM on the last Friday of every month |