-
Notifications
You must be signed in to change notification settings - Fork 333
Threat actor group mapping
Marcus Bakker edited this page Dec 20, 2021
·
10 revisions
The group functionality of DeTT&CT allows you to:
- Get an overall heat map based on all threat actor group data present in ATT&CK. Please note that like all data there is bias. As very well explained by MITRE: Building an ATT&CK Sightings Ecosystem.
- Create heat maps based on a subset of groups present in the ATT&CK data of MITRE.
- Create your heat maps based on the intelligence you get from your intelligence team or on techniques performed in red team exercises.
- Compare techniques used by threat actors with your level of visibility or detection to uncover possible gaps and improvements.
- Compare threat actor groups.
- Visualise the potential capabilities of a threat actor based on the software they use (
--software-group)
You can record the following information on threat actors in YAML group administration files:
- The name of the threat actor.
- A possible threat actor campaign name.
- Techniques used by this threat actor.
- Software used by this threat actor (also see the option:
--software-group) - A flag to indicate if the group must be enabled when DeTT&CT loads the YAML file.
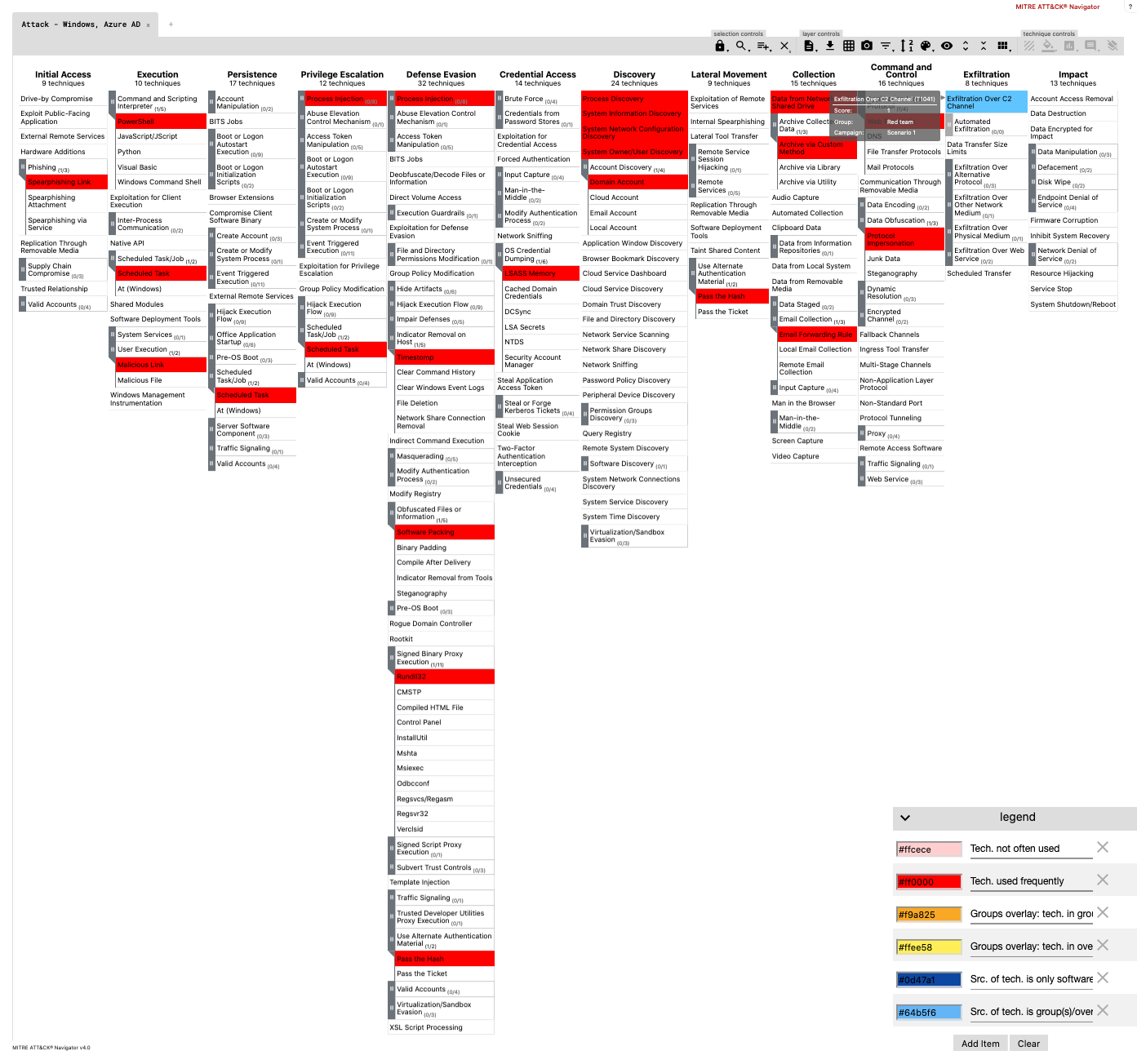
The generated layer file below contains a heat map based on all threat actor data within ATT&CK. The darker the colour in the heat map, the more often the technique is being used among groups.
python dettect.py g

The generated layer file below contains a mapping based on threat actor data stored in a group YAML file.
python dettect.py g -g sample-data/groups.yaml
- Home
- Introduction
- Installation and requirements
- Getting started / How to
- Changelog
- Future developments
- ICS - Inconsistencies
- Introduction
- DeTT&CT data sources
- Data sources per platform
- Data quality
- Scoring data quality
- Improvement graph