A Browser Extension for Quick URL Fuzzing and Secret Scanning
Fast, lightweight, and designed for security engineers who want immediate reconnaissance without leaving the browser. Quickly identify hidden endpoints and potential secrets across all open tabs.
- Quickly fuzz URLs in all open tabs to discover hidden endpoints.
- Use custom wordlists or built-in example lists.
- Concurrent requests with configurable batch size.
- Scan JavaScript files loaded in each tab for likely secrets (API keys, tokens, AWS keys, etc.).
- Export findings for further analysis or reporting.
- Lightweight UI for quick runs and detailed results with request/response snapshots.
- Open source and free to use.
- Download the latest release from the Releases page and unzip the archive.
- Open Chrome (or another Chromium-based browser) and navigate to
chrome://extensions/. - Enable Developer mode using the toggle in the top-right corner.
- Click Load unpacked and select the extracted extension folder.
- The FlashFuzz icon should appear in your browser toolbar — pin it if you want quick access.
- Click the icon to open the extension and start fuzzing!
- Download the latest release from the Releases page and unzip the archive.
- Open Firefox and navigate to
about:debugging#/runtime/this-firefox. - Click Load Temporary Add-on… and select the downloaded zip file.
- Click the FlashFuzz toolbar icon to open and start fuzzing.
- FlashFuzz must be enabled (Check the toggle in the top right corner of the extension).
- Open the tabs you want to scan (one or many).
- The extension will automatically run fuzzing and secret scanning on all open tabs.
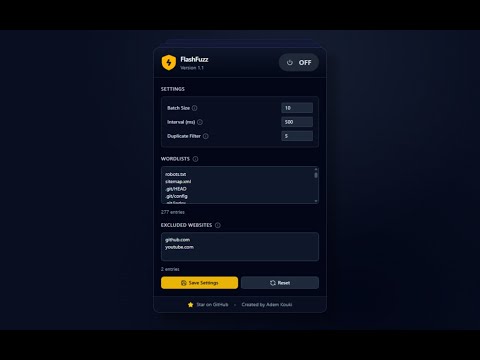
You can adjust settings like wordlist, batch size, and secret scanning options in the settings tab.
- Wordlist: You can use the default wordlist or provide your own custom list.
- Batch Size: Adjust the number of concurrent requests sent during fuzzing. (Default: 10 requests)
- Interval between requests: Set a delay between each batch of requests to avoid overwhelming the target server (Default: 500ms).
- Duplicate Response Filter: Enable this to filter out duplicate responses based on content length. This helps reduce noise in the results. (Default: 5 requests)
Q: Is FlashFuzz free to use? A: Yes, FlashFuzz is completely free and open source.
Q: Can I use my own wordlist? A: Yes, you can provide your own custom wordlist in the settings.
Q: Does FlashFuzz store my data? A: No, all processing is done locally in your browser. No data is sent to any external servers.
FlashFuzz is a tool for security testing and reconnaissance. It can generate a significant number of requests to target hosts. You must obtain explicit authorization before using FlashFuzz against any system you do not own or have permission to test. Unauthorized scanning or fuzzing may be illegal and may be considered malicious activity.
I am not responsible for any damage, disruptions, legal issues, or other consequences that arise from your use of this software. By using FlashFuzz you accept full responsibility for how you use it.
Always follow ethical guidelines and local laws. For professional engagements, use FlashFuzz only under an agreed scope and written permission.
Contributions are welcome! Please fork the repository and submit a pull request with your changes.
This project is licensed under the MIT License. See the LICENSE file for details.