-
Notifications
You must be signed in to change notification settings - Fork 983
Argon2 + encryption changes #395
New issue
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and privacy statement. We’ll occasionally send you account related emails.
Already on GitHub? Sign in to your account
Conversation
- Optimize adding & deleting (using state instead of reloading and checking the hash again) - Use 16 KiB memory + Argon2di
11 entries takes about 500ms with 16KiB, 8 KiB takes about 300ms
empty backup with no password fix
up the hasing memory to 16
Chrome does not allow webassembly without adding 'unsafe-eval' to CSP.
- change password
|
@Sneezry this has been sitting for a while, do you plan to review this? |
|
It's a little long story, and I think we may go back one step. Why we use secret hash?When I first design data structure of secret, I use secret hash as key of the dictionary. Because Chrome supports to update part of data by specific key if the data is a dictionary map. So I think if we should always update the entire data (#412), secrest hash is not required. And if so, Argon2 may be not required either? Event page vs background pageBrowser extension should be as lite as possible, and take seriously with background page. I still concern if it is worth to use a background page on user side. I understand we should always pay attention to security, however, there should be a balance. What I suggestUse an array to store secrets instead of dictionary maybe a good direction. To security, if we have to use background page, maybe we can dispose all events when user close the popup page. |
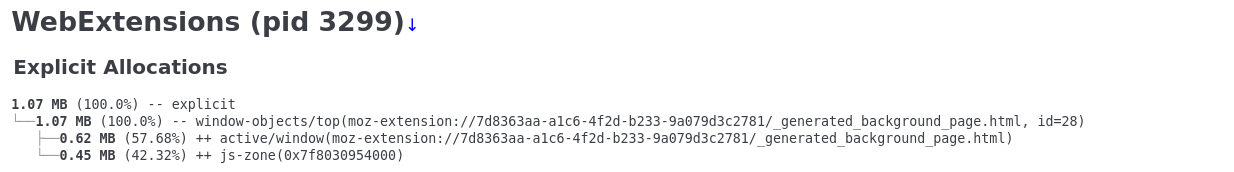
Secret hashingargon2 is only used to check the hash of Entries aren't hashed anymore and just get random identifiers (uuidv4) for their keys. It is unnecessary (and very slow with argon2) to hash individual entries as long as the Cost of using persistent background pageI profiled the background page's memory cost in Firefox. It uses somewhere between 1-2 MB. In a blank profile extensions normally use ~25 MB. In my normal profile extensions (not even counting normal web content) use between 120-250 MB. The memory cost low compared to other extensions already and is negligible compared to the security benefit this provides. Suggestions
Sounds like a good idea, this would let us move user config out of localstorage. Other than that, I don't really see that many reasons to move away from the current system. The secret hash problem should be solved by using uuids already.
If 1 MB of background page is too much, the alternative is to forget the user's password every time the popup page is closed. 1-2 MB really isn't that much for a web browser (mine is using over 0.5 GB right now!), and as long as we don't have the background page do too much it should be fine. |
This is the P1 feature we should have.
I checked that in Chrome Task manager, and it costs ~25MB, maybe Firefox can handle background better. If we can dispose the listener when popup is closed, it could be good. OK, then I think this PR is worth to merge, let's release it. |
I don't fully understand what you mean here. Am I understanding it correctly to mean set It looks like chrome dedicates an entire process for each extension. It brings in ~20 MB of runtime stuff. |
|
However, I have no idea how much benefit could we get from that if most memory is brought by runtime. |
Fixes #370, #366, and #387
Changes:
keycontains random key to encrypt entries with.keyis encrypted with password.keyis hashed with argon2 and is checked on password entry.entry.hashis now a random UUID. Entries hashes are changes when migrating tokeyformat and when changing password.