The alert notification generate a log message when an alert is triggered.
Perfect for example to record alerts as internal log messages in Graylog itself using the Internal Logs Input Plugin for Graylog. Thus you can create a stream to receive and manage alerts.
Also perfect for example to forward alerts via log messages to a Security Incident Response Platform.
Please also take note that if message field values are included in the log message template and these values vary based on the messages that triggered the alert, then multiple log messages may be generated per alert.
Alert example recorded as an internal log message:
| Plugin Version | Graylog Version |
|---|---|
| 6.1.x | 6.1.0 |
| 6.0.0 | 6.0.x |
| 5.1.x | >=5.1.9 |
| 5.0.x | 5.0.x |
| 4.3.x | 4.3.x |
| 4.2.x | 4.3.x |
| 4.1.x | 4.2.x |
| 4.0.x | 4.1.x |
| 2.2.x | 3.3.x |
| 2.1.x | 3.2.x |
| 2.0.x | 3.2.x |
| 1.3.x | 3.0.x |
| 1.2.x | 3.0.x |
| 1.1.x | 2.5.x |
| 1.0.x | 2.4.x |
Download the plugin
and place the .jar file in your Graylog plugin directory. The plugin directory
is the plugins/ folder relative from your graylog-server directory by default
and can be configured in your graylog.conf file.
Restart graylog-server and you are done.
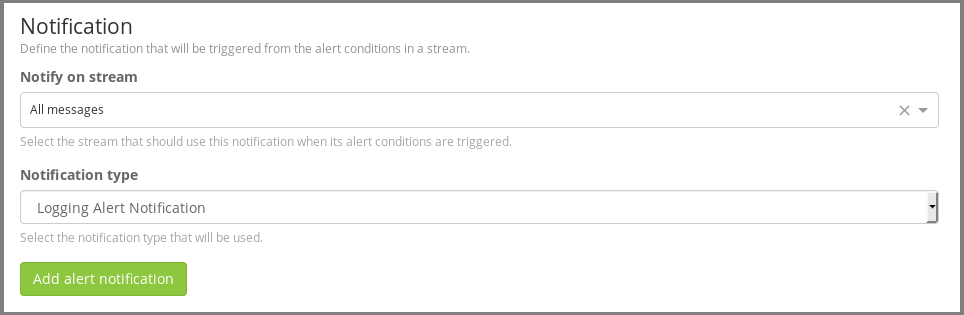
First you have to select Logging Alert Notification as the notification type.
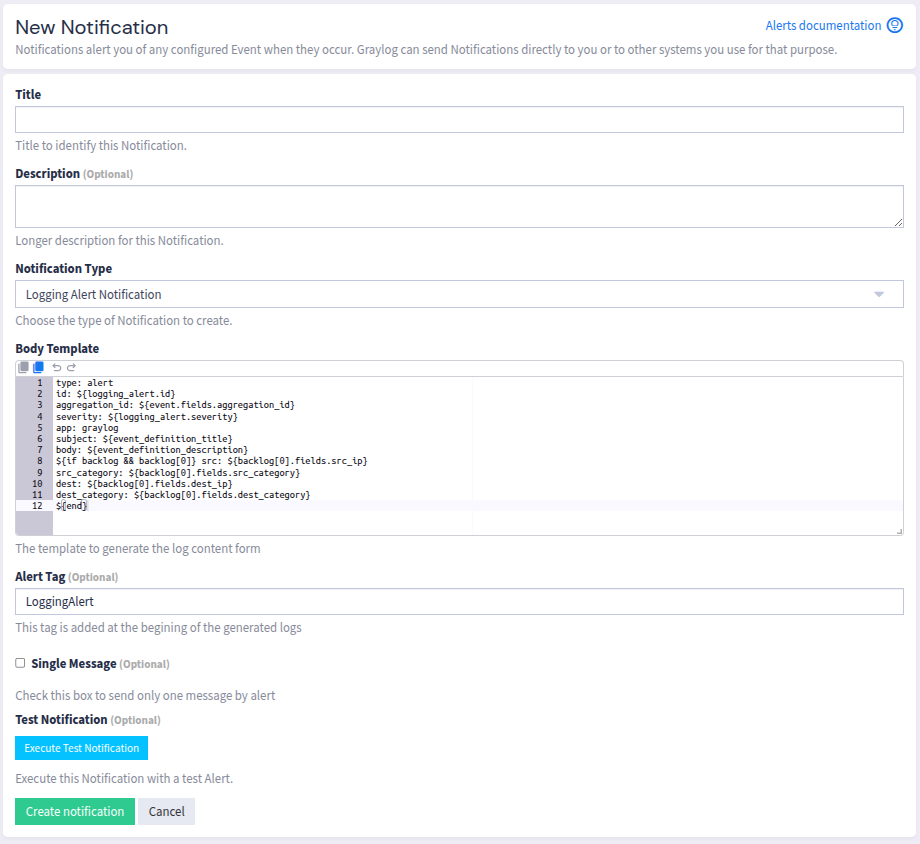
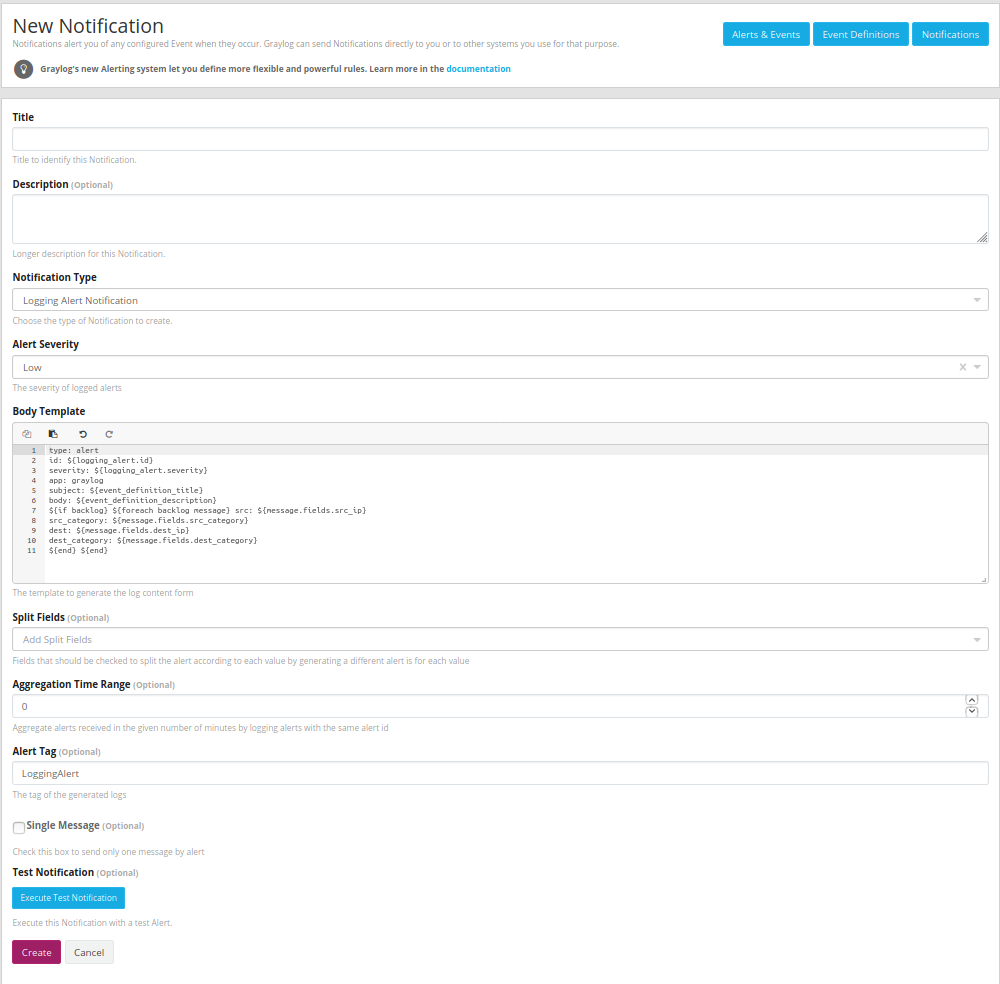
Then, in the popup that occurs, you can configure the Title of the notification.
You can configure the Alert Severity. You have the choice between 4 levels of severity.
You can also configure the Log Content to log the information you want. Please see the Graylog Documentation
Some plugin-specific fields values can be added to the log content.
| Plugin-specific Fields | Description |
|---|---|
| logging_alert.id | ID of the alert |
| logging_alert.severity | Severity of the alert |
| logging_alert.detect_time | Timestamp of the first message that triggered the alert |
| logging_alert.messages_url | URI to the retrieve messages that triggered the alert |
The parameter Split Fields allow you to split the alert based on message field values. Thus, a different alert id is generated for each value of one or more message fields.
The parameter Aggregation Time Range allow you to aggregate alerts received in the given number of minutes. Thus, the alerts are logged with the same alert id during the time range.
The parameter Single message allow you to sent only one notification by alert
You can optionally add any Comment about the configuration of the notification.
Make sure you also configured alert conditions for the stream so that the alerts are actually triggered.
Click on Configure in the System / Configurations section to update the plugin configuration.
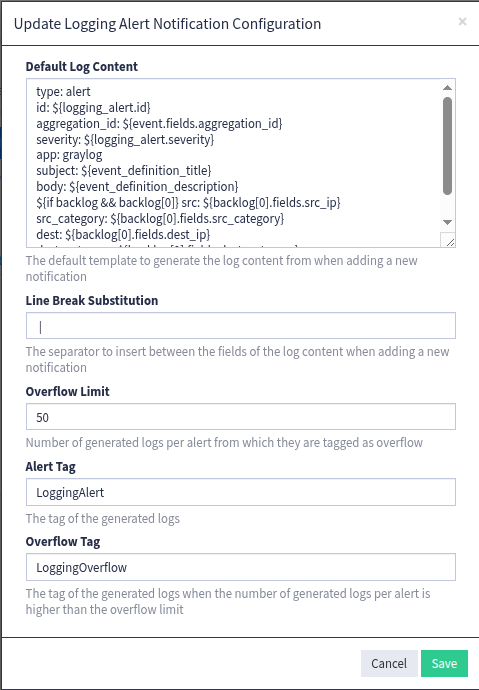
In the popup that occurs, you can configure the default value of the parameters that are set when adding a new notification: Default Alert Severity, Default Log Content and Default Aggregation Time Range.
You can define a Line Break Substitution of the log content in order to help parsing log fields and their values. Thus a separator can be inserted between the fields of the log content.
You can also configure the Alerts Stream. This stream must receive the log messages of alerts to enable the alert aggregation feature. Use the Internal Logs Input Plugin for Graylog for this purpose.
You can also set the Alert ID Field which is the field that is checked to get the alert id in the log messages of the Alerts Stream.
You can optionally define an Overflow Limit. From this given number of log messages per triggered alert, all the following log messages generated by the notification are tagged as overflow. This limit prevents you from forwarding too many log messages per alert to a Security Incident Response Platform by filtering the log messages according to their tag. For this purpose you can choose the name of the tags: Alert Tag and Overflow Tag.
This project requires Java 17 JDK.
- Clone this repository.
- Clone graylog2-server repository next to this repository.
- Build Graylog2-server with
./mvnw compile -DskipTests=true(in graylog2-server folder) - Run
./mvnw packageto build a JAR file (in this project folder). - Optional: Run
./mvnw org.vafer:jdeb:jdeband./mvnw rpm:rpmto create a DEB and RPM package respectively. - Copy generated JAR file in target directory to your Graylog plugin directory.
- Restart the Graylog.
A docker to build can be generated from Dockerfile.
This plugin is released under version 1 of the Server Side Public License (SSPL).