-
Notifications
You must be signed in to change notification settings - Fork 463
Adding create keys to tenant creation wizard #697
New issue
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and privacy statement. We’ll occasionally send you account related emails.
Already on GitHub? Sign in to your account
Conversation
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
Can you also change the title and description of the PR to better reflect what's being introduced and the task at hand?
portal-ui/src/screens/Console/Tenants/AddTenant/Steps/IdentityProvider.tsx
Outdated
Show resolved
Hide resolved
portal-ui/src/screens/Console/Tenants/AddTenant/Steps/IdentityProvider.tsx
Outdated
Show resolved
Hide resolved
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
Read comments above
| const ADGroupBaseDN = fields.identityProvider.ADGroupBaseDN; | ||
| const ADGroupSearchFilter = fields.identityProvider.ADGroupSearchFilter; | ||
| const ADNameAttribute = fields.identityProvider.ADNameAttribute; | ||
| const accesskeys = fields.identityProvider.accesskeys; |
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
Try to always use camel case variables:
| const accesskeys = fields.identityProvider.accesskeys; | |
| const accessKeys = fields.identityProvider.accesskeys; |
| const ADGroupSearchFilter = fields.identityProvider.ADGroupSearchFilter; | ||
| const ADNameAttribute = fields.identityProvider.ADNameAttribute; | ||
| const accesskeys = fields.identityProvider.accesskeys; | ||
| const secretkeys = fields.identityProvider.secretkeys; |
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
Same case:
| const secretkeys = fields.identityProvider.secretkeys; | |
| const secretKeys = fields.identityProvider.secretkeys; |
| interface IIdentityProviderProps { | ||
| classes: any; | ||
| idpSelection: string; | ||
| accesskeys: string[]; |
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
| accesskeys: string[]; | |
| accessKeys: string[]; |
| classes: any; | ||
| idpSelection: string; | ||
| accesskeys: string[]; | ||
| secretkeys: string[]; |
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
| secretkeys: string[]; | |
| secretKeys: string[]; |
| const IdentityProvider = ({ | ||
| classes, | ||
| idpSelection, | ||
| accesskeys, |
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
| accesskeys, | |
| accessKeys, |
| classes, | ||
| idpSelection, | ||
| accesskeys, | ||
| secretkeys, |
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
| secretkeys, | |
| secretKeys, |
| key={`csv-secretkey-${index.toString()}`} | ||
| /> | ||
| </div> | ||
| <button |
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
Please try to use the component from material-ui, you can see examples in the create tenants files
| MinIO supports both OpenID and Active Directory | ||
| </Grid> | ||
|
|
||
| <button |
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
Same case with button
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
Also please remember to do make assets
17224a8 to
ed8a562
Compare
e5d093a to
b0939be
Compare
restapi/admin_tenants.go
Outdated
| if err != nil { | ||
| return nil, prepareError(errorGeneric, nil, err) | ||
| } | ||
| minInst.Spec.Users = []*corev1.LocalObjectReference{{Name: consoleUserSecretName}} |
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
Existing code here will create an additional user in MinIO, we need to discuss whats the desired behavior because if the user decided to add, lets say, 5 users via the create tenant wizard he will ned having 6 users on his system and I'm sure he will ask why
| if len(tenantReq.Idp.Keys) > 0 { | ||
| minInst.Spec.Users = users | ||
| } |
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
What is this variable assignation happening here? I see below we are iterating over tenantReq.Idp.Keys and assigning more objects to minInst.Spec.Users
restapi/admin_tenants.go
Outdated
| if len(tenantReq.Idp.Keys) > 0 { | ||
| for i := 0; i < len(tenantReq.Idp.Keys); i++ { | ||
| userSecretName := fmt.Sprintf("%s-%d-user-secret", tenantName, i) | ||
| userSecretData := map[string][]byte{ | ||
| "CONSOLE_ACCESS_KEY": []byte(*tenantReq.Idp.Keys[i].AccessKey), | ||
| "CONSOLE_SECRET_KEY": []byte(*tenantReq.Idp.Keys[i].SecretKey), | ||
| } | ||
| _, err := createOrReplaceSecrets(ctx, &k8sClient, ns, []tenantSecret{{Name: userSecretName, Content: userSecretData}}, tenantName) | ||
| if err != nil { | ||
| return nil, prepareError(errorGeneric, nil, err) | ||
| } | ||
| minInst.Spec.Users = append(minInst.Spec.Users, &corev1.LocalObjectReference{Name: userSecretName}) | ||
| } | ||
|
|
||
| } |
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
Is this repeated code? I think we already iterate over all tenantReq.Idp.Keys, created k8s and populated the users array in line 577
| "CONSOLE_SECRET_KEY": []byte(*tenantReq.Idp.Keys[i].SecretKey), | ||
| }, | ||
| } | ||
| _, err := clientSet.CoreV1().Secrets(ns).Create(ctx, &instanceSecret, metav1.CreateOptions{}) |
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
You can use the createOrReplaceSecrets function here
|
can you also do |
|
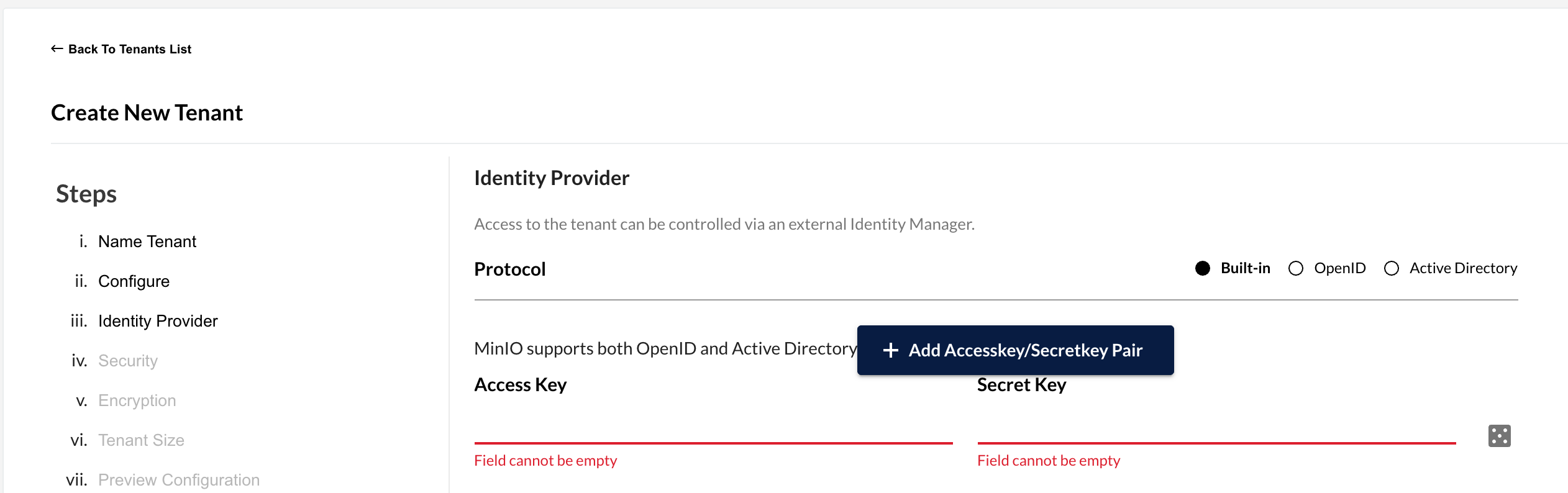
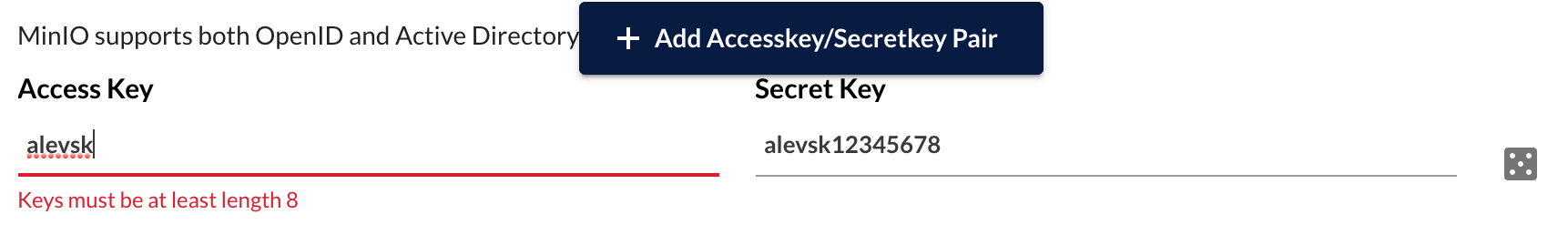
I tested this PR creating 3 users with short names like Please introduce a restriction on the UI to ensure the user and password are at least 8 characters long |
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
Please fix conflicts
57c9dcd to
d004f7d
Compare
| error={validationErrors[`secretkey-${index.toString()}`] || ""} | ||
| /> | ||
| </div> | ||
| <Button |
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
Please try to place this button as an icon in the secret key, please look for examples of overlayIcon in InputBoxWrapper component
c7196d1 to
300a737
Compare
Signed-off-by: Adam Stafford <adam@minio.io>
42b1971 to
5c42455
Compare
|
I think length policy only applies to secret key, access key can be less than 8 characters (via |
No description provided.