-
Notifications
You must be signed in to change notification settings - Fork 2.8k
Description
Describe the bug
根据 Netmanias 对于 RFC 3489 与 STUN (RFC 5389/5780) 的对比解读,NAT 类型对应关系如下(绿色为 Mapping Behavior,蓝色为 Filtering Behavior):
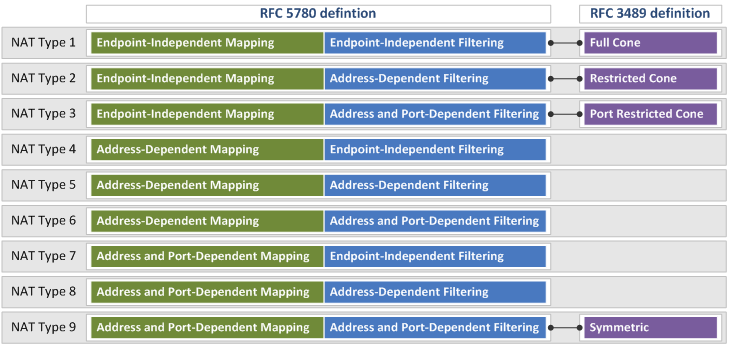
Netch 在检测 NAT 类型时采用了 RFC 5780 规范,最终显示结果遵循 RFC 3489 规范,但没有正确对应两种规范的 NAT 类型。
举例见 Log 章节。
To Reproduce
Steps to reproduce the behavior:
- Open Netch
- Connect to a Server with non-standard RFC 3489 NAT type
- See the NAT Type Indicator at right bottom corner
Log
Example 1
Other address is (hidden)
Binding test: Success
Local address: (hidden)
Mapped address: (hidden)
Nat mapping behavior: EndpointIndependent
Nat filtering behavior: AddressAndPortDependent
result: 4
参照上图,此处的 NAT 类型应为 3,即 Port-Restricted Cone NAT (RFC 3489),而 Netch 报告为 4.
Example 2
Other address is (hidden)
Binding test: Success
Local address: (hidden)
Mapped address: (hidden)
Nat mapping behavior: AddressAndPortDependent
Nat filtering behavior: EndpointIndependent
result: 2
参照上图,此处的 NAT 类型并不能在 RFC 3489 规范中找到正确对应,而 Netch 报告为 2.
Screenshots
Not Needed.
Environment (please complete the following information):
- OS: Windows 10 Enterprise LTSC 2019 (1809)
- Netch Version: 1.7.2
Additional context
(Empty)